RDP brute force attacks on rise. How to keep your business safe

According to the UNDP, the Covid-19 pandemic is the most significant predicament that has hit us since World War Two. Since its advent, countries have been racing around the clock to slow down its spread.
With the number of confirmed cases almost going through the roof, a couple of drastic measures have been implemented to help curb the spread. Some of these steps include cutting down travel, closing schools, and other social joints, among others, to maintain social distancing.
Businesses have also been closed, and employees advised to work remotely to help in the fight against this health crisis. For employees to work from home, companies have been forced to let them access the company resources from home. A large number of companies are exposing workstations through (Remote Desktop Protocols) RDPs. Unfortunately, most of these companies lack the right security expertise to ensure safe work from RDP workstations. Due to the time crunch, they omit a lot of security controls that can be exploited by cybercriminals.
What is Remote Desktop Protocol (RDP), and how does it Work?
RDP is a proprietary protocol from Microsoft that lets you connect your Windows endpoints remotely with other computers over a network. For it to work, the company will typically install the RDP server software on their servers, and then users/employees will install RDP clients on their machines to connect to the company’s server software.
The scary downside with this technological trick is that if a malicious actor can access the users’ RDP session somehow, they get the same level permissions as them. This means that they can access all the users’ confidential data and information at will and even steal sensitive information or abuse it.
Cybercriminals Craving for Your Employees RDP Credentials
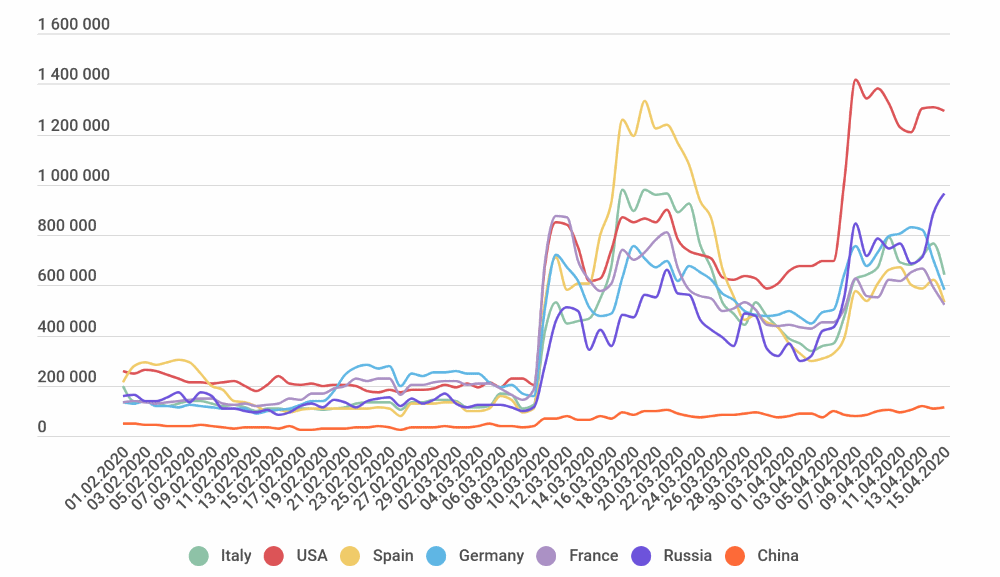
Growing number of RDB brute force attacks (Kaspersky)
Since the advent of this pandemic, everybody is remote, and this translated to a massive upsurge in the number of brute force attacks targeting RDP clients. Attackers are using compromised credentials that are leaked over the web (credential stuffing) to try and gain malicious access to company RDP servers. In the first weeks of March, there was an average of 200,000 attacks per day.
Fast forward to April 7th, and these numbers skyrocketed to over 1.4 million malicious attempts per day. This form of attack works by the hackers trying to brute force RDP passwords and username combinations until they get it right. In this search, the attackers can use just random characters or refer to their extensive database of compromised passwords and username combinations taken from various data breaches.
How to Protect against RDP Bruteforce attack?
There’s always something you can do to ensure that you’re safe from attacks like RDP brute force that rely on credential stuffing. Here are a few tips to stop attackers from maliciously accessing your servers.
1- Use Firewall
Note that, before launching an attack, the attacker will typically scan IP list ranges for the default RDP port; (Port 3389). Alternatively, they can obtain the list of RDP servers exposed over the Internet by using Open Source Intelligence Tools (OSINT) such as Shodan and Censys. For e.g., at the time of publishing this post, there were almost 1.4 Million Remote Desktop Servers reported by Shodan in the US.
Once the attacker finds a target, they launch brute force attacks to try and gain access, which, if successful, they can proceed to compromise the system. They may infect the system with Malware, Ransomware, launch a variety of other attacks against internal systems and users, or pivot on those machines to start attacking other external targets.
Although not preferred, firewalls could be used to help prevent brute force attacks by restricting access to the remote desktop instances and only allow access from the whitelisted IP addresses.
2- Use Virtual Private Network (VPN)
The VPN will allow secure access to your corporate network and ensure that the corporate assets behind a firewall could be accessed after proper authentication and authorization. The firewall here ensures that even though the corporate network is exposed to the Internet, not everybody on the Internet can access it unless they’re authenticated via the VPN. Use Multi-factor Authentication (MFA) with the VPN for added security and enforce strict password policies.
3- Use Multi-factor Authentication (MFA)
Cybercriminals notoriously use passwords to gain malicious access to servers and databases. According to Verizon, 80% of hacking incidents are due to weak, deduced, or stolen passwords.
Cybercriminals are intelligently attacking the mass number of servers. For e.g., instead of brute-forcing the password, they sometimes use a technique called Password Spraying. In this technique, a set of common passwords is attempted against an extensive list of usernames; therefore, account lockout policies and IP banning controls are bypassed.
To defend against such risks, you must employ MFA to help in verifying users before allowing access. It will help ensure that even if the hacker deduces or cracks the RDP passwords, they can’t gain access to the servers if they don’t pass the extra security check.
4- Implement Complex Password Policy With Frequent Rotation
You should implement a strong password policy with frequent rotation across the organization, including Remote Desktop Access. These passwords should not contain user names or weak passwords that are easily guessable. Instead, enforce a strong password policy such as a minimum of nine (9) characters in length, must contain characters from uppercase letters, lowercase letters, numerical digits, and special characters.
The frequent rotation policy will minimize exposure risks and mitigate most dangers. All these aspects will make it difficult for a malicious actor to gain access if they find or guess the credentials correctly.
5- Enforce Account Lockout policy
Just like we’ve mentioned earlier in this post, Brute-force attacks typically rely on multiple guesses using different username-password combinations until the cybercriminal gets the right combinations. If you configure accounts to lock after a specific number of failed attempts, you’ll significantly reduce the risks due to this kind of attack.
The account lockout policy must be configured in multiple layers (if supported by your technology stack). For e.g., the account must be locked for 30 minutes after six (6) failed attempts. After three (3) lockouts, the account must be blocked permanently and should require the employee to contact the helpdesk for manual reactivation.
6- Configure Remote Desktop Gateway
Deploying an RDP Gateway will ensure that any Remote Desktop port access from a remote connection is done on just one Gateway server. With this option, therefore, you’ll have to ensure that all the Remote Desktop services running on the servers and workstations are restricted to permit access from the configured Remote Desktop Gateway only. The Remote Gateway server here picks the Remote Desktop requests over a secure HTTPS protocol (Port 443) while connecting users to Remote Desktop Services on the target computers. You can also restrict the resources that the users are permitted to use Remote Desktop Gateway.
Microsoft offers an in-depth guide on how to install and configure the Remote Desktop Gateway on server remote desktop services here. There is also a complete tutorial on how to configure the Remote Desktop settings for your clients to use the Remote Desktop Gateway.
7- Activate Network-Level Authentication (NLA)
NLA is available on Windows 10, Windows Server 2012R2/2016/2019, by default. It enhances server security by ensuring that users that connect to the servers complete some authentication process. This will help you avoid Remote Desktop security flaws that can be exploited without authentication. Unless you’re connecting to RDP clients on other credentials that don’t support NLA, all your remote desktop servers should allow NLA connections automatically.
8- Auditing and Monitoring of Server Resources and Traffic Patterns
If you audit and monitor the server resources and traffic patterns regularly, or with the help of a third-party logistics cybersecurity firm, it will be easy to spot suspicious behavior like abnormal server activities that could signal red flags for a potential breach. Being able to detect these activities early is crucial. It will help you single out sources of the suspicious traffic patterns so you can respond swiftly and avert the breach by blocking the sources to fix the security flaw.
In Closing
Ultimately, the stay at home orders will be lifted, and we’ll be able to resume businesses as usual. Before then, we shouldn’t make cybercriminals work easy by leaving our ports and servers open. These security tips should help you beef up your server and Remote Desktop Protocol’s security landscapes. Boost your business’ cybersecurity by partnering with a reputed cybersecurity company like ioSENTRIX today to help you build a defense in depth.
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter