Are you well-prepared to safeguard your applications from cyberattacks? You may have heard of methods like penetration testing, source code analysis, and vulnerability scanning. But these techniques are not enough! You can give your app an added layer of protection if coupled with Static and Dynamic Application Security Testing (SAST/DAST).
In this blog article, we will talk about two types of application security testing— SAST & DAST — how they differ, their respective advantages and disadvantages, and how they complement each other for maximum security. So, if you want to know how genuinely secure your applications are, let’s dive into it!
Static Application Security Testing (SAST), also known as White Box Testing, is a method of evaluating the security of an application by analyzing its source code, binaries, and other artifacts without executing the application. SAST tools look for security vulnerabilities and weaknesses in the application’s codebase, such as buffer overflows, injection attacks, and cross-site scripting (XSS) vulnerabilities.
SAST is typically performed early in the development process, before the application is deployed, to ensure any vulnerabilities are identified and addressed before they can be exploited.
SAST tools make it easy to fix bugs for the developers by pinpointing the exact location of the vulnerable file or line of code. SAST tools also describe the error and its severity. These tools work by analyzing the source code or compiled bytecode of an application to identify security vulnerabilities, coding errors, and other issues that may lead to application security risks.
SAST tools typically use a combination of pattern matching, data flow analysis, control flow analysis, and other techniques to identify potential security issues. Pinpointing the exact location is not a big deal. Still, from the developer’s side, it saves a lot of time because, manually, it takes a lot of time to detect the error or vulnerability to fix, specifically on a large code base.
Meanwhile, the SAST tool makes it easy for developers to empower and detect them quickly. It helps businesses or organizations to scale and secure sensitive data against cyberattacks and automate to check security weaknesses.
Developers can use SAST tools to promptly address security issues before deploying the application in production. This increases the application’s overall security and helps reduce costs by avoiding costly rework or late-stage bug fixes. In addition, these tools allow teams to respond swiftly to any discovered vulnerability by providing continuous visibility into an application’s security posture throughout its lifecycle.
Developers design SAST tools to scan source code, detect coding errors, identify violations of best practices, and identify other potential vulnerabilities. Identifying these issues early in the development process helps developers ensure their code is secure and reliable before deploying it into production. Additionally, enforcing coding standards and best practices helps teams maintain a high level of code quality throughout their applications’ lifecycles.
SAST tools are cost-effective compared to other security testing tools because they can identify many vulnerabilities with minimal effort. This means organizations can test their applications regularly without incurring significant expenses or slowing development cycles. Furthermore, these tools assist organizations in saving time and money by offering visibility into potential risks within their systems, enabling them to address such risks quickly and efficiently.
SAST tools are designed to analyze large and complex applications quickly and accurately without requiring extensive manual effort or resources. This makes them suitable for organizations with large software portfolios that need a cost-effective way of ensuring their applications’ security without slowing development cycles or incurring high costs. Additionally, SAST solutions often include integrated tracking features that allow teams to track progress over time for better transparency and accuracy when analyzing results.
SAST tools automate the security testing process, which enables organizations to identify vulnerabilities more quickly than manual methods. This faster identification of potential weaknesses helps organizations respond more rapidly to threats, reducing the risk of exploitation. Additionally, automated solutions can easily be incorporated into existing development processes, allowing continuous testing and feedback throughout the SDLC.
Integrating SAST tools into an organization’s software development life cycle (SDLC) allows for continuous testing and immediate developer feedback. This ensures that security issues are identified and addressed early in development, reducing the risk of introducing vulnerabilities into production systems. Automating these processes can streamline the SDLC and provide real-time visibility into an organization’s application security posture.
Organizations can use SAST tools to fulfill compliance requirements like PCI-DSS, GDPR, HIPAA, SOC 2, or Sarbanes-Oxley to identify security vulnerabilities that breach regulations and industry standards. By proactively scanning for weaknesses before applications go live, organizations can ensure their applications remain compliant with applicable rules throughout development.
Dynamic Application Security Testing (DAST), or black-box testing, evaluates an application’s security by executing it and analyzing its runtime behavior for vulnerabilities. DAST tools interact with the application as a black box, simulating attacks from external attackers and looking for signs of vulnerabilities, such as unhandled exceptions or error messages that reveal sensitive information.
DAST is performed after the application is deployed to ensure run-time test coverage and identify any vulnerabilities that SAST or other testing methods may not have covered. Although SAST is a critical security testing method for detecting vulnerabilities in source code, it may not cover specific areas of an application, such as cases where the code generates pages by consuming user data.
DAST provides additional coverage by detecting vulnerabilities that SAST may miss during the testing phase, which is essential for identifying and addressing vulnerabilities on time. Understanding the specific use cases that SAST and DAST cover is crucial for maximizing their effectiveness in detecting vulnerabilities in software and applications.
DAST tools are typically used after the application has been deployed. DAST tools use various techniques to scan an application, including fuzz testing, vulnerability scanning, and penetration testing.
Meanwhile, DAST tool is not a replacement for penetration testing because it can only identify vulnerabilities discovered through automated testing techniques. In contrast, a skilled penetration tester can often identify vulnerabilities specific to the application’s business logic or other unique features.
Thus, a thorough security assessment should always include DAST tools and manual penetration testing.
The DAST tools simulate various attacks, such as SQL injection and cross-site scripting, to identify vulnerabilities attackers may exploit. They provide an external perspective, which allows the detection of the vulnerabilities that an attacker could exploit, that would not be identified by a developer or a SAST tool. They can test for security issues that may not be apparent from reviewing the code, such as configuration errors or misconfigurations, by actively interacting with the running application, DAST can identify vulnerabilities that might not be detectable by other means, such as denial-of-service attacks, broken access controls, and other issues.
DAST tools can provide a more accurate picture of an application’s security posture by testing the application’s running state. This results in more realistic and comprehensive testing than traditional static analysis limited to analyzing application code.
It’s important to note that DAST tools do not replace manual penetration testing, which can often identify vulnerabilities specific to the application’s business logic or other unique features. Therefore, a thorough security assessment should always include DAST tools and manual penetration testing to ensure the most comprehensive coverage possible.
By testing all functionalities, inputs, and outputs within an application, DAST tools offer broad coverage for security assessments. This helps identify potential vulnerabilities that may otherwise be missed or overlooked in other types of testing. Additionally, This comprehensive approach ensures thorough testing of the application before deployment.
In addition to identifying vulnerabilities in an application’s codebase, DAST tools can sometimes also detect issues within third-party features such as libraries and APIs. This capability allows developers to identify potential security flaws that static analysis cannot detect. Additionally, it enables the team to address any potential issues before deploying the application.
Unlike other automated security assessment techniques, such as static analysis or SAST tools, which have higher false positive rates due to their limited understanding of an application’s environment, DAST tools produce fewer false alarms since they test applications in their running state with greater accuracy and precision. Moreover, this helps organizations save time and resources by reducing the manual validation required for results generated from DAST tests.
By proactively testing and identifying security vulnerabilities, DAST tools can help organizations meet compliance requirements and industry standards. Organizations can use these tools to quickly identify any vulnerabilities that may violate regulations or industry standards, allowing them to take timely action to fix the issue. Furthermore, by continuously testing and providing immediate feedback, DAST tools enable organizations to stay up-to-date with the latest security standards.
Integrating DAST tools into the software development life cycle (SDLC) is an excellent way for developers to stay on top of application security. Continuous testing during development ensures that the application is tested constantly and provides developers with immediate feedback on any vulnerabilities discovered. This helps organizations identify issues before they become severe, saving time and resources in the long run.
Automation is essential when using DAST tools, as it allows for faster testing and quicker identification of vulnerabilities. Automation helps reduce human error and increases accuracy during scans, as well as reduces reliance on manual resources, which can take up more time and resources. Additionally, automation provides a more consistent approach to testing, keeping results reliable and consistent across all tests.
Overall, while SAST and DAST tools use different techniques and approaches to identify vulnerabilities, they both play an essential role in ensuring the security and reliability of software applications. Both SAST and DAST help ensure application security.
SAST tools analyze an application’s source code or compiled bytecode before deployment, typically at the development stage of the software lifecycle. This offers an advantage to developers because they have time to fix issues early in the development process. On the other hand, DAST tools test an application’s running state by sending requests or injections to its exposed endpoints. This is done later in the software lifecycle, usually when the application is live and deployed.
SAST tools analyze snapshots of an application’s codebase to identify potential security vulnerabilities in static source code. This allows for more comprehensive coverage and better detection of coding errors and architectural flaws throughout the application’s source code. Conversely, DAST tools send requests or injections to the exposed endpoints and functionalities of applications already running in production environments to test them. This allows them to detect vulnerabilities that arise from the interaction between different components of an application.
SAST tools can detect coding errors such as buffer overflows, SQL injection vulnerabilities, and other common coding errors. DAST tools can effectively find more subtle security issues from interacting components, such as cross-site scripting (XSS).
Developers may consider SAST tools more productive than DAST tools because they allow developers to analyze their entire codebase without needing a running application instance. Still, SAST tools may generate more false positives than DAST tools and require more fine-tuning to yield better results.
DAST tools can cover the full scope of an application, including any third-party components, while SAST tools may miss out on vulnerabilities in parts of the codebase that are not analyzed. This means that DAST tools are essential in providing broader coverage from an application security perspective.
Regarding integration with the SDLC, SAST tools have an advantage over DAST due to their ability to scan source code in the development and testing phases. In comparison, DAST tools are more suited for use during pre-production or production phases when applications are ready for real-world use. Regarding integration with the SDLC, both SAST and DAST tools can be integrated into the software development life cycle (SDLC) for automated security scans.
SAST and DAST are critical application security components. SAST and DAST can be integrated into the software development life cycle (SDLC) to provide value at different stages. SAST tools analyze scan source code in the development and testing phases. SAST tools can be kicked off as early as on each code commit, allowing issues to be caught early in the SDLC.
On the other hand, DAST tools are more suited for use during pre-production or production phases when applications are ready for real-world use. DAST tools can also be integrated into the SDLC for automated scans, such as during each test deployment, to ensure that any issues that arise during testing are identified before the application goes live.
Overall, SAST and DAST approaches differ in many aspects, but both practices are essential in finding and mitigating application vulnerabilities. As such, they should use in tandem to provide comprehensive protection against cyber threats.
SAST and DAST are integral components of an effective Application Security (AppSec) program and DevSecOps. AppSec includes building secure software applications from the ground up, while DevSecOps is a culture and methodology that promotes security within the development process.
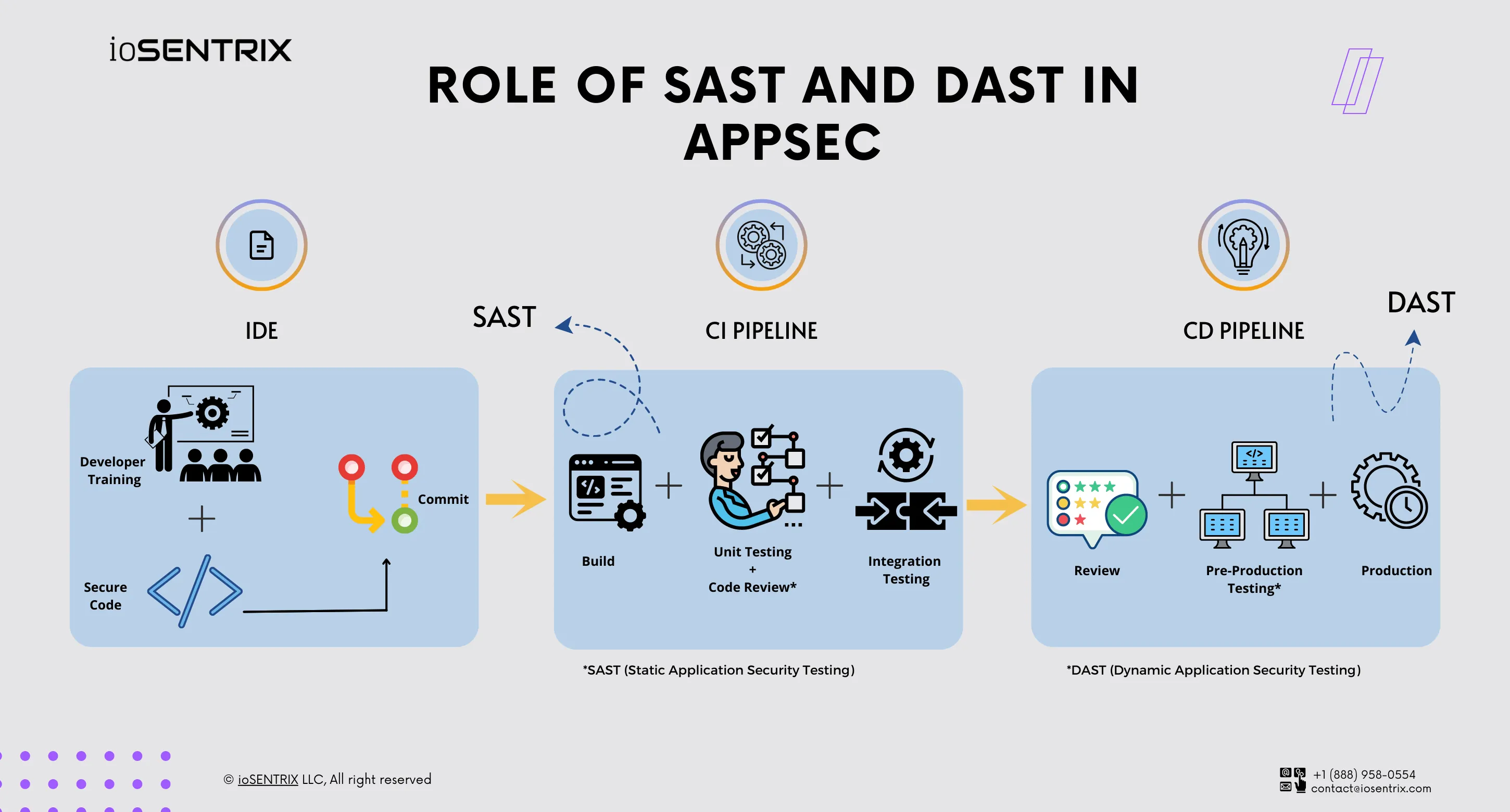
SAST is integral to this process as it analyzes source code for potential issues before malicious actors can exploit them. With SAST, development teams can identify potential vulnerabilities before deployment to production. This helps organizations prevent costly data breaches and protect against potentially damaging attacks.
DAST helps organizations detect vulnerabilities after an application is deployed. It’s an excellent tool for assessing how an application responds to external threats in real time. It simulates cyberattacks and looks for signs of weaknesses or errors that could indicate a vulnerability. Monitoring an application’s behavior is critical for maintaining its security post-deployment, especially with regular patching and updates.
SAST and DAST are powerful tools that allow organizations to scan their applications for potential vulnerabilities throughout their SDLCs proactively. By integrating them into their AppSec program, organizations can ensure their applications are secure from development through deployment and avoid costly data breaches by implementing SAST and DAST into AppSec pipelines while still meeting their speed-to-market demands.
Regular security testing is crucial to keep up with new threats and changes in attack surfaces, ensuring that any vulnerabilities can be detected quickly and efficiently remediated. Combining SAST and DAST methods can provide maximum visibility into potential security vulnerabilities, creating a much more robust security posture than relying just one way.
For business owners looking to improve their security measures, consulting with an experienced security consultant like ioSENTRIX can provide helpful insights on effectively employing SAST/DAST solutions.
ioSENTRIX specializes in helping organizations build better security practices, and our experts are dedicated to helping our clients protect their systems and networks from malicious actors. We understand the importance of secure applications and offer today’s highest-quality security consultancy services. With our help, you can have confidence that your data is safe and secure from cyber attackers.