The growing cybersecurity threats pose risks to patient safety and data privacy, leading regulatory bodies such as the FDA to enforce strict security measures. The FDA recently introduced new regulations to enhance medical device testing, aligning with global quality standards like ISO 13485:2016.
This update aims to improve medical device quality and safety, simplify market access for U.S. manufacturers, and integrate devices into global healthcare systems. Compliance with these regulations requires significant investment in cybersecurity measures and activities, leading to device redesign to meet the new standards.
A security risk assessment for medical devices is not merely a checklist item; it is a critical component of modern healthcare cybersecurity that aims to prevent these devices from becoming gateways for cyberattacks. It ensures that technology in patient care does not become a target for cyber attacks. This process systematically identifies and resolves vulnerabilities in medical devices that could be exploited in the growing Internet of Things (IoT) environment.
This assessment guarantees the long-term safety of the devices and is a vital aspect of post-market management. Healthcare providers also benefit from this assessment as it allows them to confirm that the medical devices they use do not have any vulnerabilities that could harm healthcare services, patient well-being, or data privacy.
Common types of medical device security audits include:
FDA Audits
Internal Audits
Audits by EU Notified Bodies
Audits by Regulators and Certifying Bodies
Modern healthcare industry utilizes a wide range of medical devices such as insulin pumps and advanced MRI machines. These devices are now interconnected and have become smarter, making them more susceptible to security risks.
Health systems, along with their business connections and diverse staff, handle and store a large amount of sensitive healthcare data. This data is attractive to cyber attackers because of its value on the black market.
A security breach has the potential to result in patient data being compromised, interruptions in healthcare services, and extreme situations, pose a direct risk to patient health. Due to the critical nature of these systems, it is essential to regularly perform comprehensive security audits to safeguard the confidentiality and reliability of patient data and healthcare offerings.
This process involves simulating cyberattacks on medical devices and their support systems to identify vulnerabilities, such as weak encryption and insufficient access controls, that could be exploited by malicious actors. Penetration testers use various techniques specific to the healthcare environment, including exploiting software flaws, bypassing physical security measures, and testing devices’ resilience to social engineering. The goal is to document these vulnerabilities thoroughly to strategize corrective actions.
For more insights, read: What Is Penetration Test and Why Do You Need it?
Vulnerability scanning is an automated process created specifically for medical devices and their related systems. It helps in finding known security issues by using databases like the Common Vulnerabilities and Exposures (CVE) database. This method is broader and less focused compared to penetration testing, yet it plays a crucial role in constantly checking and improving the security of medical equipment.
For thorough understanding, read our blog: Vulnerability Assessment vs Penetration Testing.
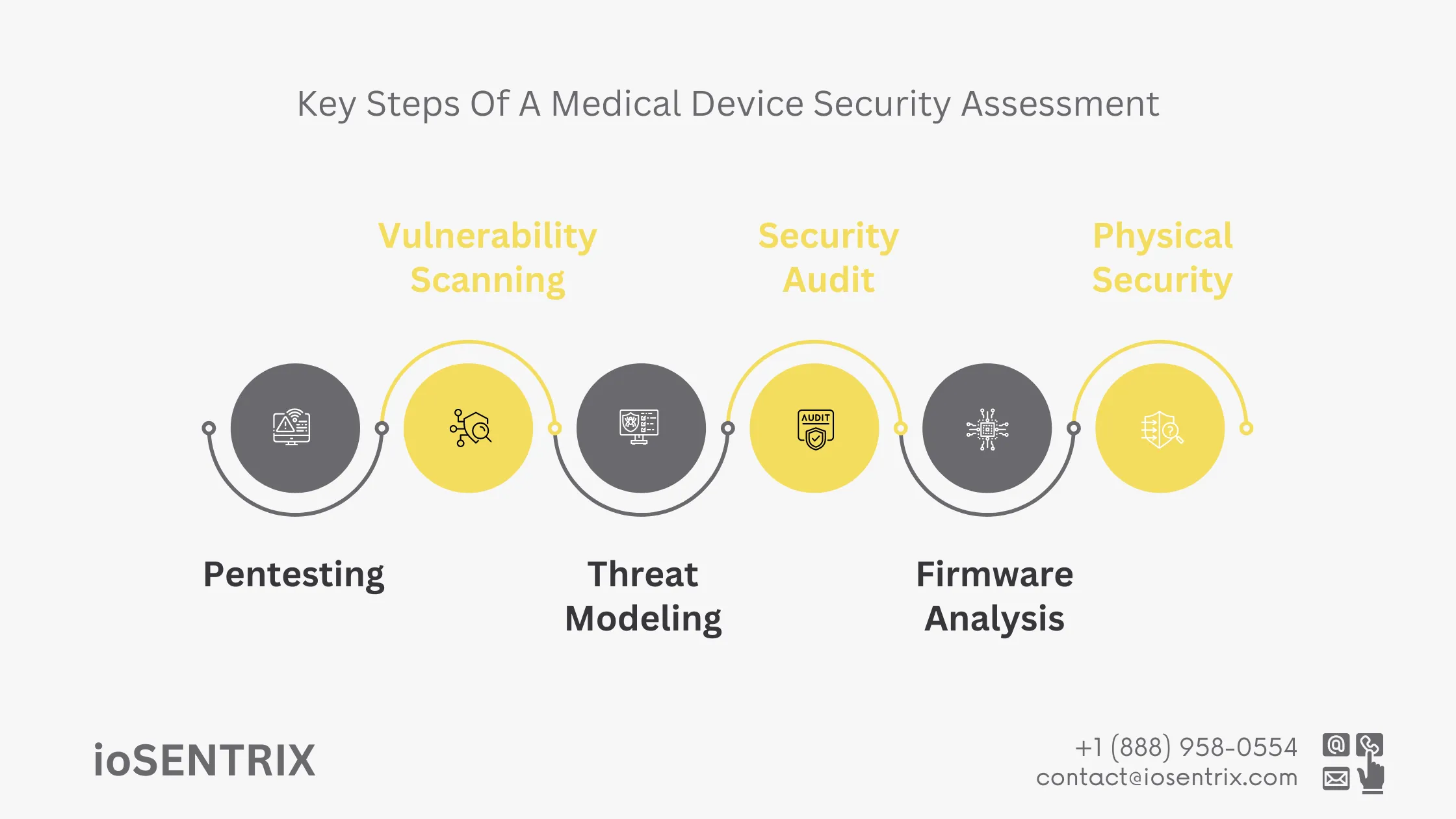
Threat modeling for medical devices involves identifying potential attackers, their objectives, and the methods they could use to compromise device security. This strategic process helps map out risks and align security measures with the most serious threats.
Security audits in the medical device sector involve a comprehensive review of the security framework and policies governing a device. Compliance checks ensure adherence to relevant regulations, such as those set by the FDA. These audits often include detailed assessments of documentation, security protocols, and incident response plans to verify their adequacy and effectiveness. Through these efforts, medical devices not only meet regulatory requirements but also follow best practices in cybersecurity.
Reviewing the source code of a medical device’s firmware can reveal vulnerabilities that may not surface during other testing processes. This analysis examines the firmware for issues such as binary flaws or reverse engineering weaknesses that could compromise the device’s security.
Read more on: Navigating FDA Cybersecurity: Essential Guidelines for Healthcare Product Manufacturers.
Physical security testing evaluates the device’s resistance to invaded and unauthorized access. This is especially important for devices used in public or semi-public areas, like medical kiosks or wearable health devices. Ensuring that physical controls are in place helps prevent unauthorized tampering, and this testing must be ongoing to adapt to emerging threats and changes in the device’s environment.
The critical importance of these assessments has been demonstrated in past cyberattacks on the healthcare sector. For instance, the 2017 WannaCry ransomware attack affected healthcare systems worldwide, disabling numerous medical devices. Additionally, nearly half a million pacemakers were recalled in 2017 due to security vulnerabilities that allowed unauthorized access to the device’s settings, putting patients at serious risk.
Recognizing the importance of security assessments for medical devices leads to a discussion on regulatory compliance. This discussion emphasizes how the FDA’s updated requirements aim to strengthen this vital link.
Key components of the FDA’s Updated Regulations include:
The FDA requires manufacturers to carefully consider cybersecurity when creating medical devices. They must conduct thorough risk assessments to find any possible weaknesses and take steps to reduce these risks before selling the devices.
The FDA mandates ongoing monitoring of medical devices for new risks. Manufacturers must have structured plans in place to address security issues throughout the device’s lifecycle, including timely software updates and patches.
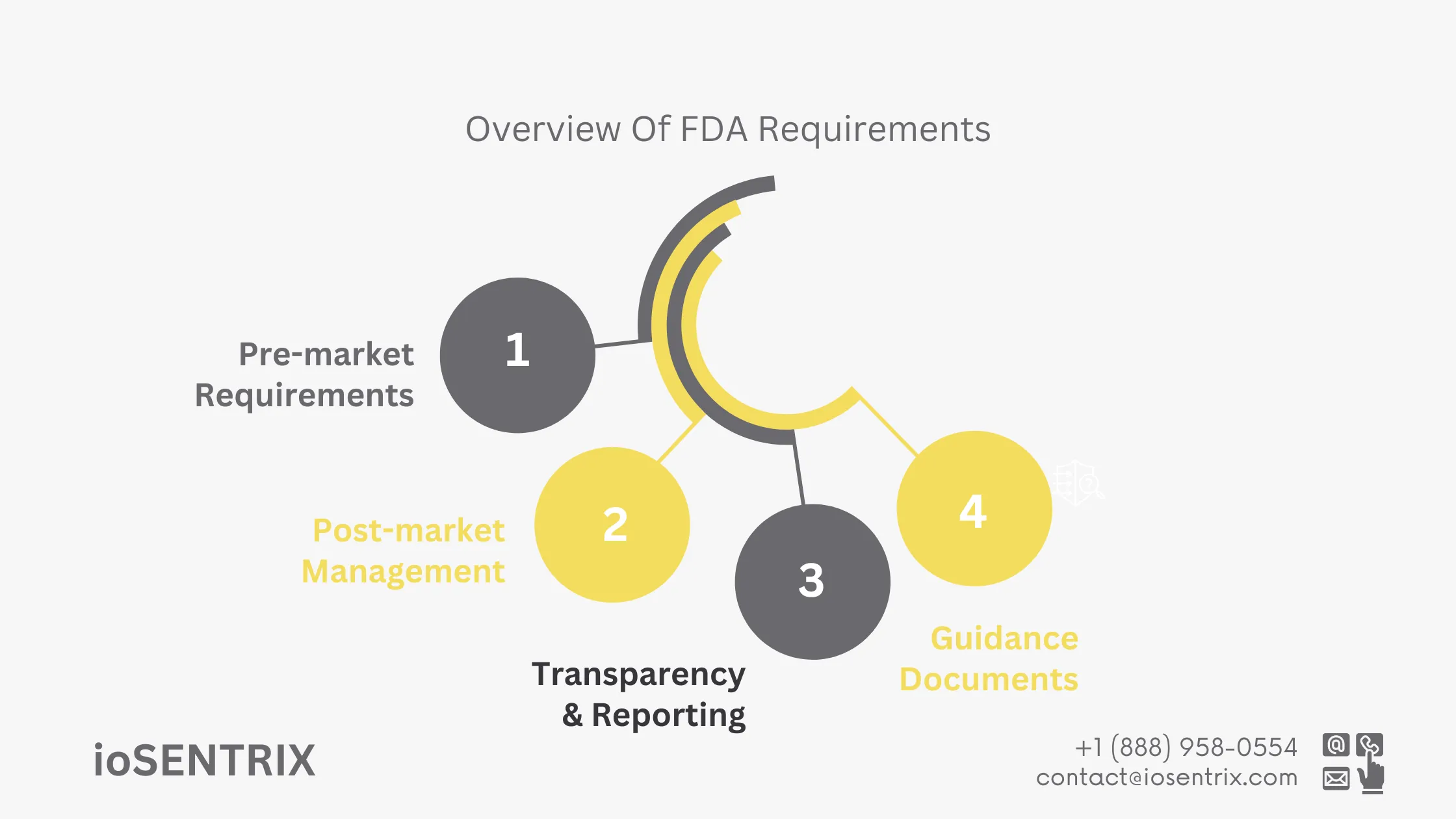
The FDA emphasizes the importance of open communication with regulators and stakeholders. Manufacturers are obligated to report significant cybersecurity incidents promptly and work with the healthcare community to manage and mitigate these risks.
The FDA has issued guidance documents to help manufacturers comply with cybersecurity requirements. These resources provide best practices for premarket submissions, post-market management, and handling cybersecurity incidents.
Several high-profile cybersecurity incidents underscore the need for strong security assessments in healthcare. These breaches have exposed vulnerabilities in medical devices. One alarming case involved hospital infusion pumps, where hackers infiltrated the network and manipulated dosage controls, putting patient safety at serious risk. This incident highlighted the life-threatening consequences of cyberattacks on medical devices and underscored the urgency for comprehensive security measures.
The FDA’s adoption of ISO 13485:2016 reflects its commitment to strengthen cybersecurity for medical devices. Manufacturers must incorporate security measures from design through post-market stages and continuously monitor for emerging vulnerabilities. Comprehensive security assessments like penetration testing and vulnerability scanning are fundamental in preventing cyber threats from compromising patient safety. The future of medical device security depends on adherence to these standards and proactive risk management strategies.
ioSNETRIX offers pentesting services for the healthcare industry that assist manufacturers in complying with FDA regulations and addressing cybersecurity issues. Through simulating cyberattacks, ioSENTRIX identifies vulnerabilities and addresses them to prevent any threats to patient safety. These services help manufacturers meet regulatory standards and improve the security of their devices.