
Cyber Threat Intelligence (CTI) is the process of collecting, analyzing, and sharing information about potential cyber threats to enhance security measures. The key benefit of Cyber Threat Intelligence is its ability to provide organizations with real-time and relevant data, so they can map out informed decisions about their security infrastructure. This strategy not only empowers cybersecurity defenses but also promotes a culture of continuous improvement and adaptation against cyber threats.
CTI is an important part of modern cybersecurity practices. It provides organizations with advanced and valuable insights ahead of falling a victim to cyber activity and improves their defense mechanisms. The understanding of the tactics, techniques, and procedures of CTI help organizations strengthen their security posture and minimize the impact of cyberattacks.
In this ultimate guide, we will delve deep into the world of CTI and explore its different facets, as well as its crucial role in safeguarding organizations against cyber threats.
Cyber Threat Intelligence is not just limited to large corporations or government entities. In fact, organizations of all sizes and across various industries can benefit from CTI. Financial institutions, healthcare providers, e-commerce platforms, critical infrastructure sectors, every entity that relies on networked systems and stores sensitive data can benefit from CTI as part of their security framework.
Using CTI, organizations can gain a comprehensive understanding of the threat landscape relevant to their industry and specific vulnerabilities they might face. This awareness allows them to create proactive defense measures, prioritize security investments, and allocate resources efficiently.
CTI enables organizations to detect and respond to security incidents swiftly, thereby reducing the dwell time of threats within their networks and minimizing potential damages.
Strategic intelligence focuses on providing a long-term view of potential threats. It involves gathering information about threat actors, their motivations, capabilities, and objectives. By analyzing this data, organizations can anticipate the type of threats they might face in the future and develop proactive strategies to mitigate the risks.
Strategic intelligence is also essential for understanding the broader cyber landscape, including emerging trends, geopolitical factors, and regulatory changes. This understanding allows organizations to align their security strategies with the advanced and complex threats and stay ahead of potential adversaries.
For example, Let’s consider a hypothetical scenario where a large financial institution is analyzing strategic intelligence. They discover that a new group of threat actors has emerged, targeting financial institutions with ransomware attacks. Using this knowledge, the organization can enhance their security measures, such as implementing multi-factor authentication and conducting regular security awareness training for employees.
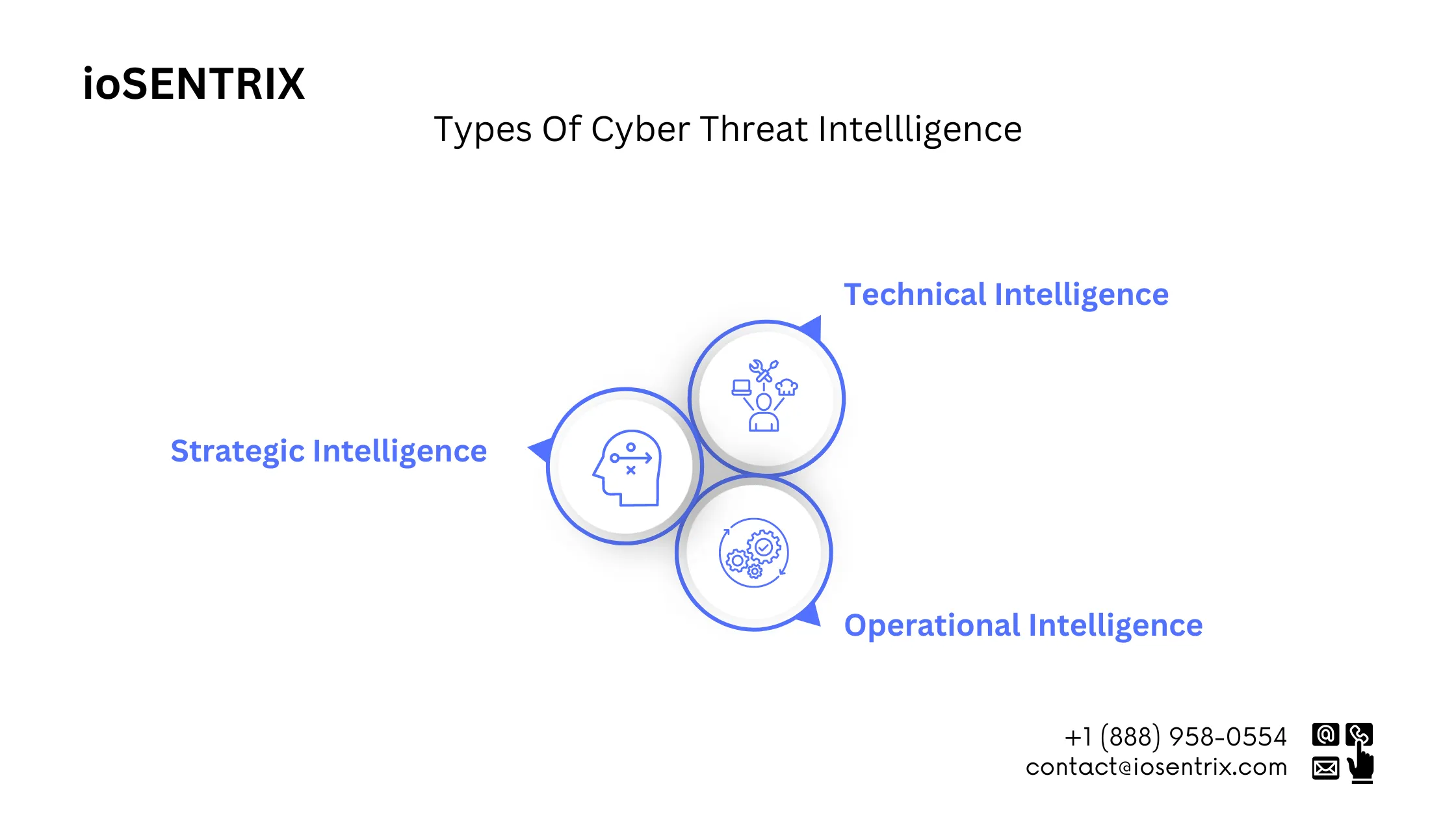
Tactical intelligence focuses on real-time monitoring and analysis of potential threats. It provides organizations with up-to-date information about ongoing attacks, vulnerabilities in their systems, and indicators of compromise. This timely intelligence enables organizations to quickly respond to threats, contain incidents, and prevent further damage.
Tactical intelligence includes monitoring various sources such as threat feeds, open-source intelligence (OSINT), and dark web forums. Continuous monitoring of these channels allows organizations to identify new attack vectors, malware campaigns, or targeted campaigns. They can then take immediate action to protect their systems and networks.
Example: Imagine a healthcare organization that relies heavily on tactical intelligence. They receive a real-time alert about a new strain of malware specifically designed to exploit vulnerabilities in medical devices. With this information, the organization can swiftly patch the affected devices, update their security protocols, and notify relevant stakeholders to prevent potential patient harm.
Operational intelligence focuses on optimizing security measures and incident response capabilities. It involves analyzing historical data, patterns, and trends to identify areas for improvement. Operational intelligence also helps organizations identify gaps in their defenses and prioritize the allocation of resources.
Example: Let’s consider a technology company that heavily relies on operational intelligence. Through analyzing historical data, they discover a recurring pattern of successful phishing attacks targeting their employees. The organization can then enhance their employee training programs, implement advanced email filtering systems, and conduct regular phishing simulations to educate and empower their workforce against such threats.
Threat intelligence is essential for various practices, including vulnerability management, risk management, incident response, and overall security operations (SecOps). Cyber Threat Intelligence (CTI) is crucial for organizations because it:
Offers comprehensive information about attackers’ tactics, techniques, and procedures (TTPs) used in cyberattacks.
Reveals attackers’ hidden motives, allowing businesses to implement preventive measures to avoid financial losses and reputational damage from data breaches. Detects long-term threats that exploit security vulnerabilities, helping to protect intellectual property and sensitive data.
Helps cybersecurity professionals, such as CISOs, SecOps teams, and developers, understand how threat actors operate and make decisions. Guides stakeholders in investing in the right tools and processes to mitigate cybersecurity risks, reducing unnecessary costs.
Empowers organizations to make well-informed, timely, and data-driven decisions about cybersecurity.
This includes identifying the information needed, the sources to monitor, and the technologies required to collect and analyze the data. By clearly defining their CTI requirements, organizations can ensure that the information they gather aligns with their specific needs. Defining requirements for effective CTI involves a comprehensive understanding of the organization’s assets, vulnerabilities, and potential threats. It requires a deep dive into the industry landscape, regulatory requirements, and the organization’s risk appetite.
Once the requirements are defined, organizations can begin the process of gathering and sorting raw data. This involves collecting data from various sources such as threat feeds, malware analysis reports, incident reports, and vulnerability databases. It is essential to have a structured approach to gather and store the data, ensuring that it remains easily accessible for analysis.
Gathering raw data requires organizations to establish strong relationships with trusted sources and partners. This includes collaborating with cybersecurity vendors, threat intelligence providers, and industry peers.
The raw data needs to be processed to extract actionable insights. This involves validating the authenticity of the data, filtering out noise, and improving it with additional context. Advanced techniques such as natural language processing or machine learning processing can be utilized to automate data analysis and processing. These technologies can help organizations uncover hidden patterns, identify emerging threats, and prioritize their response efforts.
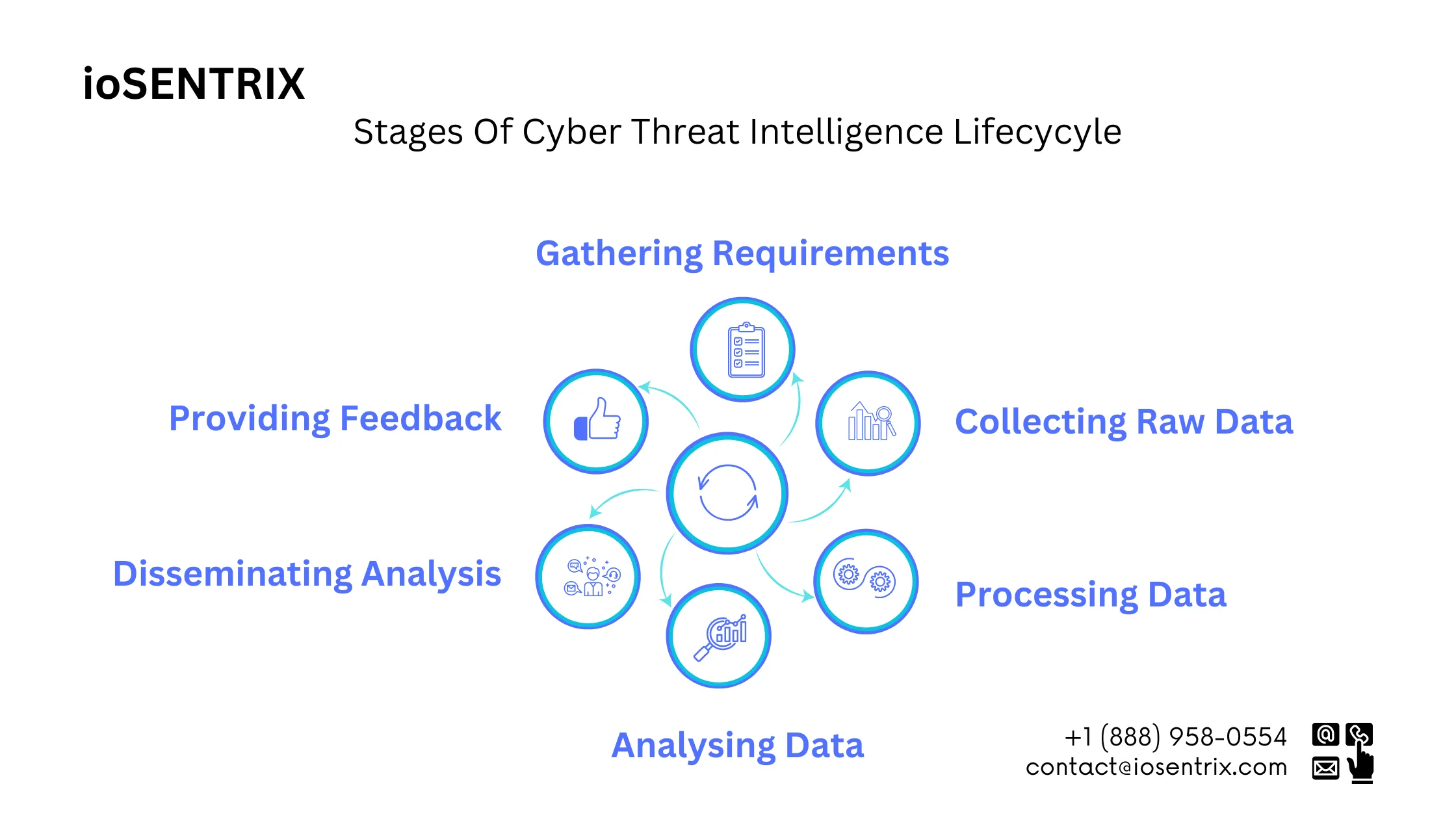
The analysis phase is where the true value of CTI comes to light. By analyzing the processed data, organizations can identify patterns, trends, and potential threats. This involves correlating different data points, identifying indicators of compromise, and mapping them to known threat actors or campaigns.
During the analysis phase, it is crucial to share findings and collaborate with internal teams, industry peers, and trusted security partners. This collective effort validates the findings, provides additional context, and enhances the overall effectiveness of CTI.
One of the core principles of CTI is the sharing of information. By sharing the analyzed intelligence with relevant stakeholders, organizations contribute to the collective security of the entire ecosystem. This includes sharing information with industry-specific Information Sharing and Analysis Centers (ISACs), government agencies, and trusted partners.
The shared intelligence enables organizations to benefit from broader threat visibility and utilize the collective knowledge and expertise of the community. It also helps identify global threat trends and enables early warning capabilities.
CTI is an iterative process that requires continuous improvement. Feedback from stakeholders, organizations can refine CTI processes, enhance their intelligence analysis capabilities, and maximize the effectiveness of their security measures.
Organizations should promote a culture of feedback and collaboration and encourage open discussions and knowledge sharing. This includes regularly reviewing and updating their CTI requirements, data collection methods, and analysis techniques to ensure they remain effective in the face of emerging threats.
Cyber Threat Intelligence is a powerful weapon against the increasing cyber threats. Embracing CTI as part of their security strategy helps organizations gain valuable insights, enhance their defenses, and proactively protect their assets, networks, and data.
However, it is crucial to remember that CTI is not a standalone solution. It should be integrated with security practices, technologies, and incident response capabilities.