
Modern software teams are under significant pressure to ship fast while maintaining strong security practices.
With the rise of DevSecOps, organizations are evaluating which testing methods offer the best vulnerability coverage, lowest false positives, and highest return on investment (ROI).
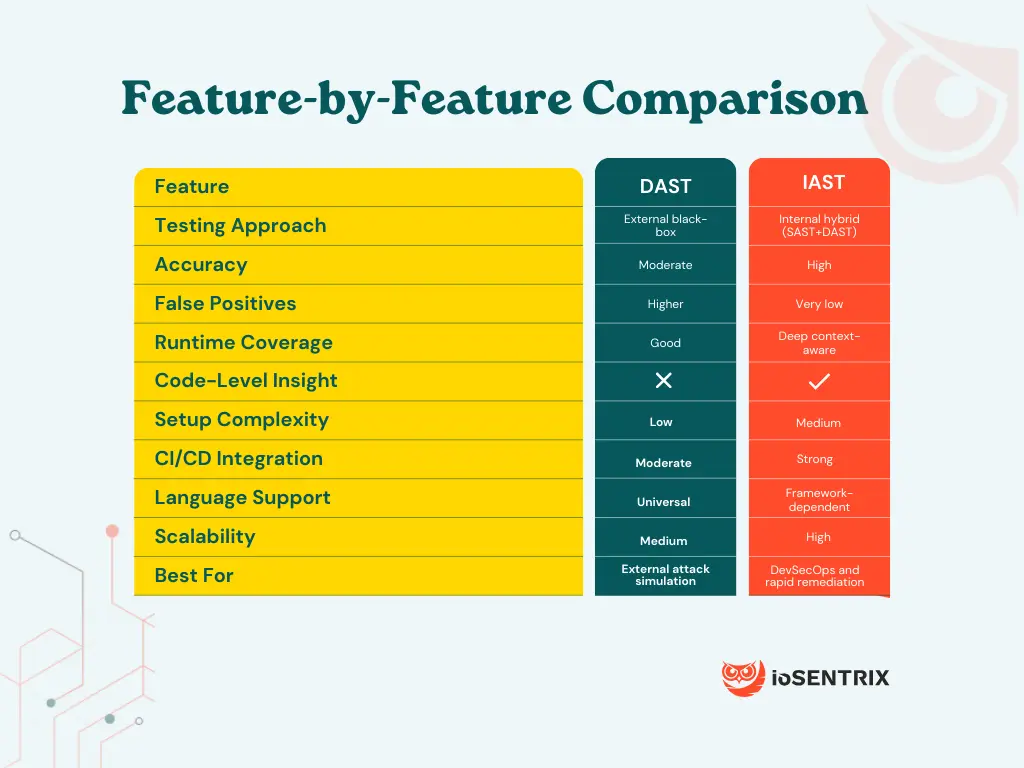
Two of the most commonly compared approaches are Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST).
This article provides a detailed, unbiased, and research-backed comparison to help you determine which tool delivers stronger ROI for your application security program.
DAST is a black-box testing methodology that examines a running application from the outside, mirroring the behavior of an attacker.
The tool interacts with the deployed application, typically in a staging or test environment, and sends crafted payloads to identify vulnerabilities exploitable at runtime.
This includes issues such as SQL injection, cross-site scripting, insecure authentication flows, and server misconfigurations.
DAST crawls pages, analyzes responses, and attempts to exploit weaknesses without any insight into the internal code or logic.
Because it operates externally, DAST can assess applications regardless of programming language, framework, or architecture, making it particularly useful for heterogeneous environments.
DAST’s primary advantage lies in its ability to detect vulnerabilities exactly as an attacker would encounter them. This makes it valuable for evaluating production-like configurations that may not be visible through static or code-level testing.
It is also language-agnostic, easy to deploy, and aligns well with compliance-driven requirements such as OWASP Top 10 assessments.
You may want to read: SAST vs. DAST: What's the Difference?
IAST is a hybrid testing approach that combines elements of SAST and DAST to deliver real-time, context-rich vulnerability detection.
It operates by installing agents or sensors inside the application runtime. As the application is exercised, the IAST agent monitors data flows, function calls, and request handling to identify vulnerabilities with code-level precision.
The IAST agent continuously observes the application from within, capturing detailed insights into how data moves through the system. This enables it to detect vulnerabilities such as insecure data validation, flawed authentication logic, or misconfigurations that may not be visible from outside.
Because IAST analyzes the application dynamically while understanding its internal structure, it provides more accurate results and deep coverage across the runtime environment.
Its contextual awareness allows it to pinpoint vulnerabilities down to specific lines of code, which dramatically reduces developer triage time.
IAST operates quickly and continuously, making it ideal for integration into modern CI/CD pipelines. It also adapts well to microservices, APIs, and distributed cloud environments where runtime insights are essential.
DAST generally requires a smaller upfront investment because it does not involve instrumentation or integration with the internal application environment.
In contrast, IAST may require higher initial setup costs due to agent deployment and compatible infrastructure.
However, the long-term financial impact often favors IAST, as it reduces manual triage and accelerates vulnerability remediation.
DAST is effective at uncovering externally exploitable issues but often struggles with accuracy due to limited internal visibility. This limitation leads to additional validation efforts by security teams.
IAST, on the other hand, delivers highly accurate and contextualized findings because it analyzes the application from within.
Its ability to identify logic-level vulnerabilities and trace them to specific code segments significantly reduces the time developers spend troubleshooting issues.
DAST typically enters the development lifecycle later, often during staging or pre-production phases. This timing increases the cost of remediation, as vulnerabilities discovered late are more expensive to fix.
IAST integrates seamlessly into CI/CD workflows, enabling teams to detect vulnerabilities early when fixes are easier and more cost-effective.
Organizations using IAST often experience shorter release cycles and fewer security-related bottlenecks.
When evaluated over a multi-quarter or multi-year horizon, IAST usually emerges as the more cost-effective approach.
Its lower false positives, reduced manual triage, fewer production vulnerabilities, and improved developer velocity result in substantial operational savings.
While DAST contributes to external risk reduction, IAST improves both security and engineering efficiency, yielding a stronger cumulative ROI.
IAST generally delivers better ROI for organizations that prioritize continuous testing, rapid development cycles, and high accuracy.
It is particularly valuable for teams seeking to reduce noise, accelerate fixes, and enhance developer productivity.
DAST, however, still provides high value for scenarios where external attack simulation is required or where technology stacks are too diverse for agent-based monitoring.
For most mature DevSecOps programs, the optimal solution is a hybrid approach where IAST handles early and mid-SDLC detection, and DAST validates external exposure before release.
Organizations handling customer-facing applications, regulated industries, or complex microservice ecosystems often benefit from deploying both testing methods.
IAST provides deep contextual insights and catches vulnerabilities early, while DAST offers an external perspective that aligns with real-world threat scenarios.
Together, they deliver full-spectrum coverage of both internal logic flaws and externally exploitable weaknesses, resulting in a stronger overall security posture.
DAST strengthens external security visibility, while IAST enhances internal detection accuracy and accelerates remediation.
For most organizations, particularly those practicing DevSecOps, IAST offers superior long-term ROI due to its accuracy, low noise, and seamless integration into development workflows.
However, combining both approaches delivers the most comprehensive coverage and ensures robust protection across the entire application lifecycle.
With Iosentrix’s advanced DAST and IAST solutions, you can eliminate vulnerabilities earlier, reduce false positives, and accelerate secure releases across every stage of your SDLC.
We deliver the accuracy, intelligence, and performance modern teams rely on.
Book a demo now to get started.