
As a cybersecurity analyst, the protection of your organization against cyber threats and malicious activities cannot be compromised. You also understand that penetration testing is one of the most important methods for evaluating your security posture and preventing future attacks or breaches. The testing comes in two major categories; automated penetration testing and manual penetration testing.
But, what suits your needs the best? Well, this blog post delves into the pros and cons of both these categories, to help you decide which option makes more sense for your business.
Penetration testing, also known as pentesting, is an essential cybersecurity risk assessment technique that employs ethical hacking methods to identify and exploit vulnerabilities within an organization’s IT infrastructure.
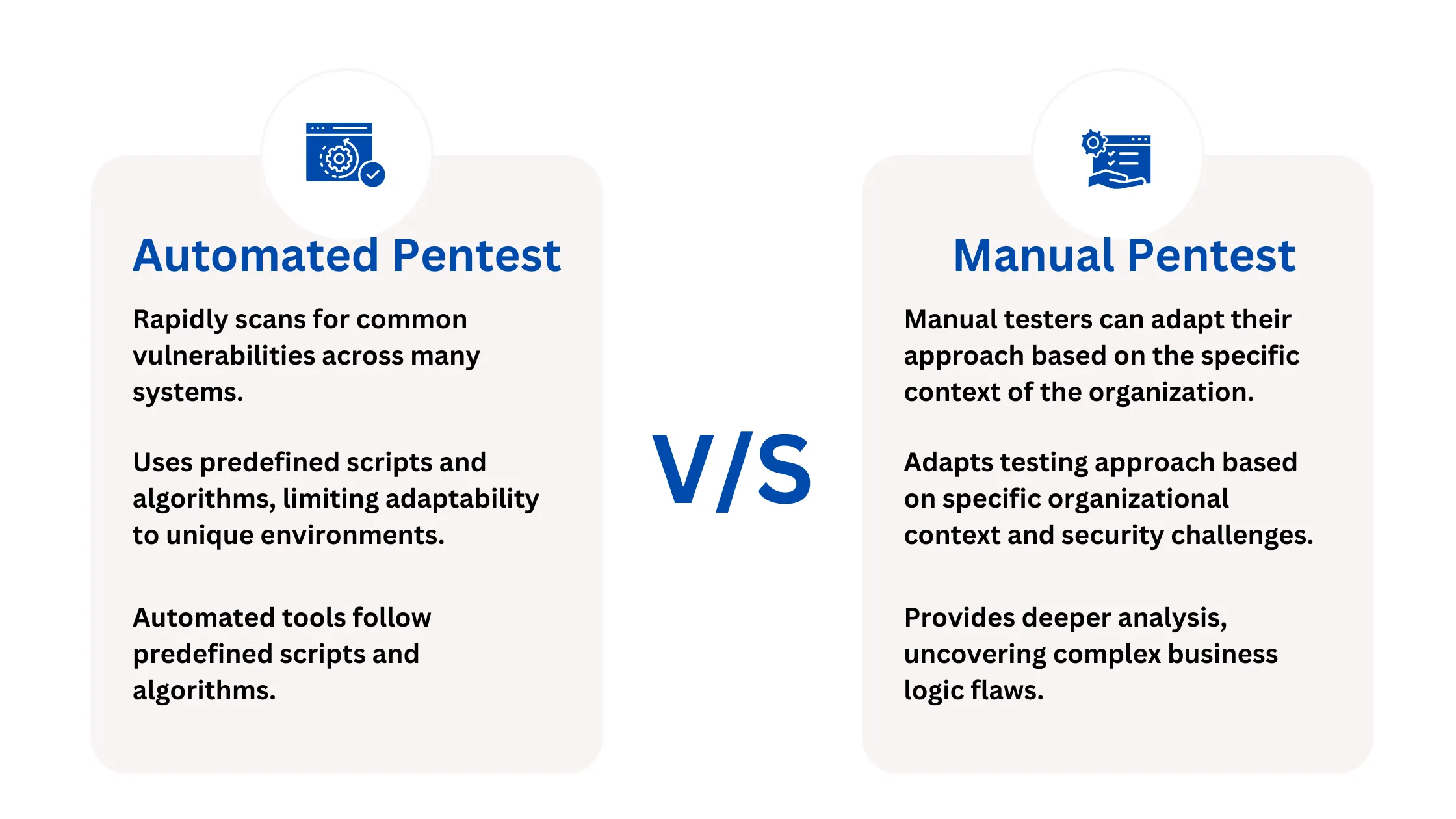
While this may sound alarming, it’s a growing strategy employed by some of the world’s largest companies to stay ahead of malicious actors. By intentionally attacking their own networks, organizations identify vulnerabilities before potential breaches occur. Penetration testing is broadly categorized into two types: automated and manual penetration testing. Both these categories are often used together in a hybrid approach to maximize the breadth and depth of security assessments.
Automated penetration testing involves using specialized tools to rapidly scan and identify common security issues such as open ports, misconfigurations, and known vulnerabilities. While automated tests can efficiently cover a wide area in a short time, they typically function as initial security evaluations rather than exhaustive penetration tests. This is because of incapability to perform complex exploitation and deep analysis necessary to mimic advanced persistent threats in a real-world scenario.
Any organization that launches applications on cloud marketplaces or establishes partnerships with cloud providers, as well as SaaS vendors, cannot rely solely on automated vulnerability scans for adequate security. Cloud platforms and discerning clients demand higher security standards, which can only be met through manual penetration testing.
In contrast, manual penetration testing provides a comprehensive evaluation of an organization’s defenses by actively exploiting vulnerabilities to understand the impact of potential breaches. Manual testers employ a variety of techniques to explore and exploit business logic flaws and other complex security issues that automated tools cannot detect. This method not only identifies deep-seated vulnerabilities but also provides actionable insights and remediation strategies through detailed reports. Manual testing ensures that applications adhere to strict security criteria and are better protected to tackle advanced cyber threats.
Automated penetration testing, though efficient and cost-effective for initial security assessments, has several limitations that organizations must consider, especially when dealing with complex web applications and infrastructures.
Automated tools primarily scan for common vulnerabilities such as misconfigurations, outdated software, or open ports, which are only the surface of potential security risks. These tools cannot perform deep, contextual analysis which is necessary for the detection of complicated cyber threats, particularly those involving intricate business logic.
The primary drawback of automated testing is its inability to understand the business context or assess how different vulnerabilities may interact with one another in a real-world scenario. For instance, automated tools might identify individual vulnerabilities but cannot predict how multiple medium-severity issues could synergize to form a critical security risk. This can lead to underestimating the potential impact of compound vulnerabilities on the organization’s operations.
Moreover, while automated penetration tests can quickly cover a wide array of checkpoints, they often generate numerous false positives that require manual review to verify. This requires additional resource expenditure, which diminishes the initial cost benefits of automation.
Automated tools do not provide actionable remediation guidance to cope with the specific business needs of an organization, making it challenging to prioritize and address vulnerabilities effectively based on their actual business impact.
Consequently, while automated penetration testing can serve as a useful tool for routine security checks and compliance adherence, it should not be relied upon as the sole method for comprehensive security assessments.Organizations should complement automated testing with manual penetration testing. This method provides a thorough evaluation of their security measures and defends against advanced and critical threats.
The hidden costs associated with relying solely on automated penetration testing can significantly affect an organization’s long-term security and financial health. While the upfront costs are lower, the potential for missed vulnerabilities, wasted resources on false positives, and inadequate remediation can result in much higher expenses down the line. This makes a compelling case for integrating manual penetration testing to ensure a thorough and effective security strategy.
Manual penetration testing, or ethical hacking, represents a combination of cybersecurity assessments, especially when examining the intricacies of business logic flaws within web applications. Unlike automated tools that perform surface-level scans, manual pentesters deeply analyze the application’s business context to thoroughly understand its operational mechanics. This comprehensive understanding enables testers to identify and exploit business logic flaws—complex vulnerabilities that automated tools typically overlook.
In the context of a web application, a manual pentester’s role is critical. They not only probe general security weaknesses but also specialize in examining the business logic that governs the application’s functionality.
For example, in an e-commerce platform, a pentester would test scenarios such as the manipulation of cart values to verify if discounts can be unfairly maximized or if transaction sequences can be disrupted. This level of detailed inspection is pivotal for identifying security loopholes that could lead to substantial business losses.
Manual testing integrates technical knowledge with an in-depth understanding of business operations. By adding automated tools to this detailed analysis, penetration testers can achieve wider and faster coverage.This integrated approach effectively aligns technical risks with their corresponding business risks. This alignment is essential for organizations, as it aids in prioritizing remediation efforts based on the potential impact on business operations to refine risk management strategies.
The return on investment (ROI) from manual penetration testing is significant, particularly due to its focus on business risk and providing actionable remediation guidance. Organizations benefit from insights that are not only technically sound but also aligned with their business objectives and safeguard their critical assets effectively.
Another distinct advantage of manual pentesting is the ethical hacker’s ability to synthesize multiple vulnerabilities to evaluate their combined impact. For instance, while automated tools might identify individual medium-severity issues separately, a manual pentester can determine if a combination of these issues could escalate to a critical threat. This capability to aggregate and elevate the severity of interconnected vulnerabilities is something automated tools lack.
Thus, manual pentesting brings unique value to cybersecurity defenses. In summary, manual penetration testing is indispensable for organizations that require an effective and deep understanding of their cybersecurity posture. It is the best approach to protect web applications or infrastructures from sophisticated threats, ensuring both technical and business aspects of risks are comprehensively managed.
Manual penetration testing identifies complex vulnerabilities and business logic flaws that automated tools often miss. This approach prevents severe security breaches by addressing deep-seated issues, providing a strong shield against potential threats. By proactively resolving these vulnerabilities, organizations can save on future costs related to breaches and extensive damage control.
Manual penetration testing aligns technical vulnerabilities with business risks, offering clear prioritization for remediation efforts. This targeted approach ensures resources are directed to the most critical areas, thereby enhancing the organization’s security posture. By focusing on these priorities, the likelihood of major security incidents is significantly reduced, providing strong protection against financial and reputational harm.
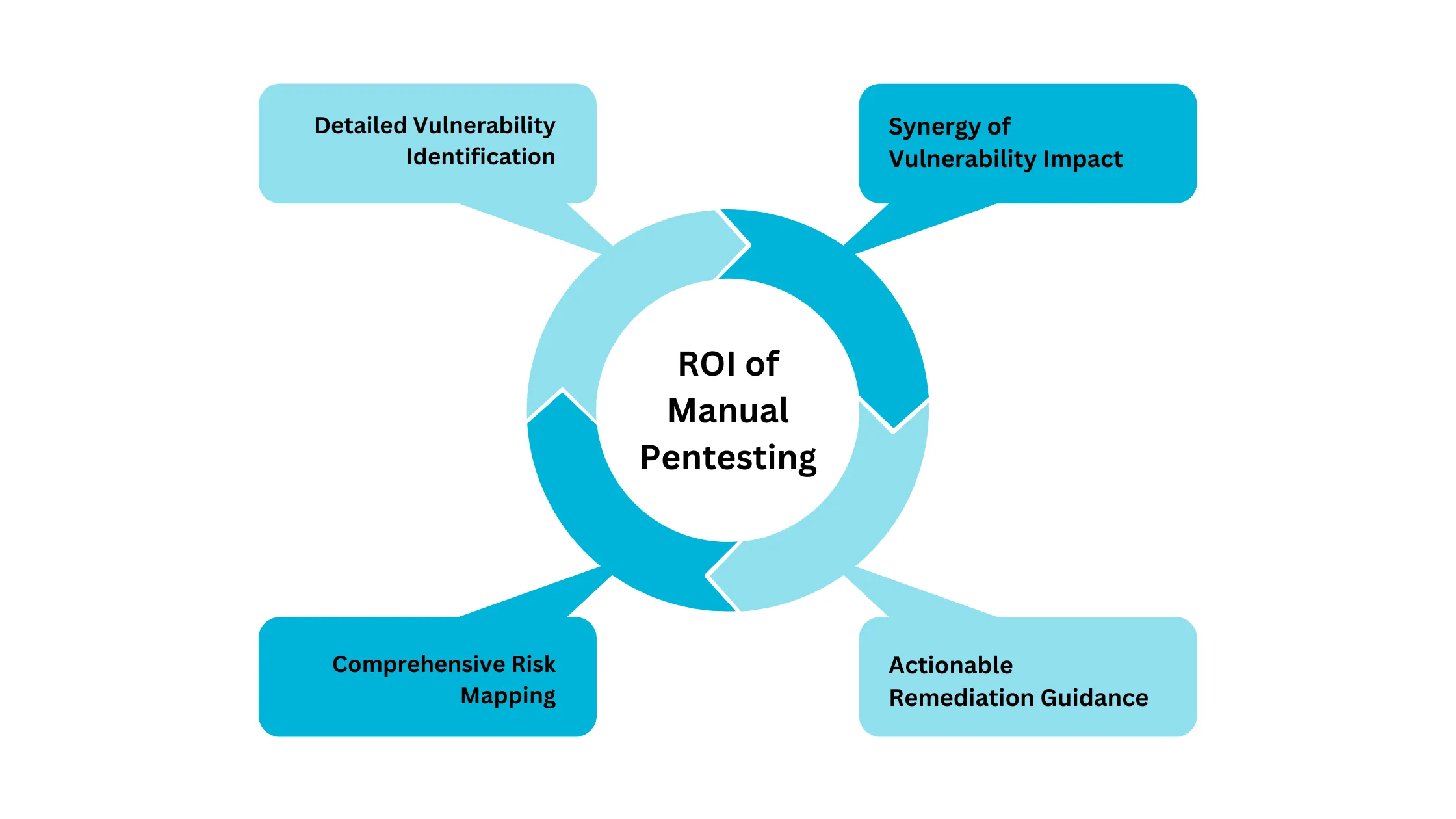
Manual penetration testing offers actionable steps for mitigating identified risks customized to the specific context of the business. In this way, it increases the effectiveness of security measures and provides long-term benefits and stability for the organization.
Manual penetration testing also evaluates how multiple lower-severity vulnerabilities might combine to pose a high-severity threat. This approach prevents attacks that exploit multiple weak points simultaneously, thus, the organization’s understanding and response to complex attack vectors is enhanced.
While both automated and manual penetration testing have their roles in a comprehensive cyber security strategy, the true value of manual penetration testing cannot be underestimated. The detailed insight, tailored mitigation strategies, and deep understanding of business logic provided by manual tests offer an unparalleled advantage in securing an organization’s assets.
Organizations should consider the long-term benefits of investing in manual penetration testing. The initial higher cost and time investment are far outweighed by the prevention of significant financial losses, legal ramifications, and reputational damage that can result from a security breach. Do you want to boost your cybersecurity?
ioSENTRIX offers customized and cost-effective penetration testing services. With ioSENTRIX, businesses are served with a team of skilled, certified professionals proficient in both automated and manual testing techniques. This ensures a thorough and proactive approach to managing risks. By integrating these services, ioSENTRIX not only identifies and addresses immediate vulnerabilities, but also strengthens your organization’s ability to withstand future cybersecurity challenges.
Choosing ioSENTRIX is not just an enhanced security; it’s a strategic investment in the future stability and security of your business. Partner with ioSENTRIX to safeguard your business against evolving cyber threats wisely.