What is phishing? How to recognize and report phishing emails?

The cybersecurity industry has seen massive growth in social engineering, especially phishing attacks, over the last few years. The recently published DBIR report in May 2021 has shared an 11% increased ratio of phishing attacks in the first quarter of 2021. Whereas, in 2020, the overall data breaches and cyber-attack reported had 25% of phishing scam involvement.
In this blog post, we have shared some of the common phishing attack types along with a brief guide to recognize and report phishing attacks to prevent oneself from being a phishers’ target.
What is a phishing attack?
A phishing attack is one of the deceptive techniques of social engineering that threat actors or cybercriminals use to manipulate people and users to take out sensitive information such as personal identifiable information (PII), financial information, trade secrets, account credentials that could help them (attackers) gaining access to sensitive assets or bypass security controls.
The phishing attack is typically performed through emails. The attacker impersonates a trusted and reliable source in the email and psychologically tricks the users into trusting him to share information and help him achieve the desired operation.
Why do phishing emails work?
Phishing emails involve fake news or scenarios to gain victim trust. It also involves downloadable attachments forged with malicious software or URL redirecting the user to a spammy website, which once opened or clicked install malware to steal data or compromise the user’s system.
To know why phishing attacks work, it is necessary to understand the user’s motivation and behaviors from a psychological perspective because this is the main factor that helps phishers compromise security countermeasures through a planned yet simple phishing email.
Cybercriminals use the human psychology element as a phishing attack tool. They target psychological phenomena to exploit vulnerable minds instead of technology, system, network, etc. We, humans, are full of emotions, fears, curiosity, anxiety, and our brain is designed to handle such emotions along with social interaction. Oftentimes, our fears, excitements, and emotions take control over us and leverage the attacker to deceive us.
Generally, a phishing attack utilizes the six principles of persuasion, such as reciprocity, consistency, validation, scarcity, social proof, and liking, etc., to use human sentiments as an effective phishing scheme. Depending upon the phisher’s intention, the email might contain all or any one of the principles.
What is the purpose of phishing attacks?
The phishing attack deliverables vary from phishers’ goals and approaches. However, in general, phishing involves the following purposes.
Sensitive information collection
Phishers target employees and average users to gather sensitive information such as email addresses, business data or secrets, bank account information or credentials, and other personal identifiable information (PII). Subject to the attackers’ goals, they can use the information to compromise accounts for data or money theft, identity fraud, etc.
Downloading malicious software (malware)
This scheme is popular among phishing attacks targeting big or small enterprises and corporations. In it, the attackers attach forged or malware-infected files in the email. Once the file is opened, it downloads the malware and establishes communication with command and control (C2C) servers to facilitate attackers in gaining system access and persistence.
Ransomware
Cybercriminals also use phishing attacks as a tool for ransomware. They deploy trojans and viruses in the email attachment or as a spammy website forged URL that once clicked, install malware to encrypt and restrict the data accessibility until the ransom is paid. In addition, cybercriminals often steal the data to sell on the dark web if the company refuses to pay for ransomware.
What are the types of phishing attacks?
There are various types and approaches that attackers use to execute phishing scams. Some of the popular phishing attack types are:
Spear phishing
Spear phishing attacks are centered on specific recipients or individuals linked to or within any organization or group. Unlike simple phishing emails which randomly target employees or users, spear phishing is focused on the victim.
In it, the attacker closely researches its object (i.e.individual or employee) and executes the phishing email sophisticatedly, typically pretending to be the mutual or most reliable source to gain user trust and involve the recipient in giving out sensitive information along with bypassing phishing filters and other security countermeasures.
Vishing
For vishing attacks, cybercriminals use voice email, landline, smartphone, or VoIP technology to reach their targets over the call. In it, the attacker pretends to be from reputable or authoritative sources such as customer service representatives, banks, technical support, company management, etc., to trap the called person in conversation and psychologically trick them into giving up sensitive information.
SMShing
SMShing relies on SMS and text messages as a primary phishing attack vector. By working on the same phishing phenomena, the attacker sends out deceptive messages to grasp the receiver’s attention by pretending to be from a reliable source and convinces them to provide sensitive information such as account credentials, MFA (Multi-factor authentication) codes, click over the URL, etc. It is also often time well-crafted messages that engage the receiver and push them forward the same messages to their contacts.
How to recognize phishing emails?
Phishing is a wide-spanning attack, and most of the time, phishing emails slip through the security solutions. Cybercriminals do not crack the technological flaws in the phishing campaign; instead, they look for the gap in the human mind. As a result, they create campaigns to look convincing as possible.
Still, if you train your mind with security awareness and making informed decisions, you can recognize the phishing scam with tell-tale signs of email. Consequently, the knowledge and common cybersecurity sense would help you upguard the defenses against phishing emails.
Following are the typical signs you can look for to spot phishing emails.

Public, Unicode, or Typo-squatted Domain
The first thing you must notice whenever you receive any email is the domain. To trap people, the attacker uses public, Unicode, or Punycode domains to launch Internationalized domain name (IDN) homograph attacks.
Unicode renders the text expressions of different countries’ written languages and makes it possible to register a domain with foreign characters that, in general, look similar to ASCII characters, i.e., the English alphabet. Cybercriminals take advantage of similar characters of different languages and incorporate them into the domains to spoof the users. Along with it, they leverage in attack preparation by buying typo squatted or similar domains.
Whenever you receive an email from any domain, see the domain first and check out its credibility. To verify the credibility, look closely at the domain and see if there is an interchangeable letter or spelling mistake. So often, we look over the spelling mistakes and read the word as we are used to reading, such as google to googIe, payoneer to payoner, yandex to yandax, etc.
Email Content
Once you are done verifying the domain legitimacy, read the email content. Notice the following thing closely
- Is the email poorly written and has grammar mistakes?
- Does the email have any attachments or URLs?
- Does email show any unnecessary urgency in its content?
- Does email claim any offer?
- Is the sender asking for any information or money?
If the received email has any of the mentioned things, stop yourself from opening any attachment or reply; instead, analyze all of the items individually.
Poor email content
Most of the time, phishing emails are sent out in bulk; thus, grammar is often overlooked. Whenever you receive an email from any source, check the email content whether the sender knows your name or calling you with generic terms like Sir, Madam, Dear customer, etc. Such common details greatly help in identifying legitimate and fake emails.
Attachment or URL
If your email has any document, image, or URL, it is highly likely to be forged with malicious software or a backdoor. Before clicking on the link, hover your mouse over it to check where the link redirects you. Similarly, prior to opening any attachment, scan it with any anti-virus software such as Virus Total.
Unnecessary urgency
It’s human nature to freak out in case of an emergency, and it is what phishers take advantage of. As phishing attacks always come from a seem-legitimate source, the attacker targets the victim with an urgent reply or action requirement. If you receive an email with the call to action that you think can be real, contact the person directly to confirm it or verify the legitimacy from another source.
Offer
Remember, it is the most common practice of phishers to fool users with exciting offers and benefits. They usually do so by sending your proposal or offer along with the URL and asking you to fill out a form or register to the website to utilize offers.
Asking for information or money
Phishers go after the user for money. They get it either through direct demand or by holding on to sensitive information or assets as a hostage—both ways, they take the money. Beware of any email asking you to initiate the payment, transfer fund, or account credentials. Nevertheless, it may be possible you get an email from a legitimate but compromised account. In such a case, it is important to cross-check the necessity of payment or account details through a call, in-person, or other mutual sources.
Since the covid-19, the world has witnessed an extensive rise in phishing campaigns. Learn more about the common covid-19 phishing scams.
Examples of phishing email
Sample 1
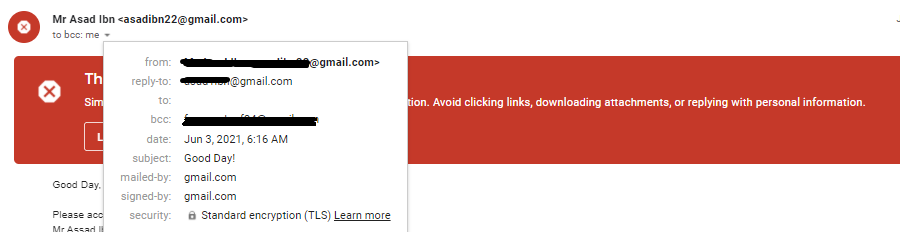
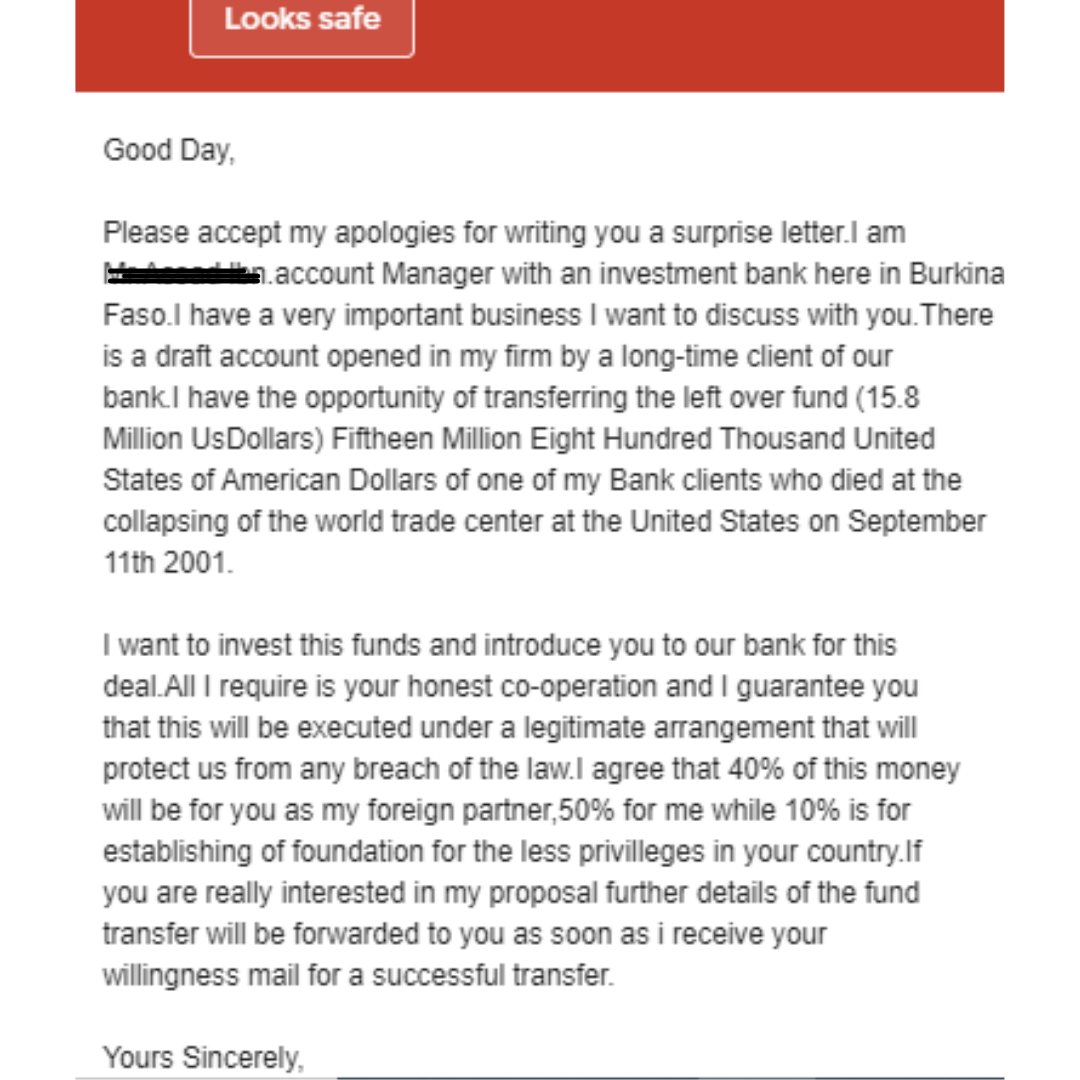
In email 1, If we look closely at the email recipient address, we do not see any fake or public domain, nor the email has any URL or downloadable attachment.
In such cases, when there is no attached file or URL and suspicious email domain, we must pay attention to the email content i,e, how is it written, how the sender is calling the email receiver, is it generic email, have grammar mistakes, or not, does it look professional or spammy, etc.
So, in this email, we can notice flawed content quickly. The very first thing is that the sender does not call the recipient with their name. It is a phishing sign that the phisher might send out an email randomly. In addition, the email content does not look or close to a professional email and has multiple grammar and formatting mistakes. Lastly, it throws out unnecessary as well as suspicious offers/proposals.
Therefore, with all the indicated behavior, we can call this email a phishing scam.
Sample 2
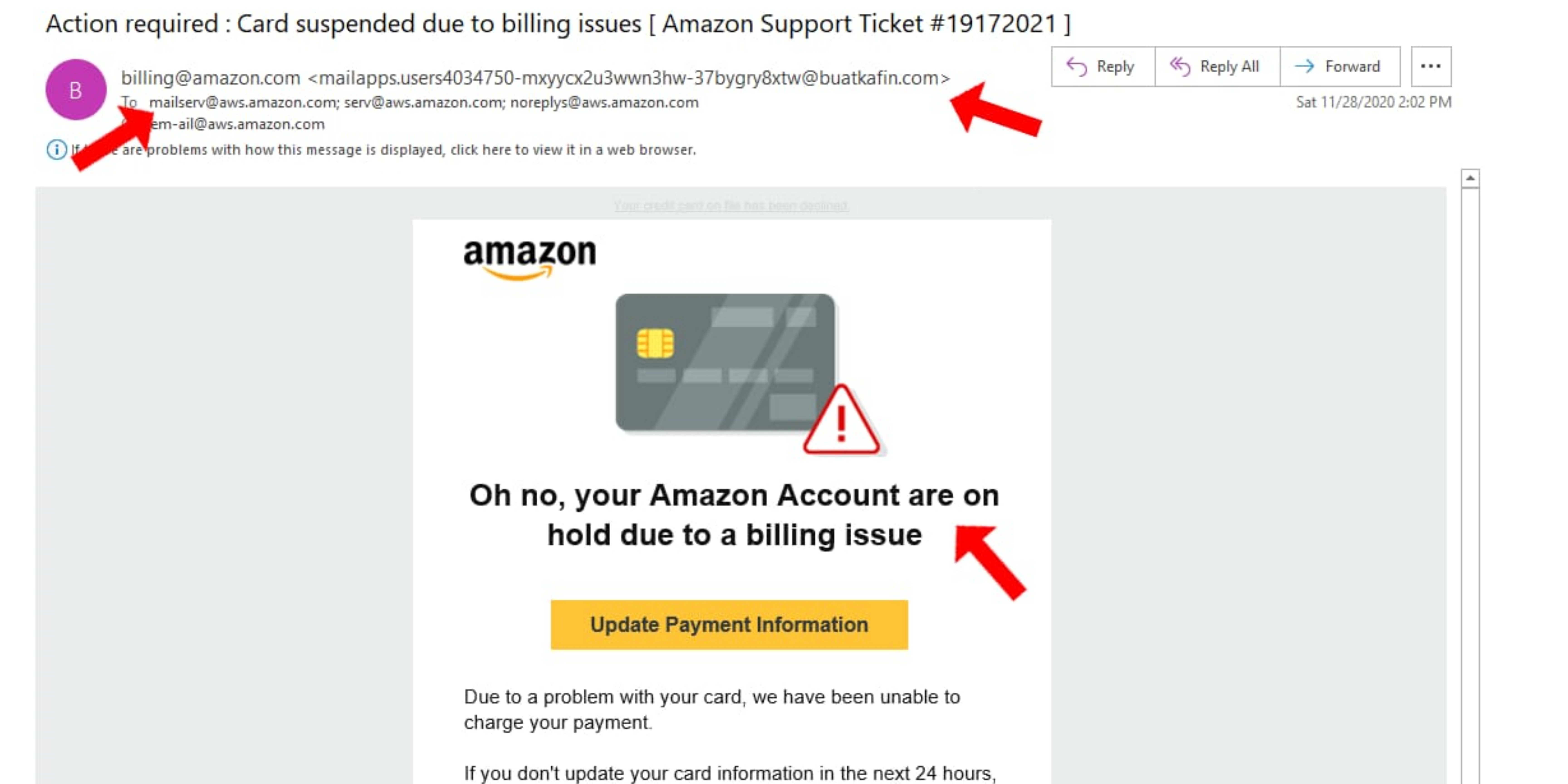 In this email, we have multiple phishing signs that we can easily spot.
In this email, we have multiple phishing signs that we can easily spot.
First, the email claims to be from billing@amazon.com; however, if we look closely, the actual email domain is “buatkafin.com.” Furthermore, unusual alerts and suspicious notifications are the most used phisher’s tricks to grab user attention in order to force them to click a redirected URL or download an attachment.
The same trick is used by the phisher in this email. Again, he sent an alert email to grasp the subscriber’s attention by creating a sense of urgency to update payment and card information within 24 hours.
Usually, with such emails, users fret out and click over the mentioned URL to revise their information that, in reality, is forged with malware that could later encrypt and steal the system data, lock files or install backdoors.
How to protect yourself from phishing attacks?
The best way to prevent phishing is to hold basic cybersecurity knowledge, make informed decisions, and remain updated on the latest attack trend. With a security-aware mindset, people and organizations can significantly avoid phishing and protect themselves.
Other than that, the following key points can help you to prevent phishing attacks.
- Enforce multi-factor authentication on your all accounts
- Hide unnecessary information from social networking sites
- Do not share your sensitive information such as name, address, email address, phone number, date of birth, passwords, banking information with anyone without verification and absolute necessary circumstances
- Use dummy emails to hide your identity and prevent your real emails from being exposed in breaches
- Use an ad-blocker to stay away from online activity
- Use VPN to hide your IP address, location, and internet connectivity
- Keep operating system and applications updated
- Use anti-virus and anti-malware products/software
What to do if you respond to a phishing email?
We are all human, and we all make mistakes. However, in such cases, when you become a victim of a phishing attack, you must take the following steps as soon as possible to avoid the aftermath.
- Change your account credentials and if you use the same passwords on all accounts, change them too.
- Beware your colleagues, friends, and family from accepting any offer, attachment, etc. from your account
- Run Antivirus and anti-malware scan
- Notify your bank and block transactions in case of fund transfer
- Notify your company’s IT team, if your corporate credentials are shared or stolen
- If you have shared your business information, alert your concerning authorities
How to report phishing emails?
Phishing attacks have become a universal concern all around the globe. It is now essential that you play your part in combating phishers and cybercriminals by reporting phishing emails and online scams to the concerned authorities. If you have received any phishing call, email, message, or become a victim to one, you should report it immediately. In the United States, you can report them to
- FTC
- Anti-Phishing Working Group (APWG)
- FBI’s Internet Crime Complaint Center (IC3)
- US-CERT.gov
- SSA.gov
- PhishTank
Organizations and individuals must be wary of cybercriminals targeting them with phishing emails. Often, such emails get passed from spam filters due to advanced tactics; therefore, employees need to be aware of evolving techniques. Whether you want to educate your staff or run an assessment to test their security awareness. Call us today; we offer social engineering assessments, including phishing campaigns. Our services are comprehensive, fast, reliable, and won’t break your bank.
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter