Ransomware is a type of malware that locks you out of your files once it’s on your computer. It encrypts the files, and the cybercriminals behind it demand a ransom to unlock them. Ransomware has become one of the biggest cyber threats to organizations, sometimes even pushing companies into bankruptcy.
In this article, we’ll look at what sets ransomware apart from other malware, how it ends up on your device, and how you can prevent it.
Malware includes any harmful software designed to damage or disrupt a computer system, such as viruses, trojans, spyware, adware, and more.
Ransomware is a form of malware that locks your data or systems, demanding a ransom to release them. However, paying the ransom doesn’t guarantee the return of your data. If attackers find out you’re willing to pay, they might launch additional ransomware attacks. Sometimes, even after paying, the files remain encrypted.
Malware is of various types including viruses, spyware, trojan horse, worms, adware, and crypto jacking. These steal the data, and use it to exploit computer systems and networks.
Virus: This type of malicious software infects other programs and harms your computer system. It needs a host, like a file or program, to spread and can’t exist on its own.
Trojan Horse: This software runs on your device without your knowledge, pretending to be a legitimate application or file.
Spyware: Collects your information without you knowing and sends it to someone else. It can even use your computer’s camera to spy on you or track your keystrokes with a keylogger.
Adware: This software displays annoying ads but doesn’t install anything on your device or capture keystrokes like spyware does.
Worm: A worm spreads itself across networks without needing to attach to other files or programs, infecting a large area on its own.
One prevalent method involves the dissemination of malicious email attachments and links. Cybercriminals deploy a high volume of emails containing suspicious links or attachments, anticipating that recipients will be lured into engaging with them. Interacting with such elements can pave the way for ransomware infiltration.
Another avenue through which ransomware can infiltrate your device is via online advertisements. While browsing, encountering a questionable pop-up and clicking on it hastily can swiftly result in a malware infection.
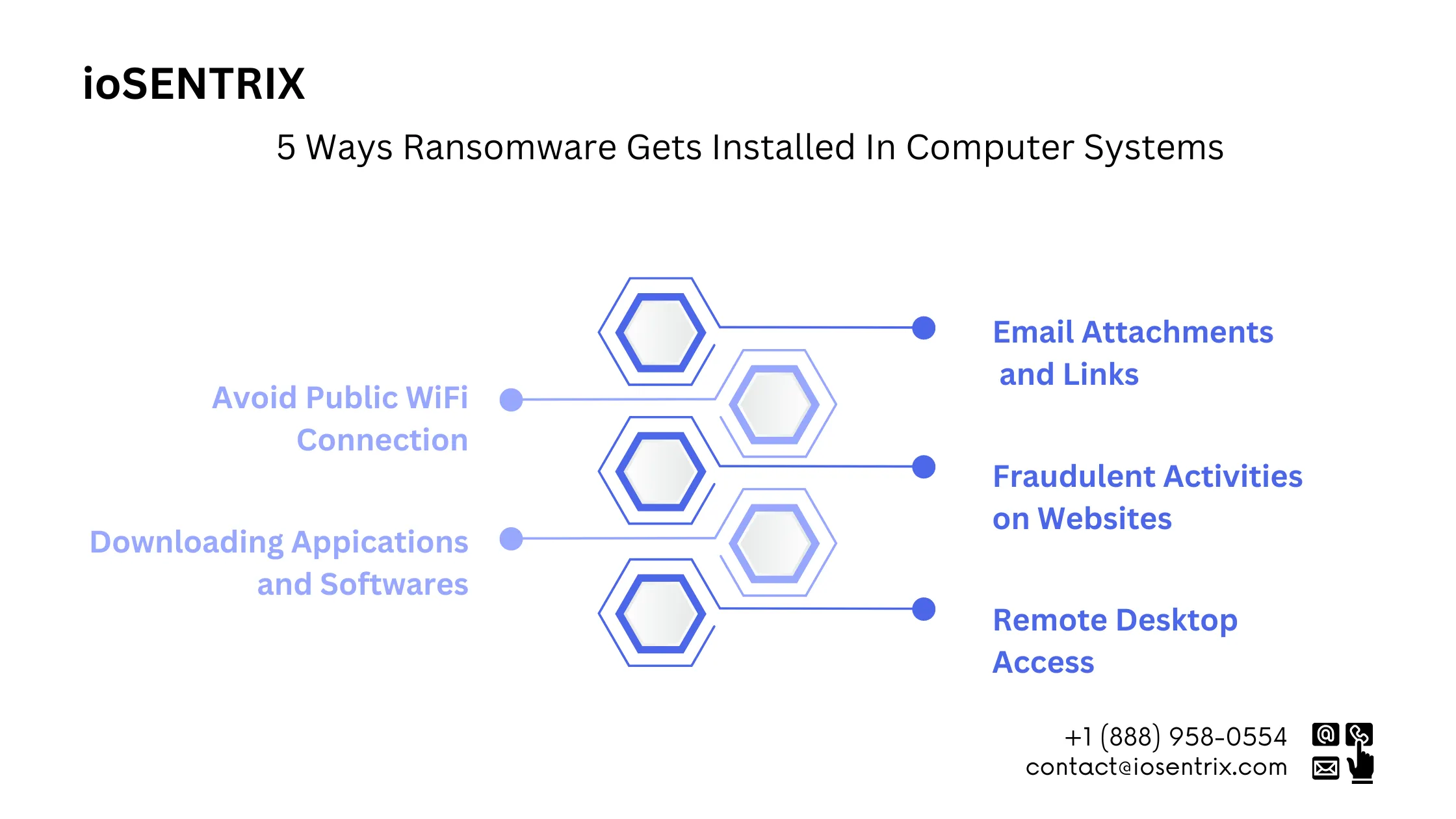
It is strongly advised against downloading applications or software from unofficial sources. opt for reputable platforms like the Google Play Store or Apple’s App Store to uphold the security of your system.
The utilization of public WIFI networks can also expose your device to potential risks. Should a network or a device connected to it be compromised by ransomware, your device could be the next target for a malware attack.
An RDP attack allows hackers to gain unauthorized access to the system, with the aim of stealing data or installing ransomware. By gaining remote access to the computers, hackers can delete data or disable security software.
A Virtual Private Network (VPN) can be used as a protective shield against RDP attack. It encrypts the user-server connection, making it harder for hackers to intercept databases.
Regularly updating your Operating System (OS) and software is extremely important for protection against ransomware threats. Updates typically include security patches that help mitigate vulnerabilities, reducing the likelihood of potential infections. Neglecting these updates exposes your systems to increased security risks. It is advisable to stay current with updates and leverage the latest versions to increase your system’s security.
In addition to using strong passwords for all accounts, enabling Multi-Factor Authentication (MFA) provides an added layer of security. MFA necessitates supplementary authentication beyond passwords. This additional security measure is effective to limit unauthorized access, even in cases where cybercriminals gain access to your password.

Regular backups ensure that data is consistently saved and can be restored in the event of an attack. It is crucial to store these backups in secure, separate locations, such as cloud storage or offline drives, to prevent them from being compromised.
Regularly testing these backups ensures their reliability and integrity, allowing organizations to quickly recover data and resume operations with minimal disruption. This proactive approach not only safeguards critical information but also reduces the impact of potential ransomware and malware incidents.
Safeguarding your systems against ransomware and malware threats involves downloading software solely from legitimate sources. Utilize official websites and trusted app stores for software acquisitions, avoiding third-party platforms and unverified links. Verifying the authenticity of software sources is crucial in preventing ransomware infections arising from malicious or altered applications.
Investing in Endpoint Detection and Response (EDR) solutions is a crucial strategy for safeguarding against ransomware attacks. EDR tools offer real-time monitoring and threat detection capabilities on endpoints, allowing organizations to swiftly identify and respond to suspicious activities that could indicate ransomware infiltration.
Ransomware poses a substantial risk to organizations, potentially leading to data encryption and operational disturbances. Providing employees with comprehensive training on cybersecurity best practices is vital to strengthen organizational resilience against cyber threats. Conduct regular training sessions to enable employees to recognize phishing emails, refrain from clicking on suspicious links and attachments to enhance organization’s overall security plan.
Remember: While prevention is the best defense, organizations must also be prepared to respond effectively to minimize the impact of a ransomware attack. By combining proactive prevention measures with a well-defined incident response plan, organizations can better safeguard themselves against the ever-evolving threat of ransomware.
For comprehensive protection against evolving cyber threats, consider partnering with ioSENTRIX. We help you defend your organizations against evolving cyber attacks with our security solutions and professionals. Stay ahead of cyber threats with ioSENTRIX and protect your business from potential security breaches.