
For years, organizations relied on annual penetration tests to meet compliance frameworks like SOC 2, ISO 27001, and PCI DSS.
But with rapid releases, weekly feature deployments, and increasingly complex cloud environments, one-time assessments no longer reflect real risk.
Today, businesses are shifting toward continuous penetration testing, a hybrid model that blends real human expertise with automation and ongoing validation, ensuring vulnerabilities are caught as soon as they appear, not once a year.
ioSENTRIX helps companies make this transition through its PTaaS-driven continuous security model, offering real-time insights, human-led validation, and rapid retesting.
Annual penetration testing is a fixed-schedule security assessment conducted once a year, usually to satisfy regulatory or contractual requirements.
During this engagement, ethical hackers simulate real-world cyberattacks to uncover vulnerabilities, misconfigurations, and potential paths to compromise.
The test is thorough and valuable for compliance, but it represents a single moment in time.
Once completed, the findings quickly become outdated as new features are deployed, cloud assets change, or new infrastructure components are introduced.
Many organizations shared in community discussions that annual pentests often suffer from predictable weaknesses: a long delay between tests, slow remediation validation, and an inability to keep up with continuous code releases.
Some organizations even expressed frustration that their annual reports were generated primarily from automated scans, lacking manual exploitation or proof-of-concept evidence.
While annual penetration testing remains necessary for regulatory audits and highly sensitive systems, it is no longer enough to defend modern, fast-moving environments.
Continuous Penetration Testing refers to a modern approach where testing happens not once a year, but continually, often triggered by system changes, code deployments, new cloud configurations, or emerging threats.
Instead of waiting 12 months to discover vulnerabilities, organizations gain ongoing, real-time assessment.
This model blends automated scanning for rapid detection with human-led exploitation for depth and accuracy. Vulnerabilities identified by the system are validated by security professionals, and remediation can be retested instantly without needing a new contract or engagement cycle.
In practice, continuous pentesting becomes part of the organization’s development lifecycle. It aligns with CI/CD pipelines, integrates with DevSecOps workflows, and ensures that every meaningful change is examined for potential weaknesses.
ioSENTRIX’s PTaaS platform enhances this model by offering real-time dashboards, continuous monitoring, exploit validation, and no-cost retesting, ensuring every fix is confirmed by a human expert.
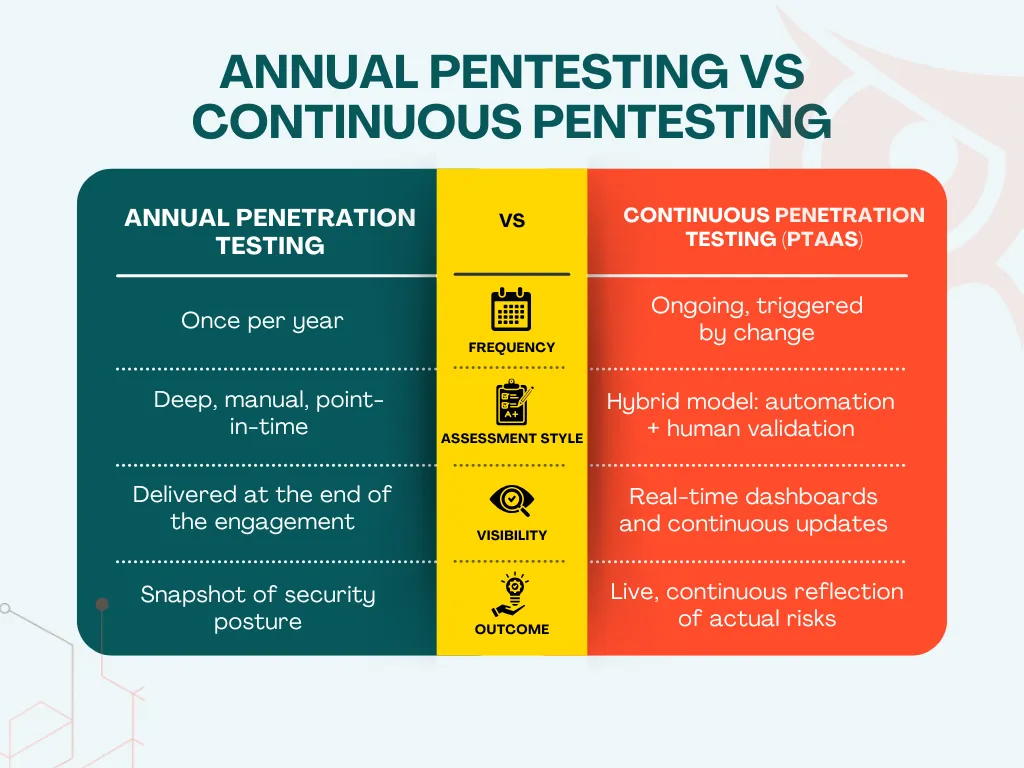
While annual tests give organizations a one-time, in-depth assessment, continuous testing provides an ongoing, always-current view of security risks.
Annual tests are ideal for compliance and deep investigations, while continuous pentesting supports rapid development environments that require agility and visibility.
Continuous testing also allows organizations to remediate vulnerabilities faster, reducing the window of exposure. Additionally, retesting becomes immediate rather than scheduled months later, ensuring issues are fully resolved.
The combination of automation and human insight brings a balance of speed and accuracy that traditional assessments cannot deliver throughout the year.
Many security leaders report that "continuous pentesting" is often misused as a marketing label for simple automated vulnerability scans.
These automated-only models fail to provide exploitation context or business impact analysis, leaving organizations vulnerable despite frequent scanning.
ioSENTRIX addresses these problems by ensuring that every engagement includes both certified human testers and advanced automation.
Instead of deploying only scanners, ioSENTRIX validates each vulnerability with proof-of-concept exploitation where applicable, prioritizes issues based on business impact, and provides clear remediation guidance.
The platform also integrates directly with CI/CD pipelines, allowing each significant change to trigger security testing automatically.
Another common concern is the “lack of contract clarity” noted by cybersecurity professionals. ioSENTRIX solves this by establishing clear Rules of Engagement (RoE), transparent methodology documentation, and full visibility into tools and techniques used.
This ensures that customers receive genuine penetration testing, not repackaged scanning services.
The choice between annual pentesting and continuous pentesting depends on your organization’s operational model and security maturity.
If you operate in a stable environment with infrequent releases, annual penetration testing provides the depth and evidence required for regulatory frameworks.
These assessments are especially valuable for financial institutions, healthcare organizations, and enterprises undergoing strict audits.
However, if your organization releases new features regularly, transitions workloads in the cloud, or manages rapidly evolving infrastructure, continuous penetration testing becomes essential.
This model ensures that new attack surfaces are tested as soon as they are introduced, reducing the risk of prolonged exposure.
In many cases, adopting both approaches yields the strongest defense: annual pentests for deep, compliance-focused analysis, supported by continuous testing throughout the year to maintain real-time security assurance.
Startups benefit from continuous pentesting because their development cycles are fast, and frequent new releases create constant risk. With real-time visibility and rapid validations, they prevent vulnerabilities from accumulating.
SMBs preparing for SOC 2 or ISO 27001 audits find a combination model effective. Continuous testing provides daily assurance, while annual tests provide required audit evidence.
Enterprises with complex infrastructures require continuous pentesting to stay ahead of attackers, especially when managing large cloud deployments and microservices.
Industries such as healthcare, FinTech, and insurance typically need both deep annual assessments and continuous monitoring due to regulatory and data sensitivity requirements.
Cloud-native companies experience the greatest benefit from continuous pentesting because their environment is constantly changing.
For them, annual assessments alone would leave too many blind spots.
Annual penetration testing still holds strong value for compliance and deep analysis, but modern digital environments evolve too quickly for static, once-a-year assessments.
Organizations are now moving toward continuous penetration testing, driven by the need for immediate risk visibility, rapid remediation, and real-time validation.
ioSENTRIX empowers businesses with a complete PTaaS ecosystem that merges human expertise and intelligent automation.
This approach ensures that security assessments stay current, vulnerabilities are validated quickly, and organizations remain compliant and protected, every day of the year.
Continuous penetration testing is an ongoing assessment process where security testing is conducted throughout the year. It combines automated scanning for frequent detection with human-led validation to confirm exploitability and business impact.
Continuous pentesting offers real-time security insights and aligns with rapid development environments. Annual pentests remain essential for compliance and deep analysis, but continuous testing ensures vulnerabilities are caught immediately rather than annually.
No. AI assists in reconnaissance, scanning, and code analysis, but it lacks the creativity and unconventional thinking needed to exploit vulnerabilities in complex, real-world environments. Human expertise remains irreplaceable.
Common tools include Nmap, Burp Suite, Metasploit, ZAP, custom exploit frameworks, and PTaaS dashboards like ioSENTRIX, which blend automation with human insights.
The lifecycle includes planning, reconnaissance, scanning, exploitation, post-exploitation, reporting, and retesting, ensuring vulnerabilities are not only discovered but also validated and remediated.