
In real life, computer hacking may not be as dramatic as in movies, but its effects are very real. It can result in financial loss, theft of personal information, and major disruptions in people’s lives. Hackers often aim to profit or create chaos.
For businesses, the risk of hackers targeting POS systems is a major concern that can lead to significant financial and operational consequences.
Businesses worldwide regularly manage customers’ credit and debit card details during transactions in-store and online through e-commerce platforms. A security breach that exposes credit card data to hackers can lead to financial losses, identity theft for customers, and legal penalties or loss of consumer trust for businesses.
Hence, it is vital to understand the risks associated with a POS system hack and take preventive measures to avoid such incidents.
To examine the extent and seriousness of POS hacking, one can estimate the unfortunate incident involving Target and its significant data breach in 2013. During the festive period that year, cybercriminals managed to infiltrate the systems and retrieve debit card and credit card details of around 40 million customers who had shopped at the popular retailer across the country.
The financial repercussions to Target following this breach are believed to surpass $200 million, inclusive of an $18 million settlement in a lawsuit. Additionally, the breach resulted in substantial harm to consumer trust in the Target brand, the effects of which cannot be purely quantified in monetary terms but undeniably continue to impact the company’s operations.
POS devices serve as a central hub for managing transactions, expenses, and customer relationships. Many businesses rely heavily on these tools in their daily operations. However, cybercriminals often target PoS systems due to vulnerabilities in the devices and the connected IT infrastructure.
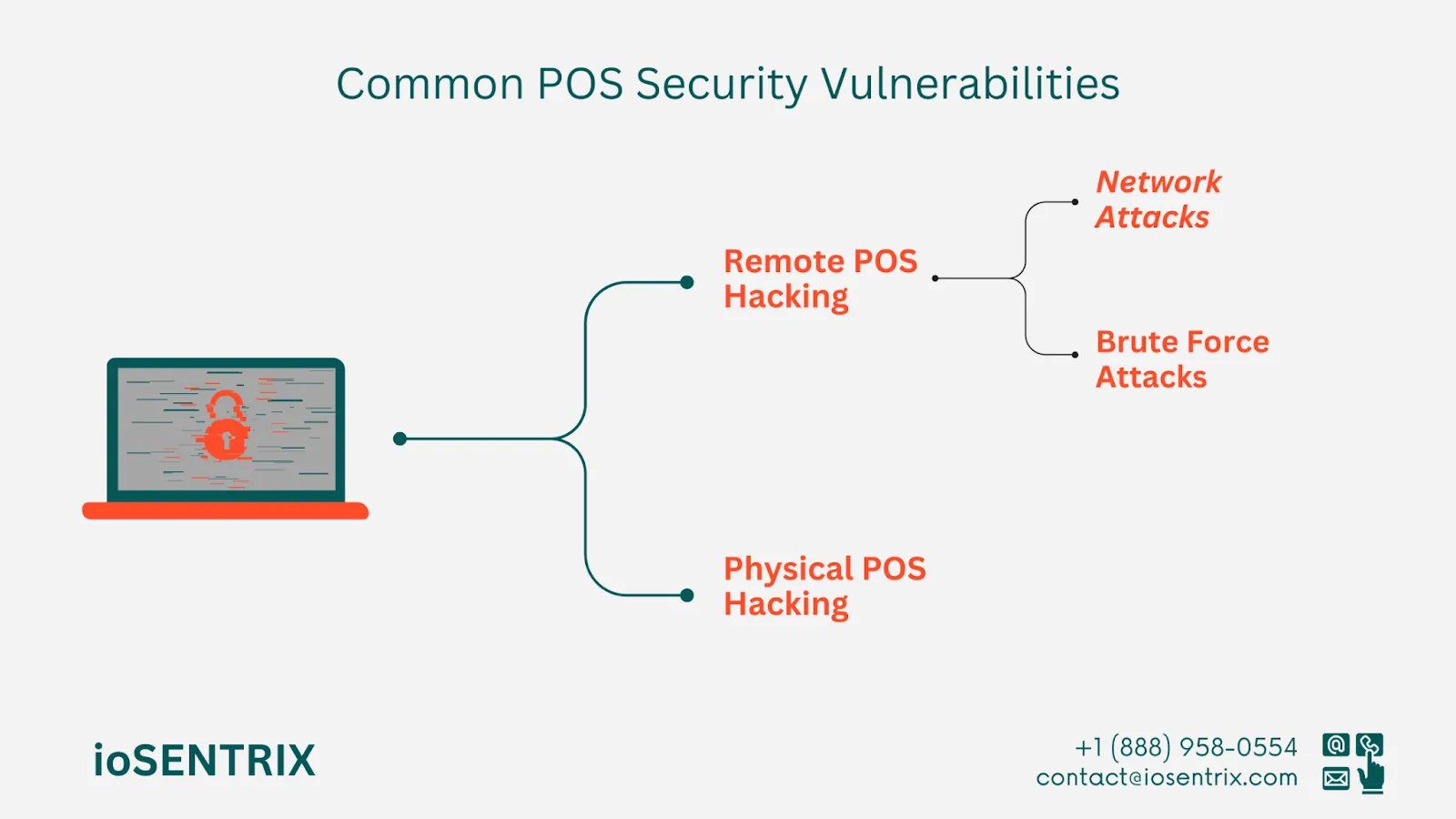
Numerous POS systems have vulnerabilities that pose a risk to businesses. In many cases, these devices come with a basic operating system and limited security measures. If this operating system is widely recognized, cybercriminals might already know how to exploit any weaknesses in the system.
They can easily target unsecured IP addresses or breach secure Wi-Fi connections to take advantage of the POS system. One common vulnerability in POS devices is their Internet printing protocol, which lots of businesses utilize for remote printing. Additionally, POS systems are susceptible to hacks through:
Network Attacks
Instances of potential security breaches happen when your POS devices link to your primary company network and become the direct target of a cyber attack or get affected indirectly through this connection.
It is recommended to maintain your POS devices on a separate network from your regular operational devices. By doing so, in case one system is breached, the impact is limited and does not spread across your entire organization.
Brute Force Attacks
This attack uses specific software programs to try different combinations of numbers and letters to guess passwords. Brute force attacks usually last a few days and can be effective if your POS passwords are easy to guess or set to their default settings.
In a well-known incident in Canada, a group of criminals stole card machines from various businesses. They used Bluetooth technology to get credit card information from the stolen devices. The hackers were able to quickly hack into the machines in about an hour, making it simple for them to take and return the devices before the businesses opened the next day.
This operation seems to have involved bribing employees to hand over the machines after work hours. As a result, more than $7 million was stolen from unaware customers.
In cases where thieves are highly skilled, they can install malware on POS terminals without having to remove them physically. This was evident in the case of a fast food chain, Wendy’s, where 300 of their stores fell victim to a malware attack targeting POS systems.
The malware was designed to extract credit card details from transactions. Investigations revealed that the malware was introduced through the use of credentials from a third-party vendor.
The company Forever21 experienced a security breach where malicious software infected POS devices for seven months without detection. The malware was stealing customers’ personal information on their cards.
Major businesses in the hospitality, retail, food service, and tourism sectors are frequently targeted by cybercriminals using POS attacks because of the abundance of financial information and the large number of transactions they process.
During a Black Hat security conference, a researcher presented a loophole in certain terminals operating on a Linux-based system that did not need firmware updates for proper authentication. This loophole enabled the researcher to implant malware onto a terminal using a modified credit card during a routine transaction.
The malware prompted the terminal to connect with a malicious server and download card-skimming software.
Many organizations face common vulnerabilities that make POS systems susceptible to hacking and digital attacks. These vulnerabilities are typically addressed through a cost-benefit analysis. Companies must adopt unique strategies to minimize risks based on their business nature and resource availability.
When devising methods to prevent credit card theft, consider these factors and allocate resources effectively to enhance security for both customers and the company.
Technology is always changing, and newer equipment tends to be more secure than older models. The security risks for a business can differ based on how current their hardware and software systems are. Software companies typically offer updates and upgrades for their products regularly. These improvements are necessary to lower vulnerabilities and lessen the chances of being exploited.
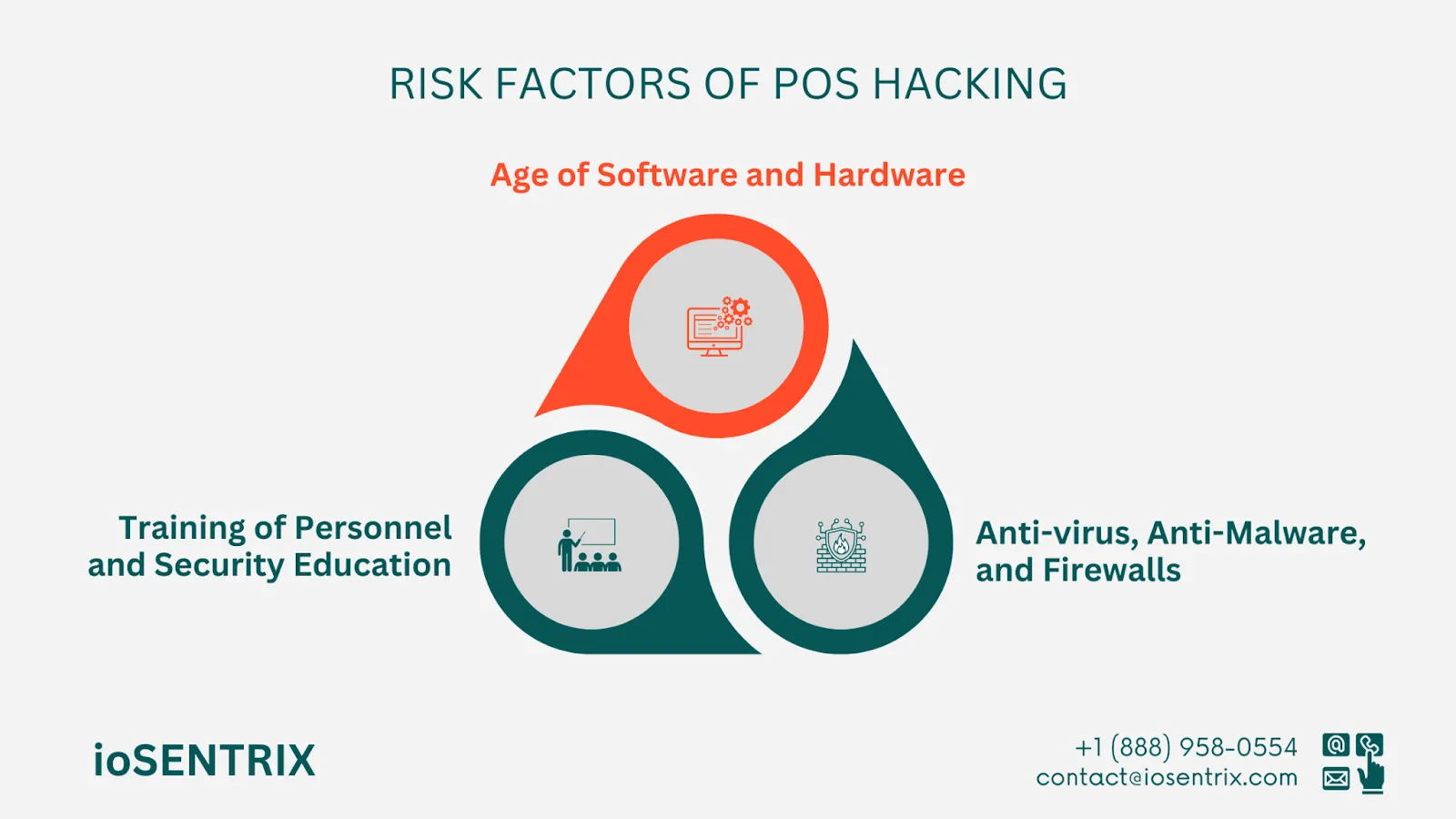
Anti-virus tools stop harmful software from infecting business computers, which could compromise other security measures. Anti-malware programs find and eliminate malware files before they can cause harm, as well as remove any already present on the system.
Firewalls act as a barrier between the internet and business systems- block access to malicious websites and require strict user permission to access internal systems.
Although security tools and firewalls are effective in protecting against hackers, they can’t prevent individuals from giving out passwords or account information in phishing scams. This is why providing thorough training to employees is essential.
With scammers getting more advanced in bypassing IT security measures, it is crucial for staff to understand how to identify malware and phishing attempts to prevent hacks from causing harm.
A POS system works similarly to a computer but on a smaller scale. It runs on different software programs like your computer does. To protect it from malware, installing antivirus software is the usual method. The antivirus software can be installed on the main system connected to the POS system or directly on the POS system. After installation, it will regularly check for harmful files or viruses that may pose a threat.
An antivirus program constantly runs to protect your POS system, which is a positive aspect. However, there is a downside as some POS hacking malware can be more advanced than the antivirus software which can lead to potential breaches without detection.
To prevent this, it is important to use reliable antivirus software and have additional security measures for your POS system.
POS hacks often exploit vulnerabilities in the network infrastructure, including unsecured Wi-Fi or poorly configured firewall settings. Offering free Wi-Fi to customers can boost sales by allowing them to leave feedback, browse your website, and access the internet easily. However, if the network is not secure, it can make your POS system and customer information vulnerable to hacking.
To address this issue, a recommended solution is to set up a distinct and protected network specifically for your POS systems to operate on. This involves separating your Wi-Fi connection from the primary system. Individuals with unauthorized access are thus prevented from gaining access to your computer systems.
It is important to protect all your networks, including the ones for your POS system and those accessed by customers, by using strong passwords. It is recommended to change these passwords regularly for added security.
It's important to be cautious about who can access your POS system to prevent potential hacks. Establish different levels of access for employees so that not everyone has unrestricted control over the system. This can help safeguard your system from unauthorized access and potential threats.
An additional crucial measure involves keeping a log of all personnel authorized to use the Point of Sale (POS) system, along with specifying the level of their access. This practice allows for the identification of responsibility in case of any incidents occurring within the system.
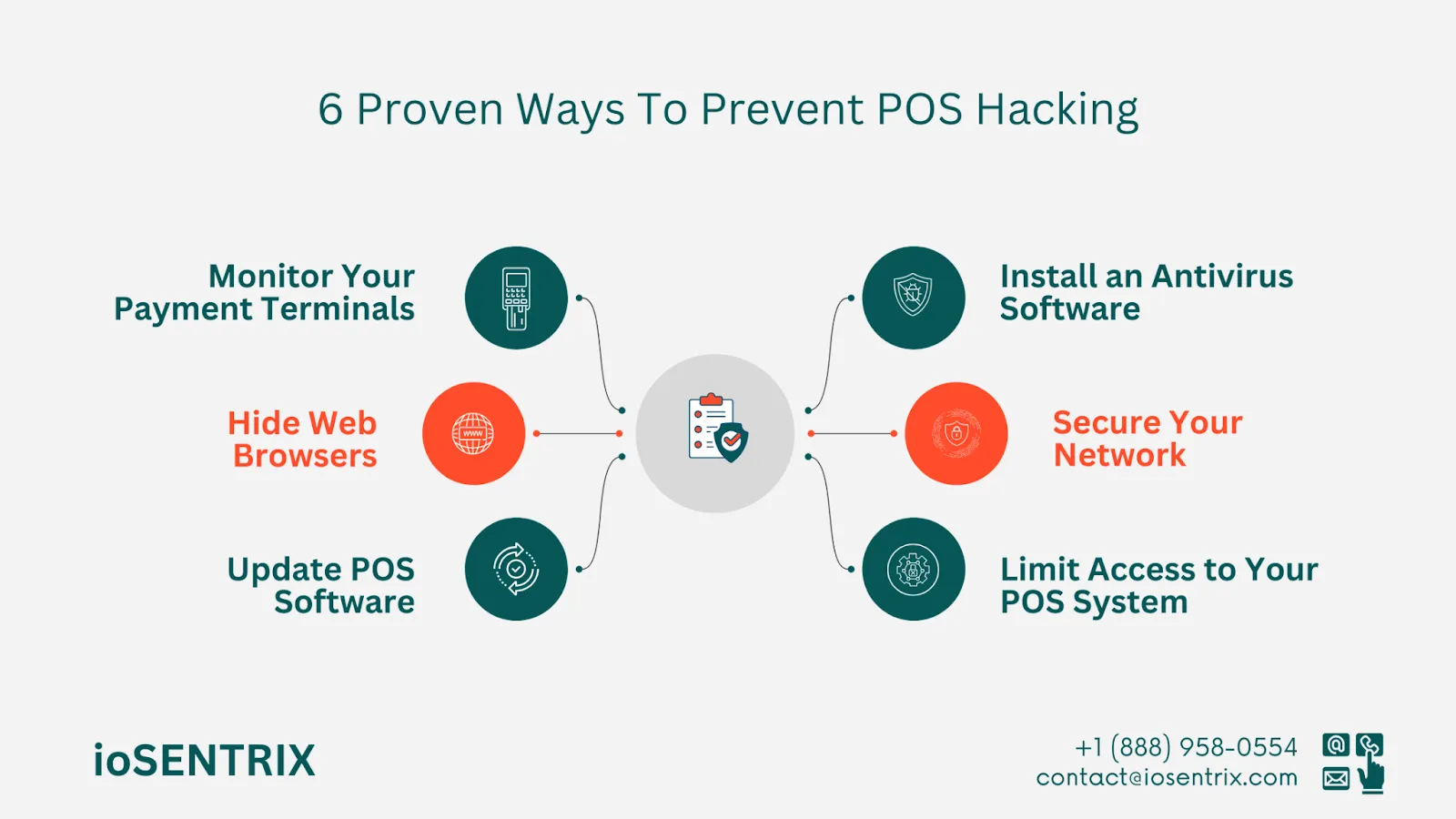
One effective way to prevent POS systems from being hacked is by regularly monitoring your payment terminals with video surveillance, conducting frequent checks, and providing maintenance. Hacking methods such as using card skimmers, attached cables, and other tactics to steal payment information when the POS system is used or a card is swiped are common.
This method enables you to detect suspicious activities, catch wrongdoers, and prevent hacking incidents. Regularly checking your terminals through video surveillance can help ensure thorough oversight and enhance security measures.
Make sure to inspect cables for any unauthorized devices or tampering that could facilitate skimming or data interception. Verify the serial numbers of all components and ensure they are securely installed in their appropriate locations.
Hackers can sometimes exploit your POS system by tricking unsuspecting employees into clicking on harmful links on websites. This can happen when employees are idle or bored at work. It is advisable to limit internet access on POS stations by removing web browser shortcuts from the desktop and toolbars.
It’s important to remember that completely removing a web browser may not be possible on certain computers. However, following the principle of “out of sight, out of mind” can help prevent employees from causing any issues for you.
Just like you update your computer software to fix bugs, make sure to also update your POS system software regularly. Updates aim to enhance the performance of your small business POS software by adding new features. Additionally, they include improved security measures to reduce the risk of hacking your POS system.
There are various ways for your business to reduce the chances of hacking into your POS system. One effective method is to enhance your business’s security by teaming up with a reliable payment processor, which can give customers added assurance that their data is secure.
ioSENTRIX offers a range of secure payment processing solutions that prioritize POS data and transaction security. You can rely on our technical service team to assist you in implementing efficient security measures at your point of sale. Your business integrity and data security are our top priorities.
When you choose ioSENTRIX, you can trust that your business will have the necessary POS technology and support. Get in touch with us today for further details, and we will be happy to assist you.