How to achieve application security with a secure software development lifecycle (SDLC)?

With the internet revolution and application modernization, our lives have been profoundly surrounded by tons of applications, be it health care applications or enterprise and database software. Everything is making our everyday work more manageable and becoming fundamental than before.
For the last few years, the technology industry witnesses data breaches frequently, compromising the security and privacy features of applications and software through multiple unpatched and 0-day (zero-day) vulnerabilities. There are varied reasons that provide opportunities for attackers to take advantage of missing security restrictions.
As reported by DBIR 2020, 43% of data breaches in the past year were connected to web-application vulnerabilities. This happens because most of the applications do not have appropriate security controls that could prevent an attacker from lurking in and bypassing the limitations. This works as the main reason behind the exponential growth of data breaches.
Organizations must implant security consideration into their application development process to deter breaches and build a defense in depth. There are countless reasons for integrating security into your SDLC, ranging from data breach prevention to lessen the impact of breach/attack on your business from reputational or stakeholder’s trust loss to huge penalties and bankruptcies or spending a high budget on post-development fixation.
To understand how you can embed security into your software or applications development lifecycle, you must have to know what application security is, why it is important?
What is Application Security, and why is it important?
Application security is defined as a process of encompassing security measures into the application development and design phase as a proactive approach to prevent data loss and a diverse range of exploitable cyber threats such as unauthorized access, spoofing, sniffing, malicious modification, etc.
It helps proactively understand risks and threats based on the application model and specification. It also facilitates providing a secure application foundation to counter critical to low severity vulnerabilities before any potential attacker identifies and exploits them. The primary goal of having security in each application layer is to identify critical and non-critical bugs in an ongoing and managed process.
The only way to reduce the impact or limit the opportunities of security breaches is to implement security into your software development lifecycle, also known as Secure SDLC. Today’s applications are more of a gateway and connected to various networks, clouds, etc., and carry critical data to every end-point. Hence, it is crucial to safeguard the gateway to protect sensitive data and its environment.
Secure SDLC is not different from the normal SDLC on a high-level. On a basic level, application security incorporates security, privacy features, and protection aspects into the development cycle that distinguishes the traditional SDLC.
Traditional vs. Secure SDLC:
Many organizations focus on building applications with new features and fast development processes in the past and current times. In the hassle of these, they usually forget to add security to the foundation of application design, which later makes them face the consequences of building insecure applications in the form of breach, penalties, and cyber-attack.
Traditional SDLC:
The traditional SDLC began with the research upon the application requirement and targeted user or market. The most imperative factor in SDLC is to develop feature-rich and data-driven applications/software as quickly as possible to capture the market and quick ROI.
The requirement solely focuses on the application’s features, design, and user experiences. It includes the extensive planning of the application or software foundation, e.g., application financial budget, appearances, layout, blueprint, architectural decisions, data transmission and storage, application interaction with users, and other systems or networks.
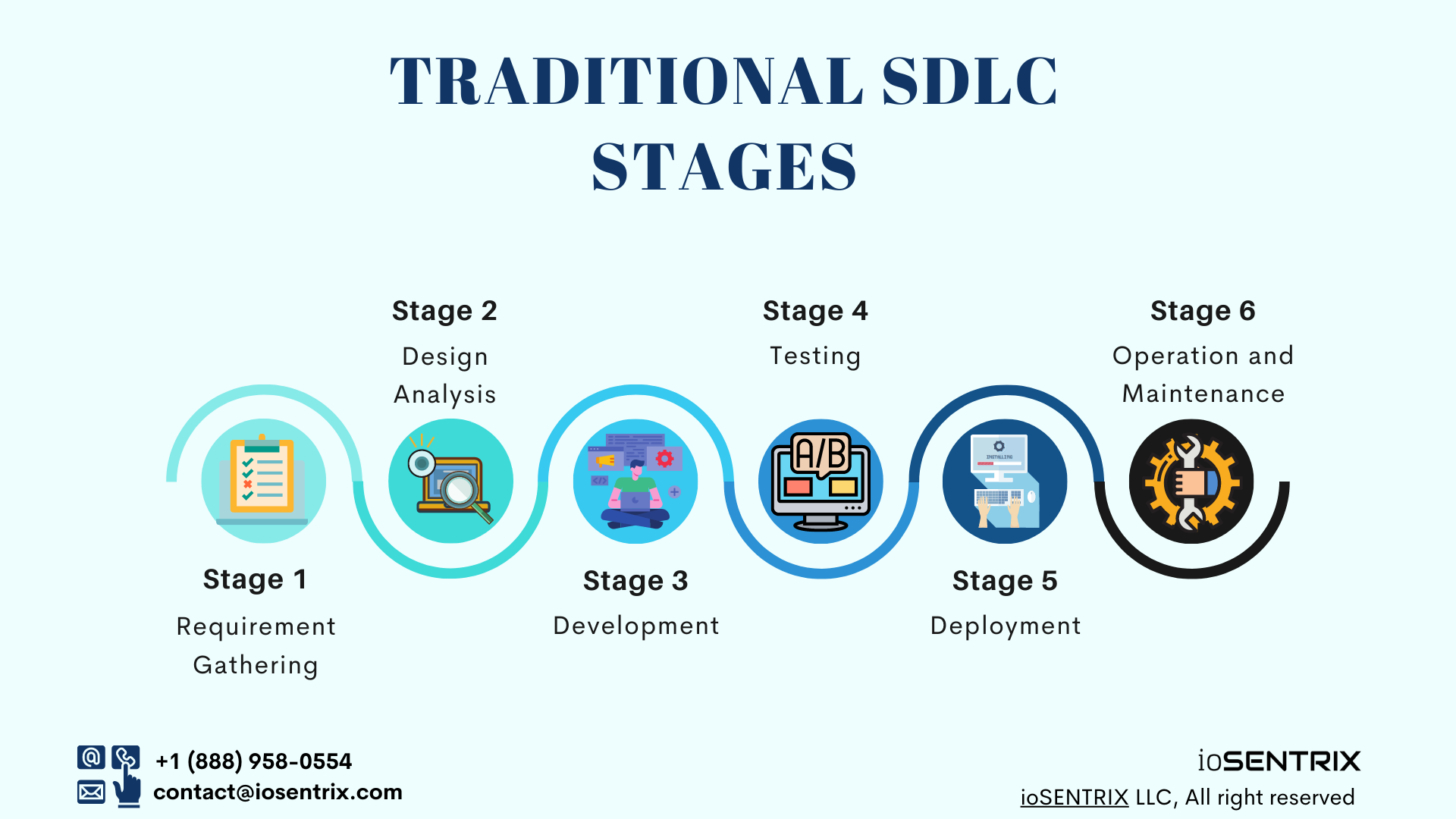
Use this link to download this Traditional SDLC Stages infographic in PDF format.
Secure SDLC:
Secure SDLC is a framework for adding the best security practices in each of the development lifecycle stages. It includes embedding security consideration into the application development requirements to the security testing and other activities till the post-development stage.
Secure SDLC is the whole package of application security and describes how an application should be built. It is incorporated when an application is developed from scratch or already in production. However, it can be done on a developed or released application as a post-security practice along with the drawback of increased time, cost, and complicated remedial process. Nevertheless, It is a more suitable option to adopt secure SDLC to in-production applications.
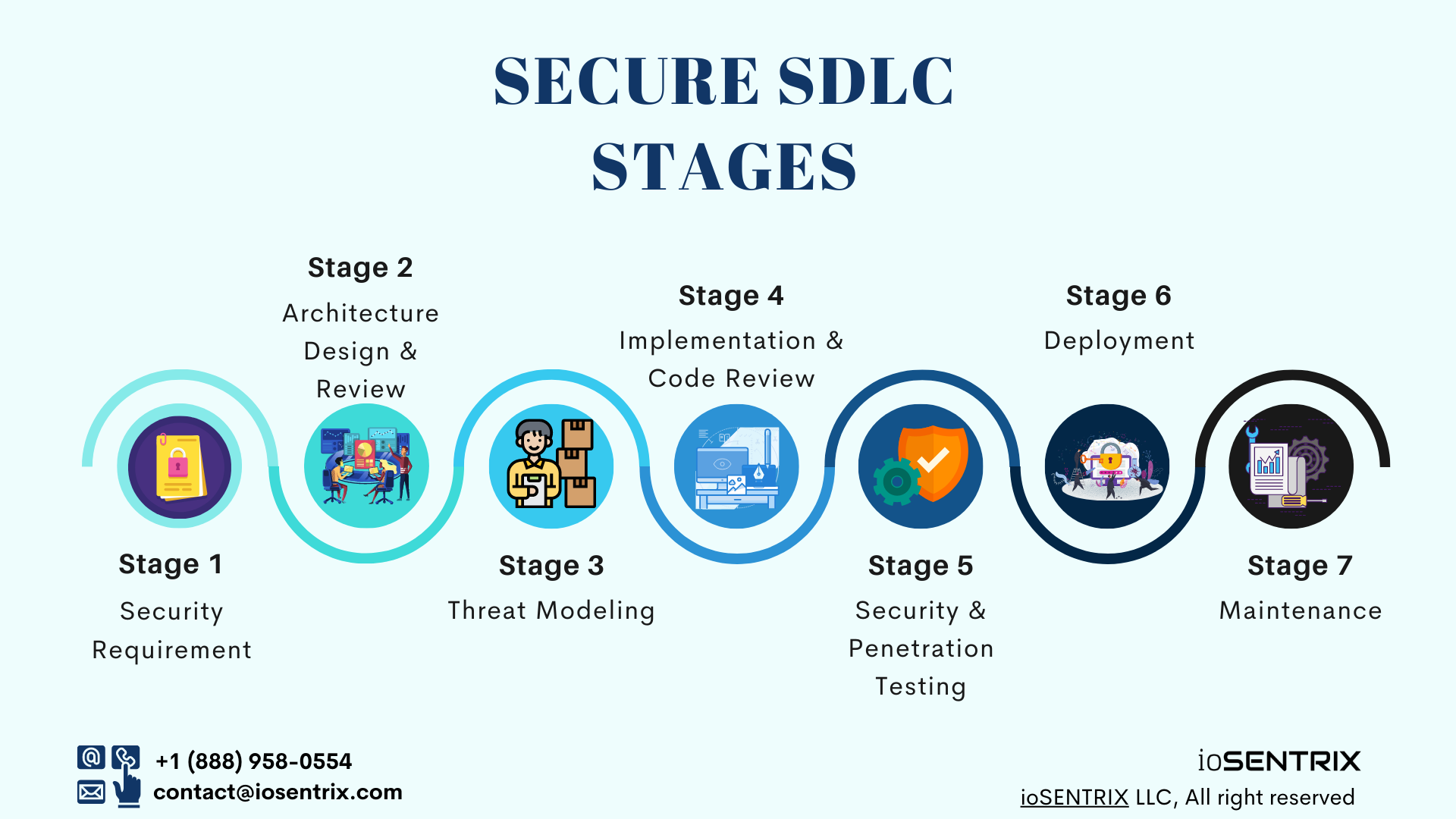
Use this link to download this Secure SDLC Stages infographic in PDF format.
Secure SDLC usually contains the following phases:
1- Security Requirements
Secure SDLC begins with the first stage of security requirement and wholly focuses upon taking the basic to advance security requirement under consideration. This phase directs and defines the kind of security necessities that must be examined before the software/application architecture is designed. Data classification is mandatory at this stage, and the development team must classify the type of data that will be collected and how they will handle the software’s data. This includes the analysis of application/software data type, legal conditions, and featured elements.
To fulfill the secure SDLC requirement stage, the collected elements are taken under attention to analyzing the critical impact of different abuse case scenarios that could trigger or present the bug to any potential cyber-criminal and open a path to exploit those bugs.
The key questionable elements include the analysis of the following:
- Does the data management come under any regulatory bodies such as HIPAA, PCI, SOX, etc.?
- What’s the data classification according to the company’s policies?
- What would be the data flow, and how would it comply with the rights commanded by GDPR, CCPA, DPA, etc.?
- What would be the pattern of data encryption at rest and in transit?
- How will server-side or client-side encryption implement over the data?
- Who will have access to data, and whether or not data will be shared with any 3P? If yes, what amount of data will be shared or transferred?
- The development and security team must plan to ensure authentication features based on the application purpose and design. For instance,
- How should the user lockout policy work?
- Does the application need any enforced MFA or TFA?
- How resilient should the application design be to prevent brute-forcing, credential stuffing, etc.?
All such things are decided in the first stage of secure SDLC.
2- Architecture & Design Review:
Over the years, it has been observed in most of the breaches; there are 60% of the mistakes in application/software design and 40% of the implementation flaws that lead the software to suffer a breach. Therefore, if the problems are encountered and controlled at the design phase, it is likable and straightforward to resolve the issues that come on to the later stages.
The application design and architecture review phase serve the same purpose as discussed above. It is a complete assessment of application/software design to put security on the software architecture and pull out the flaws initially. It works as a starting point for software designers and architects to think about security as a foundation and understand what they should consider while building software.
Typically, this phase defines the software architecture pattern, technologies, and techniques required to design and build the application in traditional SDLC. Similar activities are performed in secure SDLC while concentrating on choosing specific secure code standards and practices, development model, security framework selection, APIs, and SDK to be used, cloud services with security best practices to be incorporated. This review focuses on identifying design flaws which are expensive to fix at a later stage.
Furthermore, during this phase, a roadmap is prepared for both front-end and back-end services focused on the secure user experiences, data flow, data delivery, components or database communication, and interaction to the system and network to ensure the application works in a secure ecosystem.
As a part of secure architecture review and design, it also directs the development team to focuses on embedding security into each of the services and requirements to be delivered, such as:
- What industry best practices need to be followed?
- How would the PII flow throughout the system or other sensitive credentials be handled?
- How would the authentication and authorization process work?
- How would the services be authenticated to each other?
- What would be the data transmission process?
- How likely would the logging information be beneficial?
- Which cloud service or web server will be utilized?
- What cryptogram mechanism will be followed for data security, and how are crypto keys managed, stored, recycled, revoked, etc.?
- How are the trust zones defined in the software architecture?
- What are the critical rotation and revocation policies?
3- Threat Modeling:
Once the security requirements are gathered and the architecture design is finalized, threat modeling is conducted.
In this secure SDLC phase, a threat enumeration is performed to determine all potential threats and attacks that might be possible. Additionally, all the controls that prevent certain attacks are also identified. For computation, a traceability matrix is prepared to define all the assets, features, controls, possible attacks, and functionality of application requirements and deliverables with the known business impacts and security considerations.
The end goal of the threat modeling behavior is to map out all the potential threats and risks through an appropriate risk management assessment to have a clear picture of gaps in order to mitigate, eliminate, transfer or accept the risk according to their severity level.
Besides the traceability matrix, all possible threats are enumerated according to the defined features and assets. For instance,
- What are the security measures out there in place to control remote attacks?
- Are the security controls in place adequate enough?
- What kind of immediate access can any attack get if he manages to bypass the security?
- Are there any missing security controls that can leverage the attack to break in? If yes, then how?
- What critical security gaps must be restricted, and what are their impacts on the business and the application?
4- Implementation & Code Review:
It is 40% of software implementation mistakes that lead to a security breach. Like software architects must know about secure architecture, it is crucial to continuously train developers to write secure codes. A well-trained and security-conscious developer would not write vulnerable code. If they have basic security concepts (at least OWASP top 10 for web-dev work), it will be easy to avoid such bugs and problems while developing the code.
During the implementation phase, codes are written to achieve finalized requirements and design. Developers are guided with safe coding methodologies to create the necessary units, modules, interfaces, and GUIs. Similarly, some of the available IDEs and plugins are considered to help boost secure code development. All the input and output components are executed in this phase, and codes are repeatedly reviewed to identify bugs and block present vulnerabilities or flaws overlooked in the source code.
As penetration tests or other security assessments cannot detect every flaw in the architecture and codes, similarly to get detailed coverage over code and 100% verification, it is essential to review the code and identify bugs through secure code review practices. In the case of third-party code development or open-source software, it becomes crucial to inspect and detect vulnerable and malicious embedded code into the software that might have been overlooked or forged by the 3P. For e.g. there is a high probability of software stack running an older and vulnerable version of open source library that the development team might not be aware of.
For this, automated, manual code review and software composition analysis is performed. As compared to automated code review tools, manual code review is performed on high-risk areas. Automated code reviews are faster and provide better coverage to the code in a short span but tend to produce many false positives. It is also a good idea to integrate a static analyzer in CI/CD pipeline to break the build generation or prohibit the code commit as soon as a Critical or high-security issue is detected. In some cases, when automated tools are fine-tuned, they have good and near to accurate results. But, when it comes to validating business logic flaws, it requires reviewing the code manually, as static analyzer tools often miss them.
There are plenty of common software security weaknesses and best coding practices under the CWE and CWE Top 25, CERT for the standard for secure programming language guideline, CVE for specific product/software’s exposed vulnerabilities, PA-DSS for payment application best security practices, and other OWASP Top 10, DISA STIG industry standards.
5- Security & Penetration Testing:
The testing phase is begun when the implementation is closed, and codes are reviewed thoroughly according to security best practices and standards. In the testing phase, the software is wholly examined for defects that might have been overlooked in earlier secure SDLC phases. The security tests are performed focusing on unit test cases to validate the software security, business logic and quality.
To ensure the software’s safety and reliability, the security team must test the developed piece of software through penetration testing or hire a third-party to do so. Penetration testing concentrates on infrastructure-related issues as well as business logic, fuzzing, third-party libraries, OWASP top 10, user data authentication, processing, access, and privileges tests.
Get to know more about penetration testing from our detailed “What is pentest?” blog.
After pentest, other security assessments with broad or beyond pentest scope would greatly help to identify other security issues such as configuration flaws, lack of best industry practices etc.
6- Deployment:
After the software is adequately reviewed and fixed with no remaining bugs within, it is time to release and deploy the software for the users. This secure SDLC phase is mainly taken out as a pre-deployment phase to identify vulnerabilities that could have occurred or missed while integrating and configuring servers, databases to overall infrastructure and network. This is the last stage where all the final testing is conducted to ensure full-stack security.
The primary purpose of this audit is to stimulate an attack to analyze the security configuration of infrastructure (network, system, server) that any potential attacker can compromise through any TTP. Additionally, the audit helps evaluate application resiliency, defensive capabilities, and application behavior in a stimulating environment of automated and manual attacks. It includes the holistic test with a complete solution and configuration of network infrastructure, application server, and network assessment.
The deployment phase carries out configuration audits such as cloud security audits and full-stack security review tests over a fully deployed product-like environment. Some companies often carry out DOS (Denial of Service) and DDOS (Distributed Denial of Service) attack testing to understand or modify the software resiliency.
7- Maintenance:
Maintenance is the last and continuous stage of secure SDLC that is performed promptly after the release of software/application. It focuses on improving the application and satisfying the requirements gathered in the pre-development phase. Once the software or application is appropriately deployed and released for customer use, it requires continuous support from the manufacturers to defend against upcoming threats and timely upgrades.
As the technologies and applications evolve, new flaws and new exploitation techniques come; the maintenance must go on in the form of annual penetration testing, patch management, third-party risk assessments, frequent vulnerability assessments, open-source security audits, and on-demand compromise assessments.
Read our blog about the necessity of third-party risk assessment
Final Thoughts
The sophisticated nature threat actors have rung the bell to re-evaluate the approaches that organizations follow to mitigate the vulnerabilities and protect their assets and application. Application security is not something you can acquire or utilize by incorporating defensive tools into your application/software. Tools and technologies help to monitor the threats targeting the organization; however, they do not facilitate blocking threats and vulnerabilities originating within the software due to missing or no security controls. Application security can only be achieved through implementing a secure SDLC method to the software.
Get in touch with ioSENTRIX to boost your application security or train your development team. We provide comprehensive application security services, including Architecture Review, Threat Modeling, Penetration Testing, Code Review, and Full-Stack security. Whether it’s Waterfall or Agile, we can help integrate a holistic security model into your SDLC.
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter