
In the previous blog post on how OSINT is used in cybersecurity, we discussed what OSINT is, who uses it, and how it helps launch a cyber attack.
In this second and last blog post, we have expanded the Open Source Intelligence (OSINT) realm to dive deeper into the publicly available information that helps initiate a cyber attack. This blog post focuses on passive data mining from the Internet- specifically from the attacker’s perspective without simulating or running any fancy tools or scripts.
So before we jump into OSINT, it is essential that you learn how the cyber attack cycle works, what cybercriminals do with all information, and how the overall collected data adds value to the attack process.
The foundation of the cyber attack cycle is based on five processes, i.e., Reconnaissance or information gathering, attack surface analysis, also known as vulnerability analysis, exploitation, maintaining access, and covering tracks.
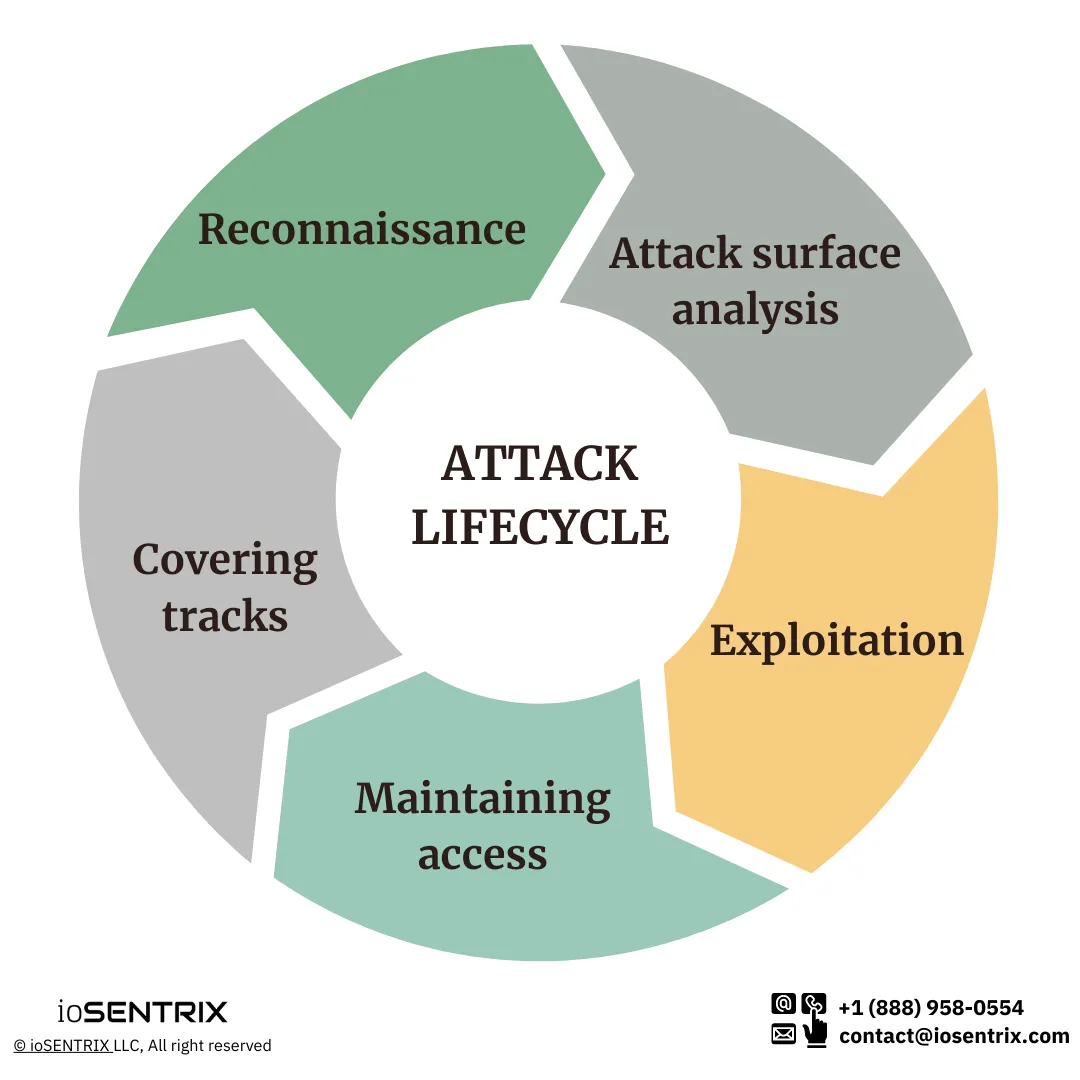
Reconnaissance, also known as information gathering, is the first stage of attack processes in which the information is collected. This is the stage where OSINT helps cybercriminals gather sufficient data about their targeted business, networks, applications, or individuals. Over here, they scrutinize the information about their target and collect maximum data about them which they want to go after.
For example, if an attacker wants to hack an application, at this initial stage, they would gain information about the application platform, framework, languages, databases, etc.
Once attackers have enough data, they perform the attack surface analysis. In which they observe the entire threat landscape and try to find out common vulnerabilities affecting the system or landscape. Such as what vulnerability would help them gain access to the system, what they can do to bypass or circumvent the security control, how they can chain up vulnerabilities to do the potential harm.
As soon as they identify the valuable attack point, they go ahead and exploit them to gain access. Depending on the motives and goals, attackers might infect the system with malware or ransomware to take hostage the compromised system, steal data, install ransomware or just move laterally to stay in the network or system for the future or their desired purposes.
The malware or botnet connects the compromised system with the attacker command and control (C2C) server through which the malware takes instructions and does the data exfiltration, escalate privileges, and other malicious activities. All these activities are done in the post-exploitation process.
Lastly, when the activities are done, and the attacker’s goal is achieved, the adversary ensures to cover their tracks, remove traces and logs of their activities so no one can find out who the attacker was and what he did.
Consequently, we can grasp that the gathered information is the foundation for all cyber attack processes because you need the attack surface to launch an attack. And for that, you need to have data, and that is where OSINT contributes.
Now that you have learned the basics of cyber attacks and know how the attack lifecycle works, let’s move ahead and gather some information from the Internet. OSINT has no hard and fast rule, and we do it daily in the form of google searches. There is no specific or standardized approach to OSINT, but you must make search engines your best friend at the beginning of your OSINT journey.
So now, we are taking an example of an Industrial Control System; nonetheless, with the same techniques and approach, you can find information about any other system, be it IoT devices, web applications, or other information technology systems or networks.
Let’s assume you want to target the Industrial Control System of ABC company. As an attacker, you might have no idea or information about the ICS/OT system. So the first thing you need to do is go on the Internet and research how ICS systems work and write down the well-known ICS and SCADA systems’ TCP and UDP communication ports. With some low-effort google search, you can indeed find out some of the standard ports.
For instance, in the below Figure 1, you can see ANSI C12.22 protocol uses port 1153, BACNet uses 47808, Siemen S7 PLC controllers use 102 ports for their communication, and so on.
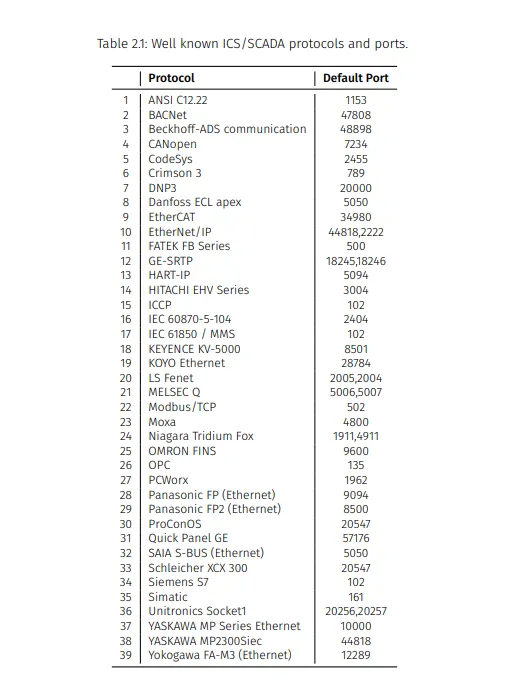
Figure 1
All such information about ICS and SCADA system protocols are readily available over the Internet, which you can utilize for your basic understanding. You may head over to YouTube to learn the ICS system working for your keen understanding and take the knowledge that is just a few clicks away. You can also align the gathered information and put them together to get a clear picture of the target and examine the particular asset to target.
Now, when you have got the idea of the ICS/SCADA system, it’s time to move ahead on Shodan.
Shodan is also a search engine, unlike Google, DuckDuckGo, Bing, other web search engines; shodan indexes webcam, IoT devices, smart devices, and everything connected to the Internet. It does so by connecting to those devices on each port. Through connecting to ports, it collects their banner and identifies the services running on those ports.
In addition to it, shodan offers a whole category or Industrial Control System which you can opt for to understand what ICS systems are and what different kinds of ICS systems and components, protocols, etc. are there that they use and much more by just clicking and exploring all devices information available on the Shodan, (See figure 2).
Figure 2
Now, let’s take an example of the port number we gathered in the first place; in the following search bar of figure 3, we have queried for port 502 on shodan, and in return, it showed almost 14k devices connected to the Internet with open port number 502 along with the device banner, operating system, location, and company name which is utilizing the product.
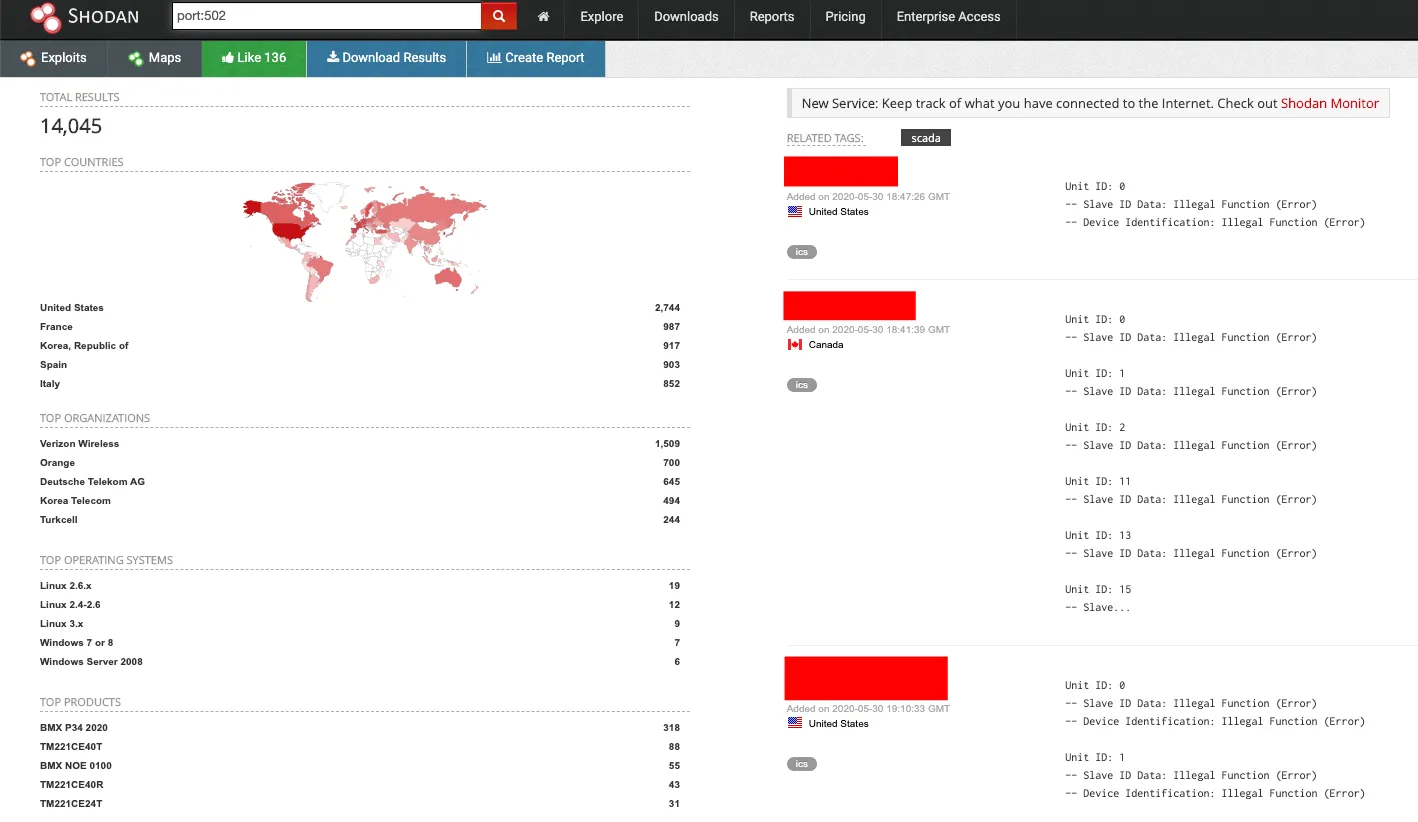
Figure 3
Being an attacker, all this data available in simple form is essential to you. Here you can notice that you did not interact with the device and collected the data passively, and quickly you got to know which technology is being used on the specific port across the Internet.
Moving ahead with another valuable option on the shodan. In figure 4, we used another prospect on shodan, which allows you to scan a particular system connected to the Internet. Here, shodan scanned the particular system and recognized the open port along with services operating over them.
Moreover, it shows the running services, identified vulnerable services against known vulnerabilities, and publicly impacted CVEs. For instance, as mentioned, Microsoft HTTP API version 2.0 runs over the TCP port 84, which is vulnerable to the mentioned CVEs.

Figure 4
Again, being an attacker, these CVEs are valuable for you because, at this point, you know which of the services suffers from the vulnerabilities, and also, you have their identified CVEs. Hence, with a bit of effort, you can actually compromise these services. All you have to do is download free or paid penetration testing tools, find the CVEs, compile the exploit, and you are ready to target the server.
Eventually, you will be able to crash the server or device, gain access, or do other potential harm. Similarly, by exploring more options on shodan, you can find some IP addresses and other usable data.
To make OSINT more understandable, we have used another OSINT tool named Censys to analyze the IP address. First, we searched for a particular IP address (See Figure 5.) to know which device IP address it is and who owns it.

Figure 5
With a quick search, we found that this IP address is a SCADA engine owned by a North American company using the BACnet protocol to access control system on the SCADA server over the 47808 port. Additionally, you can abuse all this information by quickly identifying the contact information such as who owns the IP, register the IP address against the company, their email addresses, phone number, physical addresses, and other relevant information with the same IP address, and Censys tool (See figure 6.).
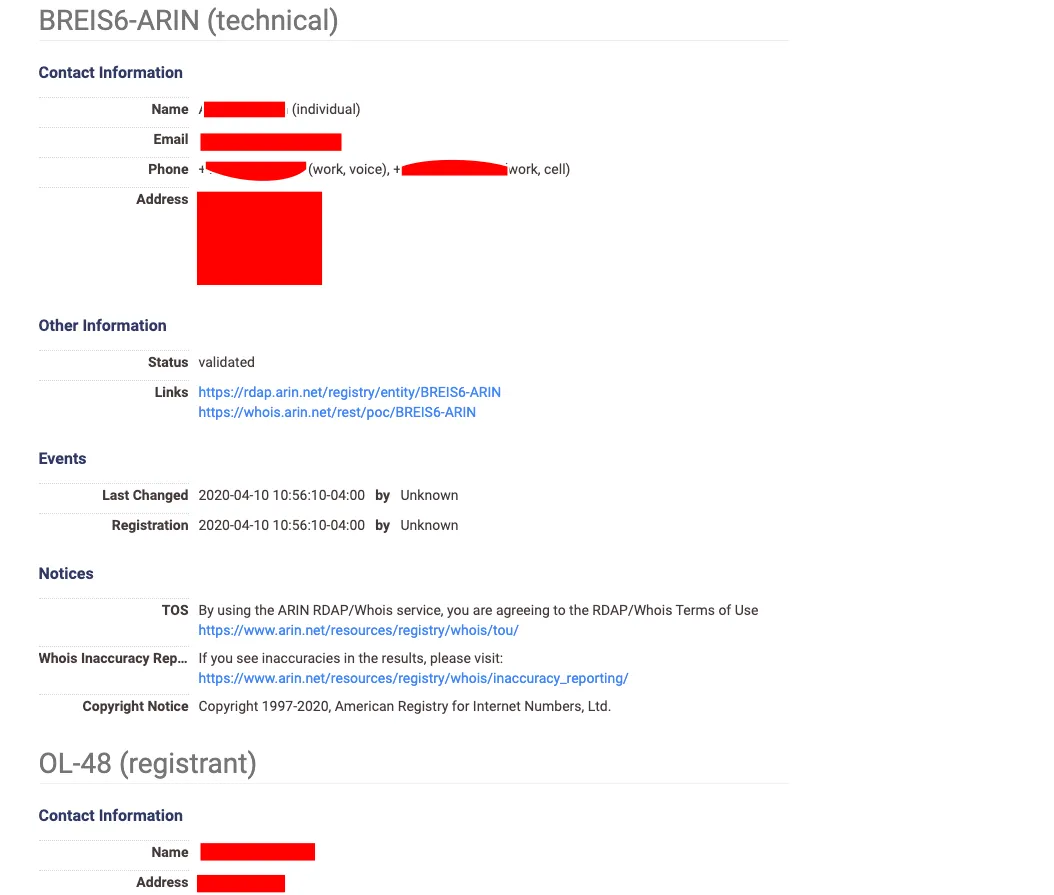
Figure 6
Now that you have plenty of information about the systems, services, technologies being used within the company, IT department, etc., you can do many things to launch an attack using this data. All of them are again valuable to you; being an attacker, you already have an email address which you can check through Have I Been Pwned to verify whether the email address has been breached in any cyber incident or not.
If it has been breached, you can go to a similar website named Dehashed, a search engine just like Have I been pwned, that offers further information such as clear-text passwords, password hashes of all email addresses that got breached in cyber incidents.
So as an attacker, you have the email addresses and clear-text passwords. Even if you get the password hashes, it is easy to get clear text against those hashes. This is because various online tools convert the hashes into clear text through the rainbow table and provide plain text against those particular hashes.
Now, you have the email addresses, passwords, and other information. There is a high chance that the individual uses the same password on all their devices, systems, and accounts, so you can easily brute force the password or perform credential stuffing attacks and impersonate them on other services. Moreover, you can launch a phishing or spear-phishing attack against those emails or use those emails as well (after successfully compromising the account via brute force and other password cracking methodologies).
Other than this, everything is available on the Internet; all you need to do is dig deeper and search smartly. You can also find out the default passwords of the SCADA system from the Internet. In many data breaches, cyber-attacks were successful because of the default password practices on the enterprise devices. The Internet has a wealth of data, and people have compiled many passwords list (See Figure 7.) based on the vendor and devices. Therefore, you can also use this attack vector of brute-forcing default ID and password to authenticate the access as an attacker.
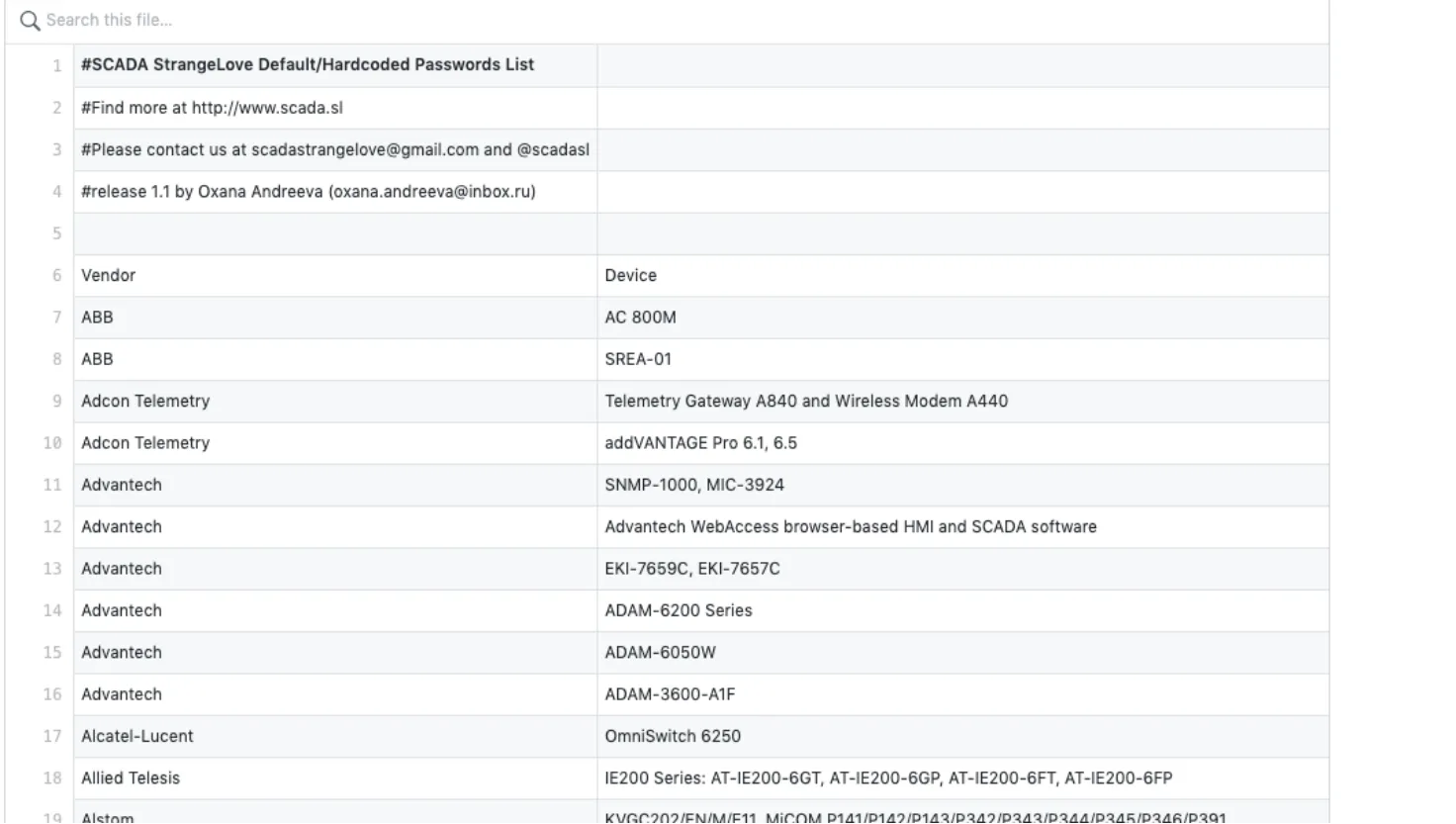
Figure 7
Last, how can we forget about google dorks? If you want to ace the art of OSINT, add google dorks on the top of the list. In below figure 8., we are searching for the Siemens S7 series PLC controller. We knew the specific URL of the s7 series; therefore, we used that with the dork “inurl:”.
If you do not know about any particular controller’s URL, worry not; this information is also available over the Internet, and you can get them with some queries and clicks.
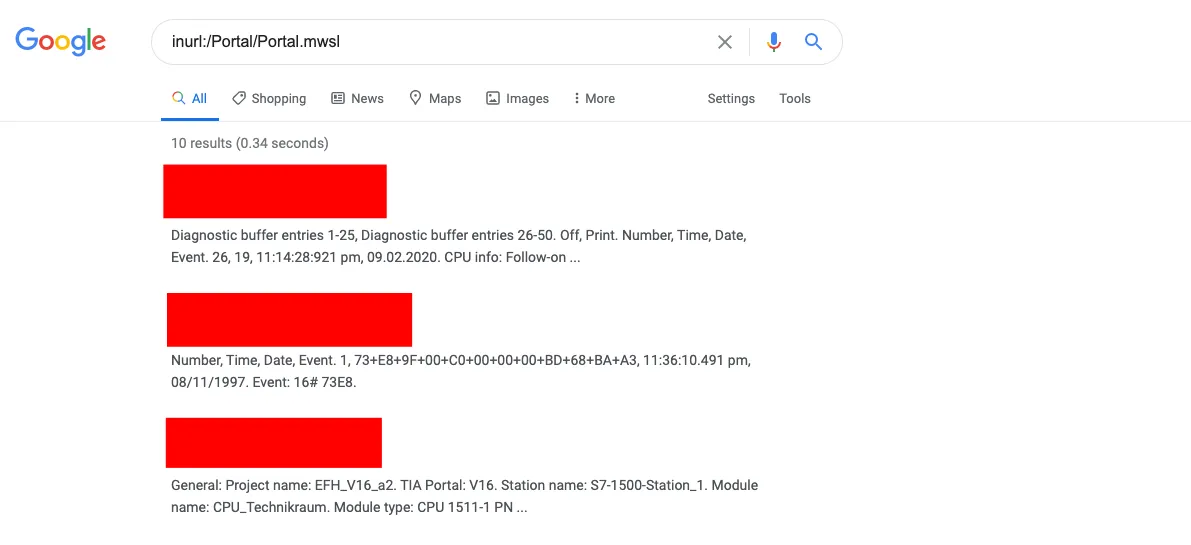
Figure 8
With the dork, we came across multiple Siemens PLC controller export, which is publically available and to step ahead, we connected with one of them. Fortunately, after connecting to it, we come across that it leaks a lot of information such as IP address, mac address, default router, network connection name, network interfaces and their speed, and other sensitive information (See figure 9.)
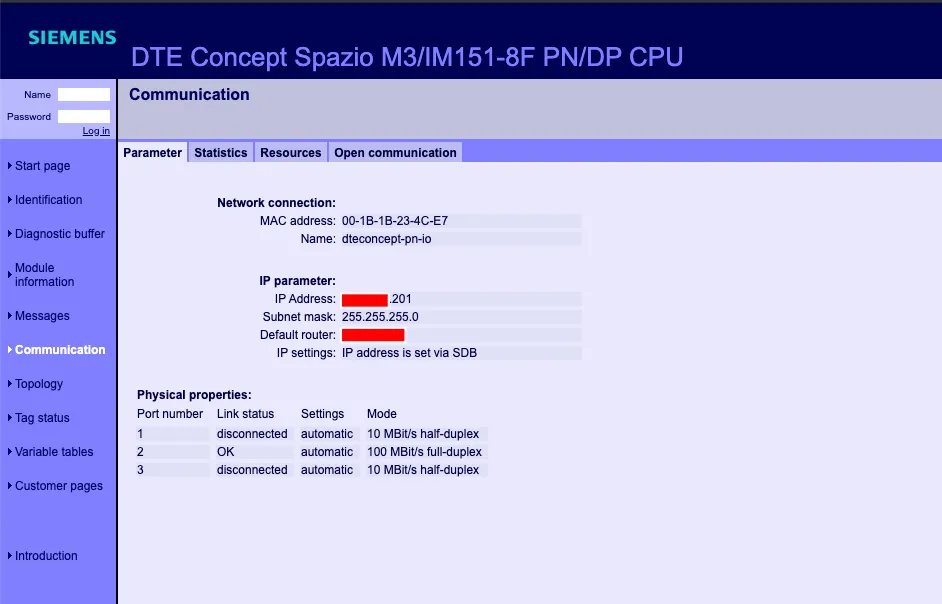
Figure 9
As an attacker, this offers a great deal of data that you can exploit such as you can use the IP address to find out relevant people’s email addresses and password that handles the IT or OT devices. Also, you can brute force the default credential or use a combined approach to gain access to the system using relevant people and default credentials, and once you gain access to the device, you can launch further attacks.
Besides these, you can search for multiple devices and their known vulnerabilities to target them. For example, in figure 10, you can see that Siemens SICAM RTUs device suffers from the vulnerability with the score of 10 and allows an unauthenticated attacker to execute arbitrary code on the vulnerable devices. The patch updates were made available against the vulnerability were released in 2019 with the 2017 CVE.

Figure 10
Hence, any device that did not get updated with the latest patches and running over the vulnerable firmware is on the edge of the risk. You have found all this data as an attacker; thus, you can easily exploit them through free penetration testing tools by complying and exploiting the CVE.
In the blog post, we tried to demonstrate the different OSINT approaches to collect information to make open-source intelligence understandable so you can leverage the OSINT according to your intent and purposes. For example, OSINT plays a huge role in ethical hacking and black-hat hacking and is utilized by security professionals and cybercriminals.
Similarly, OSINT tools have a significant role play in gathering all information with just one tap. It is estimated that by 2026, the global market of open-source intelligence tools will be grown at a compound annual growth rate of 24.7%, which is nearly $29.19 billion. Depending upon the approach, OSINT can also help reduce the attack surface the same way it helps launch the cyber attack.
Contact us today to analyze your business attack surface; we offer multiple cybersecurity assessments to help businesses achieve security thresholds and ensure they are resilient enough to combat cyber incidents. Our services are comprehensive, reliable, fast, and won’t break your bank.