
Malware or malicious software refers to files or programs, designed to harm networks, computers, or servers. It includes a variety of harmful software intended to infiltrate and compromise systems. Understanding malware’s complexities is essential for individuals and businesses to respond and prevent these malicious activities effectively.
Common forms of malicious software include worms, viruses, ransomware, Trojan horses, adware, and spyware. These programs can encrypt, steal, and delete sensitive data, disrupt or hijack core computing functions, and monitor user activity.
In this guide, we’ll explore the world of malware, its destructive capabilities, infection methods, and the different types of malicious software that can damage computer systems and compromise confidential information.
Malware primarily aims to exploit vulnerabilities in computer systems, gain unauthorized access to sensitive information or disrupt normal operations. It can be distributed through email attachments, malicious websites, infected software downloads, or even physical devices like USB drives.
Once a system is infected, malware can carry out a multitude of malicious activities, such as stealing personal data, corrupting files, intruding network connections, or using the compromised device as a platform for launching further attacks.
The term “malware” was first coined by computer scientist and security researcher Yisrael Radai in 1990, but the concept existed long before that. One of the earliest known examples was the Creeper virus, created in 1971 by Raytheon BBN (formerly BBN Technologies) engineer Robert Thomas as an experiment.
Creeper was one of the earliest pieces of malware, designed to infect mainframes on ARPANET, which was the precursor to the modern internet. Unlike today’s threats, Creeper didn’t mess with the system’s functions or steal any data. Instead, it simply hopped from one mainframe to another, displaying a cheeky message that read,
“I’m the creeper: Catch me if you can.”
Later on, computer scientist Ray Tomlinson took Creeper and made a few tweaks to let it replicate itself, which is what we now call the first computer worm.
From there, malware started to become more common, especially with the rise of personal computers like Apple and IBM PCs in the early ’80s. This trend really picked up pace with the launch of the World Wide Web and commercial internet in the ’90s. Since then, malware and the ways to defend against it have both gotten a lot more sophisticated.
Malware possesses a wide range of destructive capabilities, from simple annoyance to severe system compromise. Some types of malwares can render a device or network unusable, while others can discreetly gather sensitive information, such as login credentials or financial data, without the users being aware of it.
Ransomware is a pretty severe type of malware. It locks up your files and then demands a ransom if you want to get them back. This kind of attack can shut down entire businesses, causing big disruptions and costing a lot of money.
DarkSide, REvil, Conti, LockBit, and Maze are ransomware groups recognized for their advanced exploitation techniques. They target vulnerabilities in software, networks, and human error to gain unauthorized access to systems.
These methods enable them to bypass security measures and infiltrate organizations, increasing the likelihood of successful attacks. Consequently, organizations must stay informed about the latest vulnerabilities and promptly apply patches and updates to mitigate the risk of exploitation.
Another kind of malware that’s become more common recently is spyware. As you might guess from the name, spyware is all about secretly spying on what you do online. It can log your keystrokes, take screenshots, and even turn on your device’s microphone and camera without you knowing. This type of malware is a big privacy threat and can lead to serious issues like identity theft or blackmail.
DarkHotel, CoolWebSearch, Olympic Vision, and Hawkeye are some of the most dangerous spywares that pose complicated security problems for businesses and organizations.
These spywares compromise confidentiality by stealing banking details, business passwords, and emails of the company executives. Once the data is accessed, hackers can then easily utilize the details to exploit the security infrastructure to meet their notorious targets.
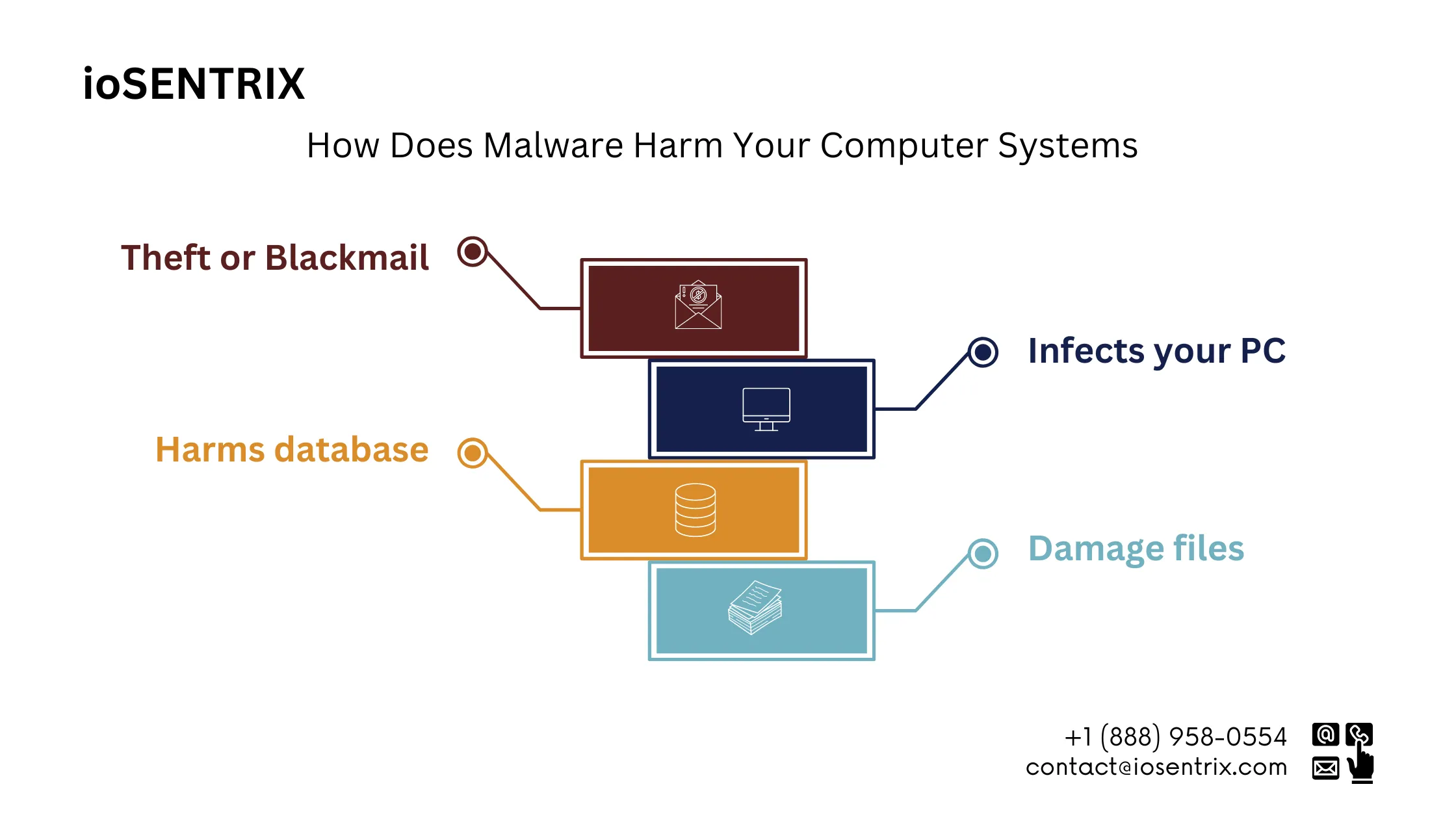
Adware might not be as dangerous as some other types of malwares, but it can still be a real headache. It’s often sneaked into legit software and then bombards you with annoying ads on your device. These ads can slow things down, eat up your bandwidth, and just make your whole experience less enjoyable. Adware sometimes tracks your browsing habits to gather personal info for targeted ads.
Malware infections continue to pose a significant threat to cybersecurity worldwide, with cybercriminals constantly evolving their tactics to bypass traditional security measures. To overcome these malicious activities, it is essential to delve deeper into the various entry points through which malware infiltrates systems.
Phishing emails: Malicious emails that trick users into clicking on links or downloading attachments containing malware.
Infected websites: Visiting compromised websites or clicking on malicious ads can lead to malware infections.
Software vulnerabilities: Exploiting security flaws in outdated or unpatched software is a common method for malware infiltration.
Drive-by downloads: Automatically downloading malware when visiting certain websites or clicking on infected ads.
Malvertising: Displaying malicious advertisements on legitimate websites that infect visitors’ devices.
Malware often sneaks in through social engineering, where cybercriminals trick people into sharing sensitive information or taking actions that let the malware in. This highlights how crucial it is to have not only strong tech defenses but also to educate and make users aware to prevent these attacks.
Read more on our Blog: Ransomware vs Malware
Malware appears in many different forms and targets weaknesses in computer systems and networks. By understanding these threats better, people and organizations can strengthen their protection against cyber-attacks.
These are self-replicating programs that infect files and spread from one system to another. They can cause significant damage, corrupting or destroying files in the process. Viruses often attach themselves to executable files and are activated when the infected file is executed.
Unlike viruses, worms don’t need you to click or do anything to spread. They sneak through network weak spots on their own, clog things up and slow them down. They can zip across networks fast, infecting lots of devices in no time at all.
Named after the wooden horse from Greek mythology, Trojans disguise themselves as legitimate software. Once installed, they grant unauthorized access to an attacker, enabling various malicious activities. Trojans are commonly used to create backdoors in computer systems. This allows cybercriminals to remotely access and control compromised devices.
This malware is designed to encrypt files of a victim’s system and demand a ransom for decryption. The malicious activity has been increasing in recent years with both individuals and organizations at its target list. These attacks result in substantial data loss, financial demands, and can severely damage the reputation of the affected entities.
A rootkit is a program that provides threat actors with administrator-level access to a victim’s system. Once installed, it grants root or privileged access, allowing the attacker to control the system.
Also known as system monitors, keyloggers record nearly all user activity on a computer. This includes writing emails, visiting websites, opening programs, and typing keystrokes.
This involves using someone else’s computer to mine cryptocurrency without their permission, often through phishing attacks or by embedding malicious code into websites that run automatically.
Logic bombs are malicious programs designed to activate and inflict damage upon meeting specific conditions. They remain inactive until triggered by predefined events, such as a user executing a particular action at a specified date or time.
Exploits leverage vulnerabilities, flaws, or weaknesses in a system’s hardware or software. Unlike social engineering, which manipulates users, exploits target technical vulnerabilities to gain unauthorized access and perform malicious actions, such as executing arbitrary code within a system.
Spotting malware early is important to minimize its impact and prevent further damage. By familiarizing yourself with the signs and symptoms of malware infections, you can take immediate action to mitigate these threats.
Sudden loss of disk space.
Noticeably slower computer or device performance.
The appearance of a blue screen of death.
Frequent system crashes or freezes.
Altered browser settings and unexpected redirects.
Increase in unwanted internet activity.
Disabled security features in firewalls and antivirus software.
Changes in file names and sizes.
Pop-up advertisements.
Programs opening and closing on their own.
Ensure compliance with policies and best practices for securing applications, systems, and appliances. Implement unique passwords of at least 16 characters and utilize a password manager. Promptly apply patches to address security vulnerabilities as updates are released.
Establish advanced backup processes to safeguard against data loss. Given the prevalence of rapid, network-based ransomware and cyber-attacks, robust data protection solutions are imperative.
Employ a layered defense strategy incorporating next-generation endpoint monitoring tools like AMP for Endpoints, next-generation firewalls (NGFW), and intrusion prevention systems (IPS) for effective security across endpoints, email, and DNS layers.

Educate users on identifying trustworthy sources and recognizing phishing attempts and other scams. Implement two-factor authentication as an initial security measure.
Minimize outbreak risks by segmenting your network with effective network segmentation practices.
Monitor network traffic closely with advanced analytics to gain deeper insights into network activities. Utilize real-time threat intelligence sources to stay updated on cybersecurity threats.
Create and practice incident response plans to ensure preparedness and effectiveness in handling security incidents.
Implement a zero-trust approach to secure access across users, devices, APIs, IoT, microservices, and containers. Verify trustworthiness before granting access to protect the workforce, workloads, and workplace effectively.
Understanding and combating malware requires a comprehensive approach that includes technical defenses, user education, and proactive measures. By staying informed and vigilant, individuals and businesses can protect their systems from the ever-evolving threat of malware.