Prior to cloud computing, we were used to downloading and installing applications for our use. Organizations were habitual in creating their data center, hiring IT professionals, buying servers and related supplies, etc. It might seem surprising how technology emerged and shaped the world in just a few years.
However, cloud computing is a decades-old technology, but since its evolution, it has become an essential aspect of information technology.
Cloud computing has given businesses and average users many alternatives regarding flexibility, reliability, performance, presences, compatibility, cost, and investment as an innovative solution. Currently, every small to large enterprise utilizes cloud services, but as everything comes at a cost, the cloud security risks are growing relative to the increasing demand for cloud services and applications.
In this blog post, we have covered the security aspects of cloud computing and the shared responsibility it comes with. But before we jump into the shared responsibility of cloud security, you must understand what cloud computing is, how many services it offers.
Cloud computing is the process of accessing services such as storage, applications, server, infrastructure, etc., hosted on a remote data center managed by the cloud service provider (CSP) on a pay-as-you-go and pay-upfront model via the Internet sphere.
It is basically an on-demand computing service that enables the companies and individuals to store, access, or use the services virtually with peace of mind in terms of backup, availability, reliability rather than having the required resources (e.g., servers, hard drive, apps, etc.) on-premise.
Cloud computing is no different from regular computing, except the fact that rather than owning the infrastructure, software, data center, you rent out the resources from a cloud service provider to avoid the upfront cost, maintenance, and space. You can use cloud service either by paying a fixed amount for your allocated resource or by a variable amount according to your usage.
In it, you simply log in to your cloud environment from your browser or cloud software and are granted access to your chosen services and resources.
The cloud computing infrastructure uses a large group or remote server, data centers, and physical resources networked to allow centralized data storage, resource sharing, and online access to different computer services or resources. It shifts your workload to its centralized infrastructure and offers you the flexible interface to use virtual resources.
All the virtual resources are connected to remote cloud computing infrastructure and handled by your cloud service provider, including the physical components, including on-site database, servers, hardware, computers, etc.
In cloud computing, your service provider usually maintains multiple copies of your data and hardware, software resources to mitigate instances of security threats, data loss, breaches, etc.
The cloud service providers (CSP) give three major types of cloud service models. Depending upon the needs of your business, you can use any one or all of three.
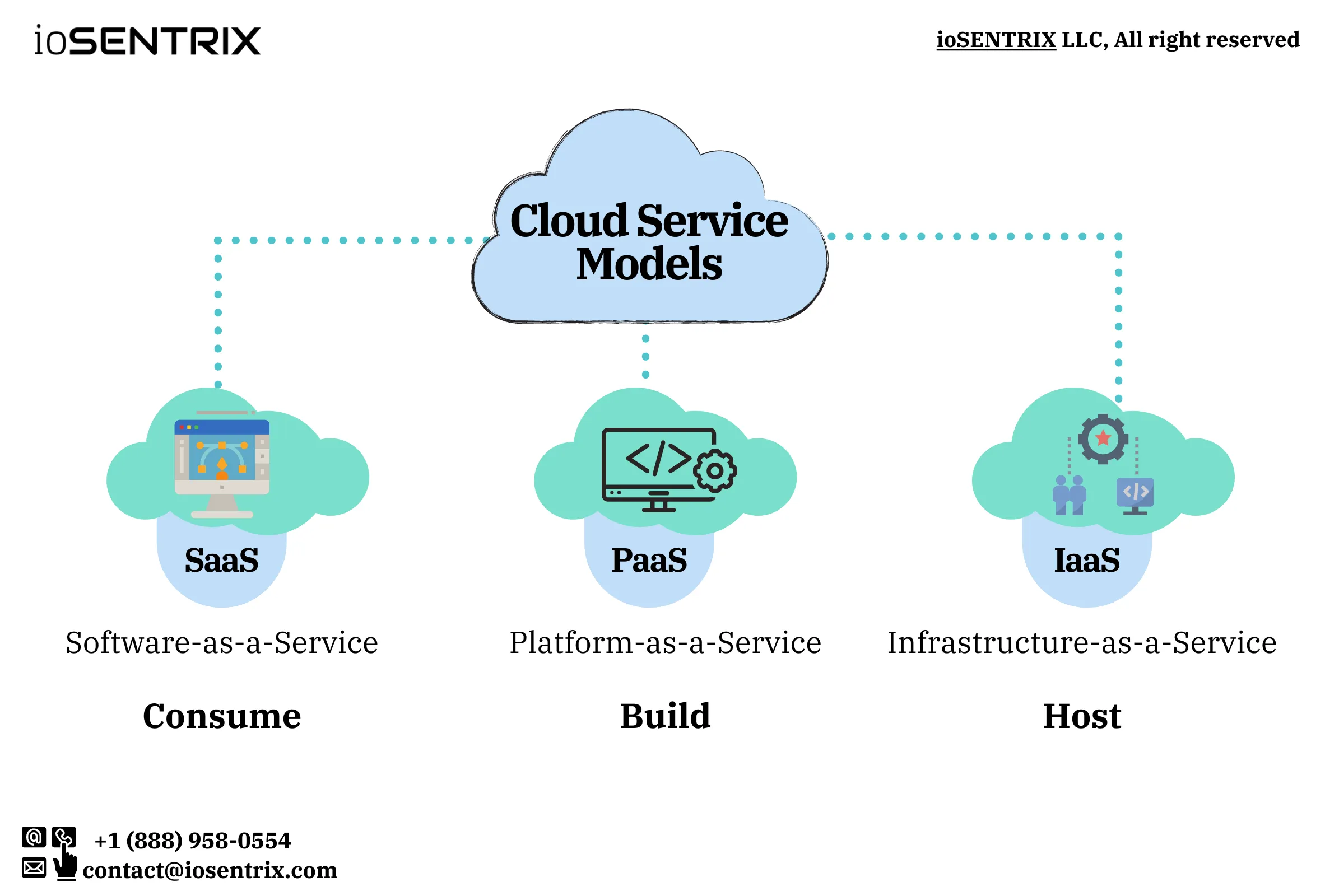
SaaS is a cloud-based service that provides the software on licensing model. It offers users to use software located on a remote server. Some SaaS comes with a ready-to-use environment where you do not need to configure them to consume, but some SaaS requires you to download or install the software.
Today’s finest examples of SaaS are DropBox, Gmail, Slack, Zoom, Microsoft Teams, etc.
This cloud-based service provides a complete suite of development and deployment resources and environments such as servers, storage, database management systems, etc., to create, run and manage the application.
Google App Engine, Salesforce Lightning, Wasabi, AWS Elastic Beanstalk are the most used examples of PaaS.
This cloud-based service offers fundamental access to servers, storage, virtualizations, networking, and other computing resources as an alternative to on-site expensive capital resources.
Google compute engine, Microsoft Azure, AWS Elastic Compute Cloud (EC2) Cisco Metapod are prominent examples of IaaS.
Other than these three cloud services, there are plenty of other computing services such as serverless computing, BaaS (Backend-as-a-service), FaaS (Function-as-a-service) that organizations can obtain based on their requirements and needs.
Previously in the traditional data center, you were responsible for the overall security from your physical data center building, assets to the virtual environment such as application user controls, server, internet connectivity, etc.
Unfortunately, when it comes to maintaining cloud security, people often confuse it and assume that there is no need for security in the cloud, and it is by default secure, or it is the sole duty of the cloud service provider (CSP) to maintain the overall cloud security. However, the notion is not valid.
In 2017, An unsecured AWS S3 storage bucket owned by Accenture was found by security researchers. Due to the misconfiguration of media storage from the customer end (Accenture), the data, including authentication credentials, secret APIs, digital certificates, decryption keys, and customer data, was publically available for download. At one point, it was also discovered that more than 137 GB of Accenture data was posted on the dark web.
In cloud computing, the security is addressed on the shared responsibility model, which means your cloud service provider and you maintain the security on your defined level. You can keep a secure environment with less upfront cost by working and sharing security responsibilities with the shared responsibility model.
In the essence of cloud security, the cloud service provider (CSP) is only accountable for your cloud deployment and the necessary security element that comes with that deployed environment. Your provider (CSP) offers a great benefit by administering the burden of many operational functions, processes including security.
Depending upon the services such as SAAS, PAAS, IAAS, your cloud service provider will handle and manage the resources from physical network to virtual network, including servers, storage, runtime operating systems, applications, middleware, etc. Still, you will be responsible for maintaining security and compliances for the rest of the deployed environment.
Understand it this way, suppose you have rented out a property in the Acme building. As a property owner, your landlord has done the necessary repairs and maintained the common areas to keep the vital services running, such as plumbing, electricity, proper trash receptacles, etc.
But once you get the procession and become the tenant, you are responsible for putting necessary locks on the entrance and other areas to keep your home secure against robbery and thefts.
In cloud computing, the security works the same. The entire cloud security scope is classified between you and your cloud service provider into two main categories, i.e., security of the cloud and security in the cloud to maintain the security posture inside and outside the cloud environment.
The security of the cloud is the CSP’s responsibility, and The security in the cloud is customers’.
Cloud computing has a broad set of technologies, associated infrastructure, policies, applications, and related services that demand security at each layer. On a deeper level, the shared responsibility model varies between cloud service providers and could be changed depending on what services you opt for and which service provider you choose.
There are multiple cloud service providers (CSP) such as AWS, Azure, Google (GCP), Digital Ocean, Oracle, Alibaba, etc. However, on a broad level, based on your subscribed cloud service model, the security necessity between your service provider and your end can be broken down into the following.

The majority of the cloud breaches happen because of customer’s mistakes and misconfiguration rather than CSPs. According to Gartner, through 2025, 99% of cloud breaches and failures will occur due to customer’s fault. Therefore, it is essential to know and understand the responsibilities that come with the incredible power and feasibility of the cloud.
It refers to the security concerns faced by the cloud service provider regardless of service model (such as SAAS, PAAS, IAAS). Your CSP manages the security of the cloud, and they are accountable for secure cloud deployment and immunity against cyberattacks, security incidents, natural disasters, or any other mishap.
The CSP provides security at the following layer of the cloud service model.
Physical Network
Cloud vendors and service providers protect the physical networks through multiple software and physical means. The physical network security includes the protection against intrusion and tempering to any of the cloud-supported hardware. Additionally, they ensure the uninterrupted and high availability of internet connection and power supplies, reliability and flexibility of entire infrastructure resources, controlled access to the data center, monitoring of critical parameters, disaster recovery solution in case of natural catastrophe, network, drives, server equipment protection and stability with comprehensive built-in backup and restore solutions.
Server and Storage
By spinning up the cloud environment, the cloud service provider maintains 99.99% (or lower in some cases) availability and security of servers and storage devices such as hard drives, RAM, storage arrays, network servers to protect user data, offers seamless migration and backup if any device fails to perform its supposed operation
Hypervisor
The hypervisor allows multiple guests operating systems on a single host and allocates single hardware to be shared across multiple virtual machines, which bound the cloud vendors to provide separate virtualization, segmentation, and isolation of cloud components such as CPU, GPU, OS, memory to protect the user cloud environment, application and data.
The security of components mentioned above is provided by the cloud service provider irrespective of the cloud service model. The rest of the component’s security varies with the cloud service model you choose to buy.
In the platform-as-a-service, your cloud service provider offers you a convenient and automated secure environment to develop, test applications, and spin up the servers through the self-service processes. Whenever you opt for PaaS, your cloud service provider manages the security of all cloud components mentioned above in IaaS with addition to two elements, i.e.
Virtual Network
The virtual network provides agility- complete control over your network and allows you to deploy your resources at any time. In addition, it facilitates in defining network segmentation to support multi-tier architecture as well as segregation between multiple development, production, and corporate networks. To offer you redundancy with less downtime, your service provider performs the logical isolation of the cloud network dedicated to your subscription and defines the access control to your virtual private cloud (VPC) along with managed security operations.
Operating System
Since in the PaaS, the operating system is rendered by your service provider, eventually they become the one responsible for maintaining and releasing patches, minor and major security updates of operating system (OS), web server, application server runtime availability, etc.
In SaaS, your cloud service provider renders you a dedicated software environment and is hence responsible for managing its security. Along with the application itself, your cloud vendor maintains the cloud software supported resources such as physical network, server, and storage, hypervisor, virtual network, operating system, etc., similar to IaaS, PaaS.
Application
The cloud vendor solely managed the application security and is responsible for providing data security in the multi-tenant environment. In addition, they are bound to provide data security in transition and at rest. Also, if any security flaw or vulnerability arises due to the third-party component used in the application, it is entirely patched by your service provider.
Security in the cloud refers to the security concerns faced by the customer who uses the cloud service, stores data, or hosts applications on the cloud. This cloud security category depends upon the customer, i.e., YOU, who utilizes the cloud environment.
User
Your sole responsibility is to maintain user access and security to prevent the internal cloud environment from malicious invasion. You must maintain user access on the ground level and deploy the access control mechanism. As for robust security against unauthorized access, you may follow multi-factor authentication (MFA), single sign-on (SSO), access key, password management, and other relative measures to maintain identity and access control.
Data
You have direct control and visibility over your data. Therefore, it falls under your responsibility to control sensitive data by secure configuration, encryption mechanism along with an appropriate protocol for data transmission in order to maintain data security across and outside the cloud environment.
Let’s understand the SaaS shared responsibility model with an example.
Suppose ABC company provides an on-demand cloud-based object storage service via web-based software. As a customer, you have purchased the monthly or annual subscription for your business, established the account, and further shared the platform with your employees to use and store data.
Now, as a customer, it is your assigned responsibility to implement a strong password, multi-factor authentication policy among your employees and users having access to the software.
Furthermore, to secure your account from unauthorized access, you would be responsible for monitoring and auditing the logs and traffic. You would have to ensure encrypted data storage, password-protected links for data sharing among the team members so no unauthorized person can read the data or make it accessible by hacking into an employee’s account of credentials.
Application
When you opt for platform-as-a-service, your shared security responsibility demands you to protect the user, data, and application layer. In the PaaS, your service provider offers you tools and resources to develop the application, and so the application security is shifted to your court.
It is your responsibility to develop and design your software/application with secure SDLC consideration. It requires you to mitigate risks, promptly patch the vulnerabilities and constantly monitor your built software against the latest attack vectors and trends. Whereas the rest of the data and user security management remains the same for you as SaaS.
Understand your responsibilities in PaaS with the following example.
Let’s assume you have purchased a platform-as-a-service to build an object-storage system. So, as a user of that particular PaaS, you would be spinning up your web server, designing and developing the application with all their resources, but you have to manage the security consideration within the application you built around using the PaaS.
It includes database and security controls selection such as cryptogram mechanism to ensure data security, protocol selection for secure data transmission, identity and access control to restrict unauthorized access, user lock-out policy, data at rest and in transit pattern, PII management, etc. Along with it, you would have to secure your interconnected systems, your code repositories against invasion, ensure secure production and testing throughout the development and integration phase.
Learn more about How to achieve application security with a secure software development lifecycle (SDLC)?
Moreover, you are not only obliged to maintain the security of the application that you design and develop using the cloud service but also, you are accountable for maintaining your team access and data security within the PaaS cloud service environment.
It is simple; you are liable for having an appropriate identity and access management (IAM) system, data storage, and security mechanism in place so no unauthorized user or employee can access your production environment. Additionally, it is necessary to restrict attackers from compromising the security, inserting malicious code, forged certificates, or misusing any internal resources.
In the cloud environment, your responsibilities increase with the increasing demand for cloud resources. For example, with the Infrastructure-as-a-service, you rent out an on-demand infrastructure computing resource. Like your PaaS responsibilities, you need to maintain application security, but you get additional responsibilities to manage the rest of the deployed environment, i.e., virtual network and operating system.
Virtual network
In IaaS, your service provider offers your company an entire infrastructure for your day-to-day operations, development, etc. Your provider only maintains the security till the hypervisor layer. All the networking above it and under your control is directly managed by you.
Therefore, it is totally up to you and required from your end to constantly monitor, segment your virtual network, define access controls, and securely configure your virtual private cloud and internal network.
Operating System
With the infrastructure-as-a-service, you get to choose and install your desired operating system on your network, which increases your responsibilities. As a direct authority of your operating environment, you need to keep your OS secure against vulnerabilities affecting your server-based resources with up-to-date patches.
Let’s get an idea of your IaaS security responsibilities.
Suppose you have bought an IaaS service model for your business. Your cloud service provider has set up your environment with all pre-requisite elements. Now it is you who will be heading the overall development and cloud environment with all security considerations. It involves operating system selection, vulnerabilities management, multiple virtual network creation, virtual network isolation and segmentation, database integration, load balancer management, web server integration, application development with secure SDLC, etc.
In short, from the operating system selection to employees’ access to the cloud territory, you must have to monitor all the activity, vulnerabilities, patches and promptly manage them.
The shared responsibility model provides an appropriate action plan and clear benchmark to both customer and cloud service providers to maintain security in and out of the cloud. Whenever you go for any cloud service model, learn and understand your security duties and requirements.
Above all, regardless of what cloud service provider and service model you use and where your responsibilities start or end, you must ensure that your business cloud environment meets the compliance terms and conditions.
Transforming your business with cloud infrastructure does not eliminate the compliance requirements nor makes it automatically adaptable with it. You must perform due diligence with cloud security assessments to gain visibility, analyze and respond to cybersecurity threats and maintain the regulation requirements.
As a cloud security service provider, we help organizations secure their cloud realm with robust configuration and security management. It is impossible to be immune to cyberattacks, but it is possible to reduce the risk to an acceptable level, which we do at ioSENTRIX. We ensure that your computing environment remains compliant, secure, and resilient from external and insider cybersecurity threats and attack vectors. Contact us today for a consultation or discuss cloud security concerns.