
Did you know that in 2022, the average cost of data breaches worldwide was $4.35 million, with phishing being the most common type of attack? Ransomware, a type of malware that locks critical data and often involves stealing sensitive information, is among the most common forms of attack.
Several industries suffer from high expenses for data recovery, damage to reputation, strained business relationships, legal issues, loss of customer trust, and regulatory fines. This highlights the importance of conducting cyber security assessments and analysis to establish a strong defense against threats.
An Industrial Control Systems (ICS) security assessment evaluates an organization’s ICS for weaknesses and vulnerabilities and establishes effective controls to protect against cyber attacks. This includes tracking authorized device access, using multiple defense layers, developing a vulnerability management plan, monitoring logins, ensuring secure configurations, and identifying security flaws.
With an ICS Security Risk Assessment, you can:
Also read our Blog: What is Cybersecurity Risk Assessment?
The CIA triad is a well-known security assessment method that focuses on Confidentiality, Integrity, and Availability. All three elements are crucial for evaluating system vulnerabilities and assessing risks. It is important to maintain a balance between these factors to ensure safe operations in industrial processes.
Keeping an organization’s data private and preventing unauthorized access are important aspects of confidentiality. There are often attempts to breach the security of industrial control systems. Protecting confidentiality includes ensuring safety through encryption, multi-factor authentication, data labeling, and other methods.
It is important to keep data consistent, accurate, and trustworthy throughout its lifespan. Data should not be altered while being transmitted, and precautions should be taken to prevent unauthorized changes, such as in cases of data breaches.
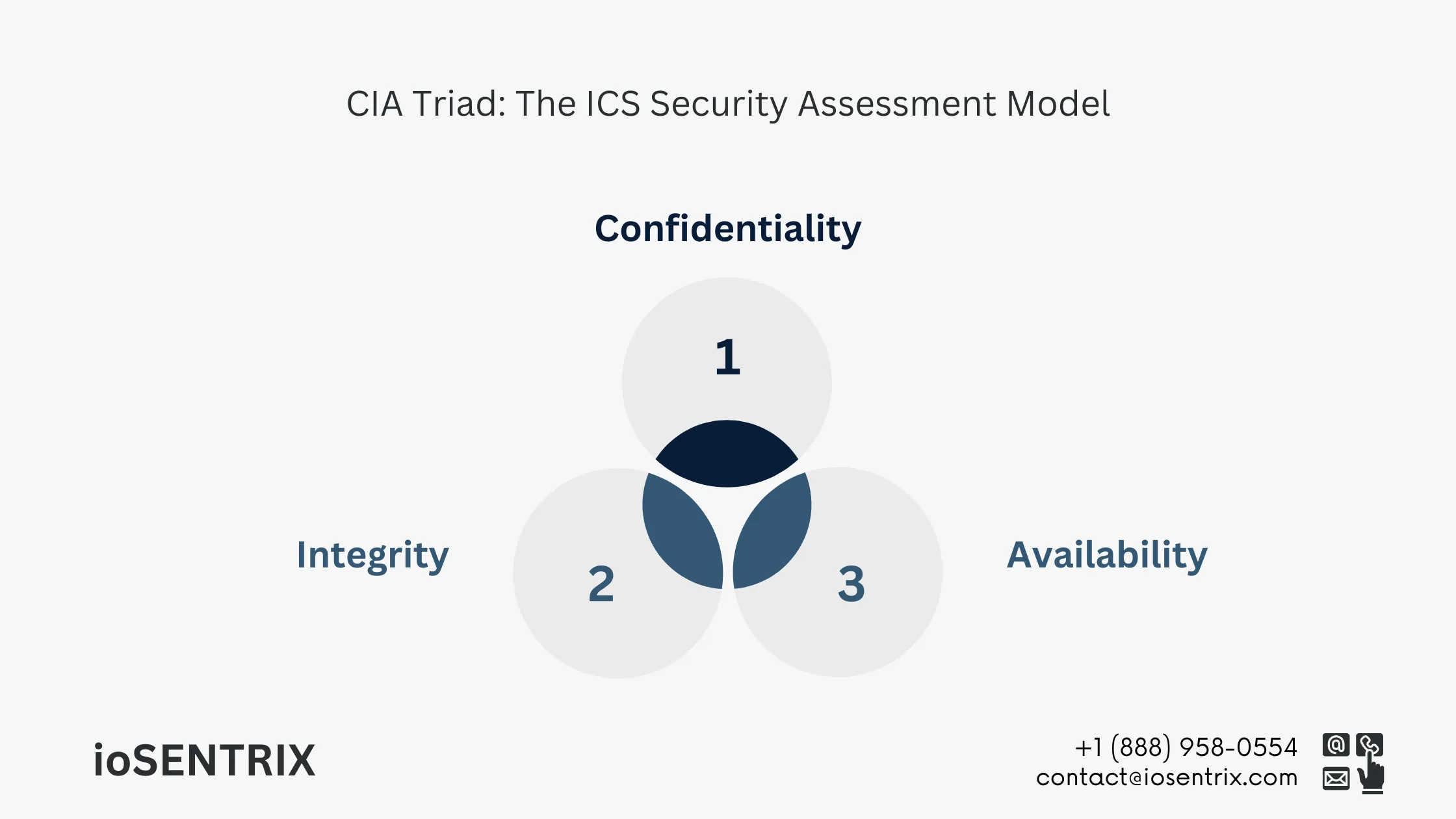
High availability of system and data is essential, as any disruptions can come from factors like natural disasters or cyber-attacks. This includes maintaining the necessary hardware, technical infrastructure, and systems for storing and presenting the information.
The CIA triad is a foundational framework used to guide security policies and practices, helping to evaluate system vulnerabilities in terms of confidentiality, integrity, and availability.
Even top tech companies faced an average of 1,435 Distributed Denial-of-Service (DDOS) attacks every day in 2022, highlighting the seriousness of the issue. It is crucial to conduct cybersecurity assessments regularly. Neglecting these assessments has resulted in significant losses and security breaches across various industries.
Below are several cyber incidents that disrupted various industries as a result of inadequate assessments:
It is important to address issues promptly through assessments to recognize possible risks and activate protective measures.
Various organizations adhere to specific security standards to meet the needs of their respective industries. In this discussion, we will explore a few of these standards.
The IEC 62443 standards help secure industrial automation and control systems. These systems are used in power plants, oil and gas plants, water treatment plants, and more. The standards offer guidance on implementing appropriate controls in ICS platforms.
IEC 62443 is widely used in the industrial automation and control sector by various industries. It offers a thorough set of guidelines that are highly recommended for industries to adhere to.
The NERC CIP standards are designed specifically for the power grid industry to ensure its security. They are implemented to safeguard the electricity sector. These standards include:
Recent data from the FBI Internet Crime Complaint Center shows a significant increase in cyber attacks, with 3.26 million complaints since 2018 resulting in $27.6 billion in losses. As the frequency of attacks continues to rise, it is necessary to conduct penetration testing specific to Industrial Control Systems (ICS) environments to strengthen their defenses.
The Industrial Internet of Things (IIoT) links important operations in various ways, expanding their vulnerability to possible risks. Without adequate security measures, hackers may gain unauthorized access to and exploit valuable information.
As a result, penetration testing plays a vital role in safeguarding against these threats. For example,
Also read: Choosing the Right Pentesting Approach: Automated or Manual?
Creating a plan for managing risks is essential. Factors like the physical work environment, ICS services, and security needs play a crucial role in this process. It is important to clearly outline the specific requirements of ICS environments to accurately identify potential risks.
This part of risk management involves evaluating risks and considering potential threats. It includes assessing how an incident in ICS could affect physical processes, dependent processes, and the physical environment.
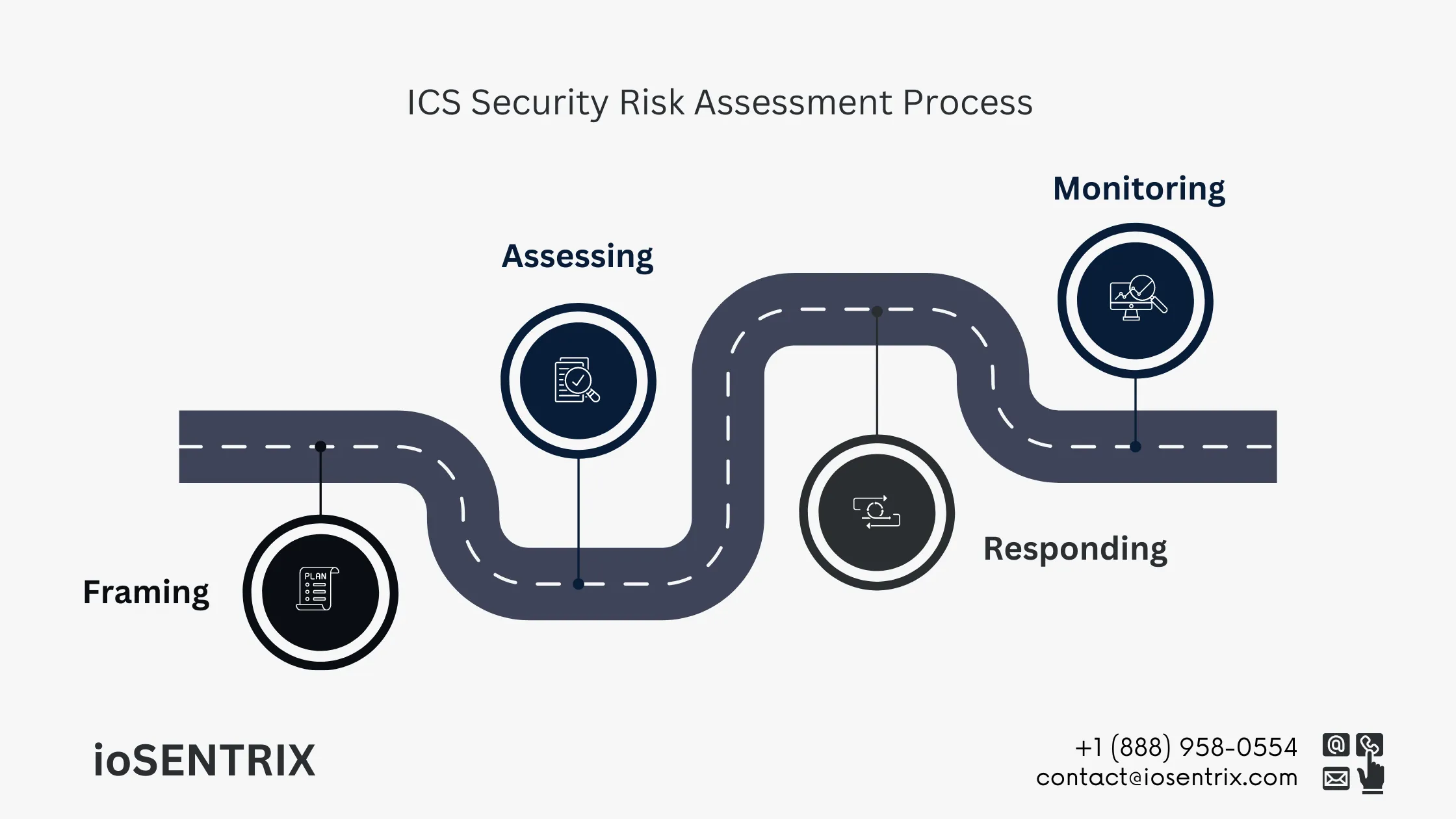
This element involves how the organization will address the recognized threat. It will consist of potential actions to reduce the risk. These actions might be limited by system needs, effects on day-to-day activities, and adherence to regulations.
This part of the process requires regularly checking for potential risks. It involves monitoring the execution of selected risk strategies, as well as keeping an eye on external factors such as geography, Market trends, and economic issues, that could impact risk assessment.
Each of these elements is connected and manages risks related to information security, physical security, safety, and financial security.
When designing the network architecture for ICS, it is important to keep the ICS network and corporate network separate. This is done to prevent DoS or man-in-the-middle attacks that may occur if ICS network traffic is routed through a corporate network. The ICS security architecture should include the following considerations:
Firewalls control how data moves between networks with different security levels, helping organizations stop unauthorized access to important systems. Firewalls enhance security by filtering out unnecessary traffic from computer networks. It’s important to regularly check firewalls for new threats and ensure they work in real time to prevent cyberattacks on industrial control systems.

It is important to keep the ICS and corporate networks separate to ensure security. There are various methods available to achieve this goal:
Dual Network Interface Card (NIC)
Dual-homed computers present a serious security threat when transferring network traffic between two networks without sufficient security measures in place. All connections between a corporate network and an ICS network must be routed through a firewall to ensure proper security controls are enforced.
Firewall Between Corporate and ICS Network
A two-port firewall helps to achieve enhancements in security. This can help decrease the chances of external attacks targeting the network.
Firewall and Router between Corporate and ICS Network
This design is strong and reliable, featuring a firewall and router for extra protection. The router helps relieve pressure on the firewall while offering a comprehensive defense.
To learn more, request a demo.
Costa Rica announced a state of emergency in response to ransomware attacks in 2022. Hackers demanded a $10 million ransom to refrain from releasing the stolen data. This incident highlights the critical consequences of cyber threats.
The urgency to adopt proactive measures to safeguard industrial control systems has never been higher. Therefore, organizations must implement security protocols and conduct regular assessments. Consistent adherence to security checklists is paramount in protecting critical sectors and maintaining their operational continuity.
If your organization uses ICS infrastructure, reach out to ioSENTRIX team members to discuss further. Our experts can assist in evaluating your current risk level, addressing any concerns, and initiating a security assessment for your crucial ICS assets.
Get in touch with us to secure your ICS environment.