
A network consists of many computing devices linked by physical or wireless connections. Networks use client-server or peer-to-peer setups and various protocols to enable connected systems to communicate. The increasing complexity of enterprise IT systems has made businesses more interconnected and efficient. Nevertheless, the convenience of accessing data raises concerns about data security and the overall IT infrastructure.
Typically controlled by a network administrator, network security involves incorporating both network software and hardware, along with IT security policies.
Network security infrastructure includes various solutions that safeguard a company’s network from cyber threats. With the expansion of corporate networks due to trends like cloud computing and remote work, it is crucial to have network security infrastructure in place to monitor and protect against digital threats effectively.
Your network infrastructure consists of components such as routers, switches, cables, and LAN cards. Additionally, network software is part of these structures, including operating systems, intrusion detection systems, management systems, firewalls, and security applications. The services provided by a network infrastructure include T-1 lines, IP addressing, satellite, DSL, and wireless protocols.
Every part of a system, including hardware, software, and services, can have weaknesses that may be targeted by deliberate or accidental actions. Network infrastructure security is meant to provide a variety of resources for protecting against both internal and external risks. Attacks like denial-of-service, unauthorized access, spam, and malware could pose threats to these infrastructures.
A business’s network security design needs to safeguard the company and its systems from various online risks. To achieve this, different network security features are necessary. Here, we explore some key elements of a typical business network security system.
Firewalls and intrusion detection systems (IDS) help protect a company’s network perimeter. Firewalls control the flow of data and stop unauthorized traffic from entering or leaving. An IDS detects harmful activities like malware and DDoS attacks and notifies the security team to take efficient actions.
An effective strategy for cloud infrastructure security involves various policies, technologies, and applications. It consists in implementing controls to prevent and address vulnerabilities or incidents promptly. This approach also supports business continuity by assisting with disaster recovery and ensuring compliance with regulations in different cloud environments.
Virtual private networks (VPNs) are a widely used solution for remote access. When a user connects remotely using a VPN, it establishes a secure tunnel between their device and the corporate network. This tunnel encrypts the data, guaranteeing that it remains safe from interception or alteration as it traverses a public network.
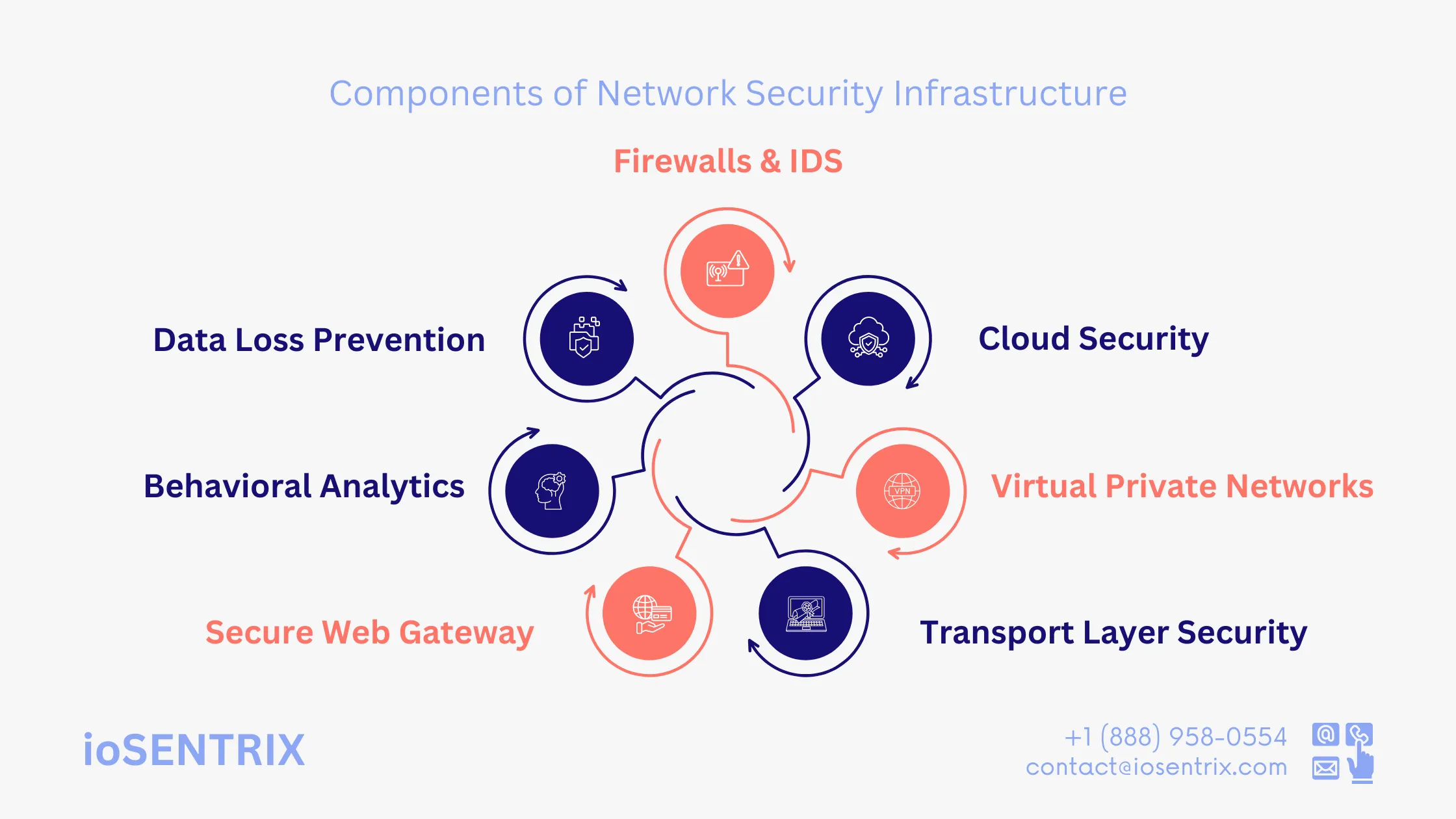
Transport Layer Security (TLS) is a network protocol that boosts the security of network connections. It sets up a secure and encrypted channel between a client and a server. One common use of TLS is seen in HTTPS, which protects unsecured HTTP traffic during web browsing.
Numerous cyberattacks, such as phishing and drive-by downloads, can occur when a user visits a malicious webpage. A secure web gateway (SWG) helps organizations detect and stop malicious web traffic. It uses reputation filtering, threat intelligence, and corporate policies to block dangerous websites.
Enterprise networks need to have better tools for spotting unusual behavior patterns. Behavioral analytics enables businesses to keep an eye on and study the actions and traffic flow of users, systems, and networks to identify irregularities, pinpoint possible risks, and improve security measures.
Data Loss Prevention (DLP) systems safeguard company data by pinpointing important information and using thorough analysis to spot and stop potential data leaks. This analysis includes techniques like looking for specific words, patterns, and built-in tools to find content that goes against a company’s DLP rules. This helps companies find, supervise, and stop theft or unauthorized access to sensitive data automatically.
Network security products are effective only when properly implemented and used. By following these recommended strategies, companies can improve the performance and operational value of their network security system.
Network segmentation involves dividing a company’s network into various sections based on the roles and trust levels of systems. This strategy helps deter attackers from moving sideways within the network by creating barriers for them to cross.
It’s important to be prepared for cyber threats, as they can cause chaos in your network. Whether it’s a security breach or a physical event like a power outage or natural disaster, losing data or functionality can be devastating. Having an incident response plan can help you minimize risks and be ready for different situations.
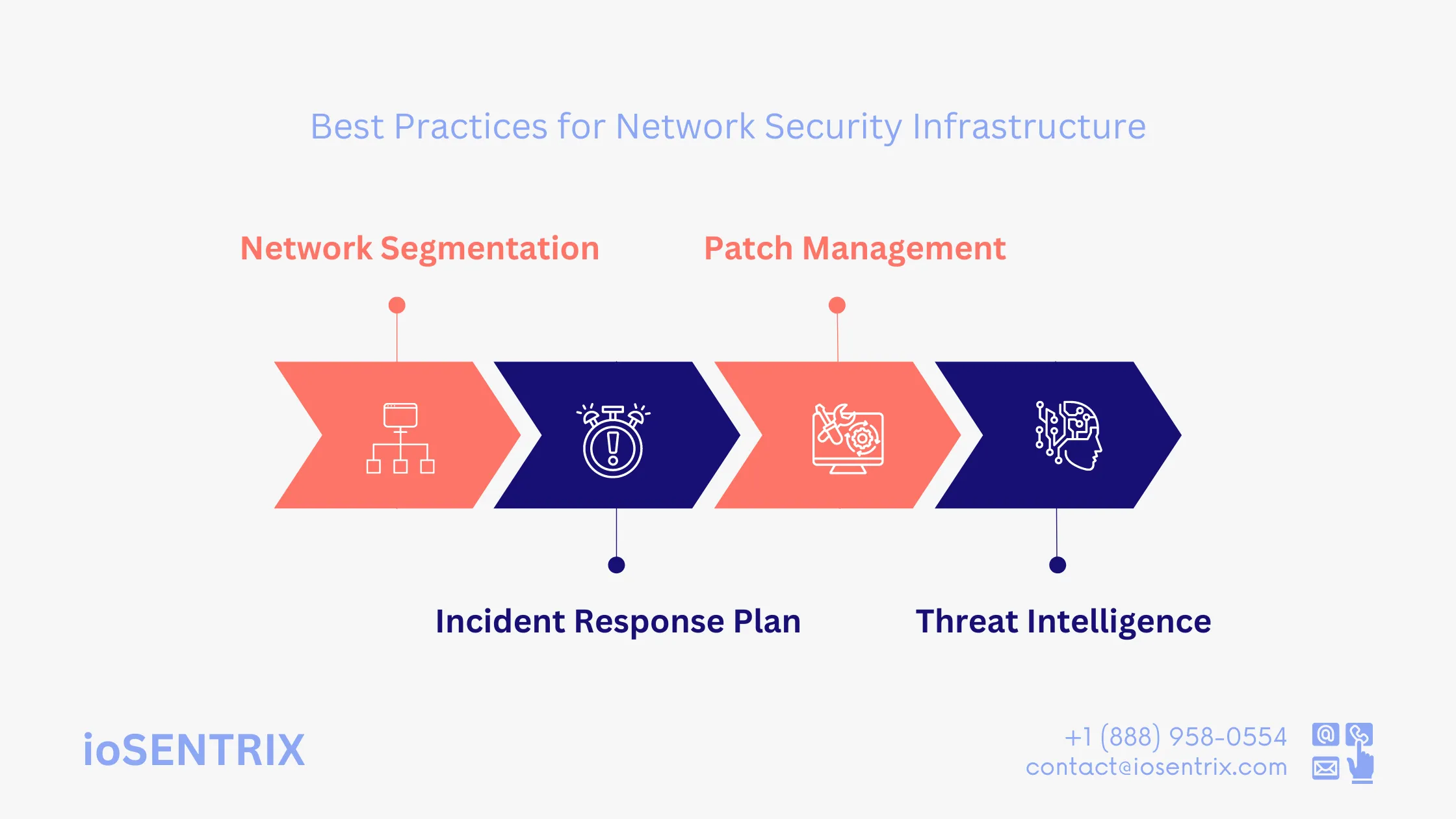
This process ensures that software is kept up to date with important features and functionalities that the organization requires. Additionally, it helps in meeting security and privacy regulations and can enhance overall system performance.Patch management also updates software to ensure compatibility with the latest hardware.
Threat intelligence feeds give details and signals of compromise (IoCs) for recent cyberattack campaigns. By subscribing to these feeds and using this information in their security program, organizations can better identify, stop, and fix possible cyberattacks.
The cybersecurity field is always changing with new cyber threats emerging, and new techniques and technologies being developed to address them. There are promising new network security trends on the horizon.
The zero-trust security model aims to control an organization’s network and application access points and safeguard important assets by enforcing strict access rules. Unlike traditional security approaches, zero trust examines each access request separately, taking into account factors like context and user privileges, instead of automatically trusting requests from within the corporate network.
To implement zero trust security, organizations need network security solutions that can apply detailed access controls. ZTNA stands out as a better alternative to VPNs as it provides more secure access controls compared to traditional VPNs.
Software vulnerabilities are increasingly becoming a challenge for numerous organizations. In 2023, there were more than 29,000 new vulnerabilities publicly reported, making software users and their customers susceptible to cyberattacks.
DevSecOps enhances production system security by integrating security measures during development. It aids organizations to lower the expenses associated with fixing vulnerabilities and decrease the likelihood of these vulnerabilities impacting the production environment.
Read our Blog: AppSec and DevSecOps.
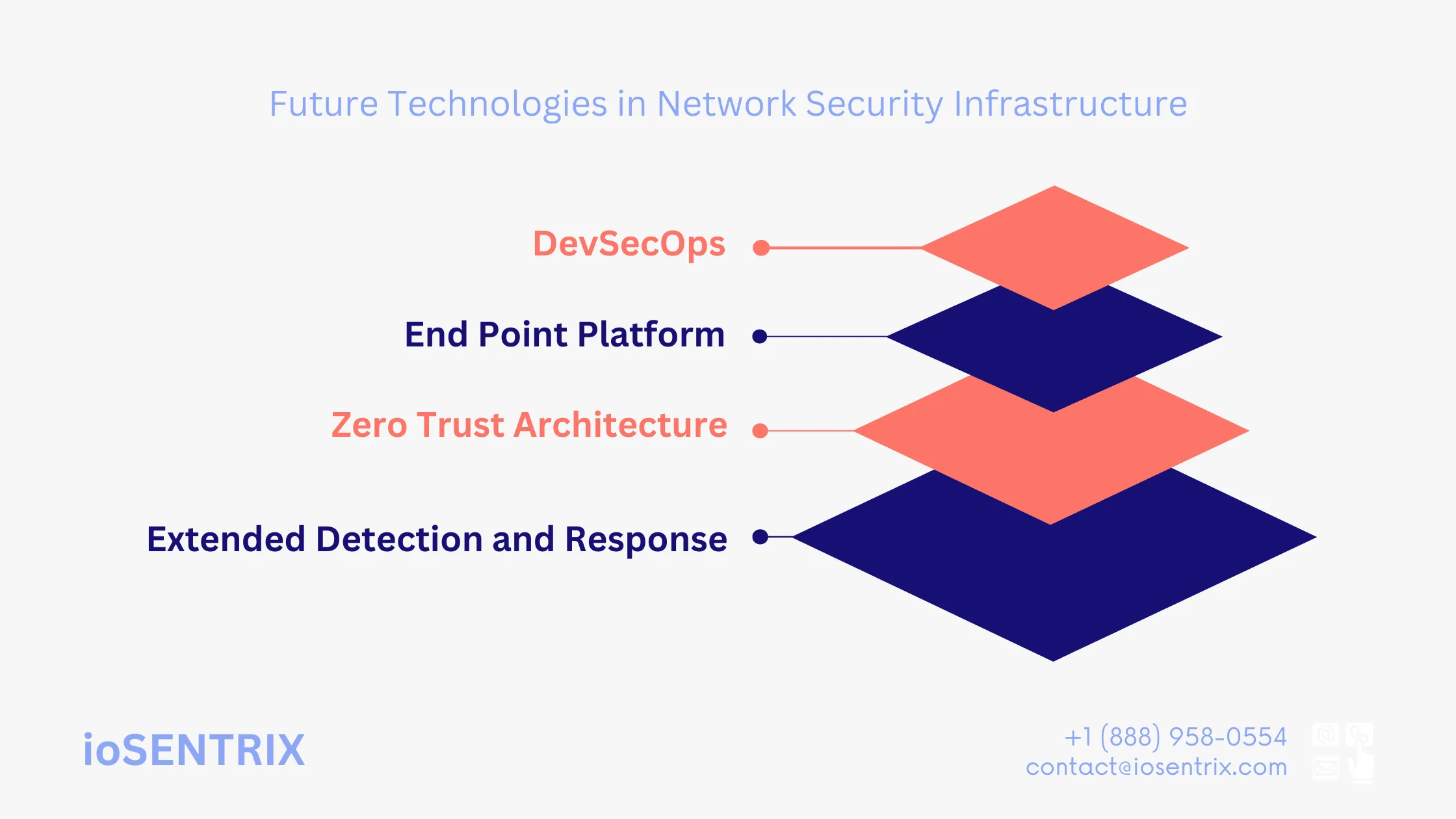
An endpoint protection platform (EPP) provides comprehensive security for an organization’s endpoints. It combines multiple security features like malware detection, behavioral analytics, and guided remediation to detect, block, and recover from various cyber threats. With centralized management, it ensures consistent enforcement of security policies across both on-premises and remote devices.
In the business world, there are many types of devices like laptops, servers, phones, and IoT systems used in corporate settings. As the number of these devices increases, businesses find it difficult to detect and prevent potential threats to these endpoints effectively.
XDR solutions gathers information from various places to better pinpoint possible threats to the organization. By improving visibility and connecting events, a company can better detect and address potential threats.
Network infrastructure security offers numerous key benefits. It helps lower costs, boost productivity, protect internal communications, and safeguard critical data. However, establishing and maintaining a strong security strategy for your network infrastructure can be complex and demanding.
For professional guidance and support in designing and implementing effective security measures, consider exploring expert technology solutions by scheduling a consultation with ioSENTRIX.