
In December 2022, OU Health, a hospital in Oklahoma, notified approximately 3,000 patients about a data breach resulting from the theft of an employee’s laptop. The breach exposed sensitive information such as treatments, social security numbers, and insurance details of the patients. This incident highlights the significance of comprehensive security measures to protect sensitive data.
Let’s explore the concept of security controls. We’ll discuss the different types and categories of security controls, along with examples. Additionally, we’ll go through the steps to implement these controls.
“Security controls are measures implemented to protect an organization’s critical data and infrastructure. They aim to identify, combat,, and manage risks to physical assets, information, IT systems, and other resources.”
A study conducted at the University of Maryland’s Clark School revealed that cybersecurity attacks happen every 39 seconds in the U.S., impacting one in three Americans annually. Small businesses are particularly vulnerable, as 43% of these attacks target them. From March 2021 to March 2022, the typical expense of a data breach in the United States amounted to $9.44 million.
Companies need to strengthen their data protection strategies to avoid possible penalties. The European Union enforced the General Data Protection Regulation (GDPR) guidelines in 2018 with strict standards. Similarly, California’s Consumer Privacy Act became active on January 1, 2020, and numerous other states are considering similar regulations.
Most regulations have strict penalties for companies that fail to meet the criteria. For instance, Meta has estimated a fine of over USD 3 billion from the U.S. Federal Trade Commission for issues related to data protection policies resulting in data breaches.
Different security measures can safeguard hardware, software, networks, and data from potential threats that may result in harm or loss. For example:
Physical security measures consist of various elements like fencing around the data center, locks, security guards, access control cards, biometric systems, surveillance cameras, and intrusion detection sensors.
Digital security refers to the tools utilized to safeguard your online identity, data, and assets. These resources involve web services, antivirus software, smartphone SIM cards, biometrics, and secure personal devices.
Cybercriminals are drawn to the wealth of valuable data available, viewing it as an opportunity for exploitation. Even if they manage to trick just one person, such as using a phishing scam, hackers can benefit greatly from stolen information like identities or credit cards with significant funds.

The controls are designed to uphold the CIA triad, which stands for ensuring the confidentiality, integrity, and availability of an organization’s information and technological assets. Controls are structured around four key elements: people, technology, processes, and strategy. Cybersecurity controls serve as a mechanism to prevent, detect, and combat cyber-attacks and threats such as Distributed Denial of Service (DDoS) protection and systems that prevent unauthorized intrusions.
Cloud security controls are tools and processes created to safeguard data, programs, and systems within cloud platforms. These controls establish rules and guidelines for managing the security of cloud-based technologies. They can take the form of physical, technological, or administrative measures, spanning various actions such as encryption, user authentication, and response plans for security incidents.
Security control systems consist of processes and documentation that outline the implementation and management of these controls. They are commonly known as frameworks or standards. Frameworks help organizations to effectively oversee security measures for various assets based on established and proven methods. Popular frameworks and standards include:
In 2014, NIST introduced a voluntary framework to help organizations detect, respond to, and prevent cyberattacks. It helps organizations protect themselves against cyberattacks by offering guidance on prevention, detection, and response.
The framework involves assessing an organization’s security controls to ensure they are correctly implemented and functioning as intended. This verification guarantees that the controls are effective in meeting the organization’s security needs. The NIST framework is regularly updated to stay current with cybersecurity improvements.
The CIS created a list of top-priority defense measures that all businesses should prioritize to protect against cyber threats. These measures, known as the CIS controls, are based on common attack patterns identified in major threat reports and have been tested and approved by a wide range of government and industry experts, according to the SANS Institute.
Businesses can utilize these frameworks and others as a guide to create their security framework and IT security policies. An effective framework ensures that an organization:
The effectiveness of a security solution depends on its weakest point. For further security, it is important to have multiple layers of security controls, known as a defense-in-depth strategy. This strategy involves implementing security measures for identity and access management, data protection, applications, network and server infrastructure, physical security, and security intelligence.
Conducting a security controls assessment is a crucial initial measure to identify any existing vulnerabilities. This assessment allows you to assess your current security controls to ensure they are correctly implemented, functioning as expected, and align with your security needs.
The NIST 800-53 Standard, developed by the National Institute of Standards and Technology, is a valuable resource for assessing security controls. Following the NIST guidelines as a standard practice can reduce the chances of security breaches in your organization. If preferred, your organization can develop its security assessment process.
Important steps to consider when conducting a security assessment are:
Determining the Target Systems: Compile a list of IP addresses for scanning within your network. Include the IP addresses of all systems and devices connected to your organization’s network.

Determining the Target Applications: Provide a list of web applications and services for scanning. Additionally, identify the web application server, web server, database, third-party components, and technologies utilized in constructing current applications.
Conducting Vulnerability Scanning and Reporting: To prevent any potential issues during a vulnerability assessment, it is important to keep both network and IT teams updated on all assessment activity. This is necessary as the assessment can sometimes lead to increased network traffic, causing potential disruptions.
Additionally, it is crucial to obtain proper permissions for scanner IPs to pass through the organization’s network without authentication. To avoid triggering any security alerts, ensure that these IPs are added to the whitelist in the IPS/IDS system. Failure to do so may result in the scanner’s IP address being blocked due to suspicious activity.
Perform a risk assessment to identify any weaknesses in your infrastructure and understand the necessary security measures. Determine which controls can address the identified weaknesses and mitigate potential risks. Delegate control responsibilities to specific individuals within each department.
Strict preventive measures are essential to minimize the risk of intrusions and cyber threats. It is advisable to employ monitoring tools to prevent potential breaches.
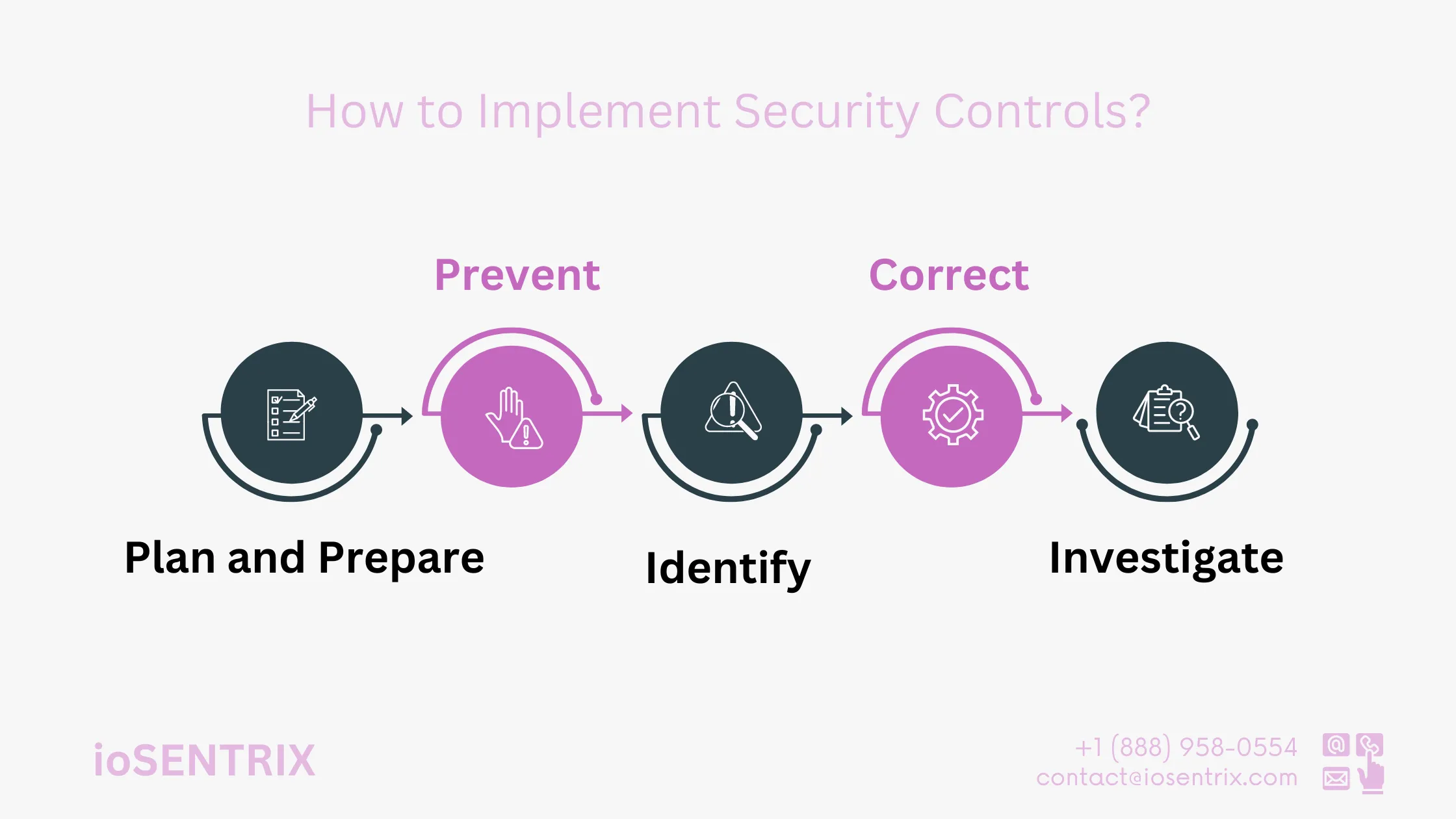
This stage is crucial for detective controls to identify and analyze any breach attempts or system weaknesses to prevent malicious attacks. Utilize your detective systems to spot any breach attempts or weaknesses and stop potential malicious attacks.
Intruders sometimes manage to infiltrate systems, but it’s a common occurrence. That’s why there are measures in place to address such incidents. It’s important to identify and fix any issues, document the corrections, test important systems impacted by the breach, isolate the compromised systems, and apply patches to prevent future attacks.
After successfully neutralizing the threat, it is important to investigate the breach. Determine how the breach happened and whether appropriate security measures were in place. If security measures were in place, how were they bypassed? Assess the damage caused by the breach. Lastly, outline steps to prevent such incidents from happening again.
Are you feeling overwhelmed by managing and tracking numerous controls? We understand that handling various tools, systems, people, and processes can be challenging.
ioSENTRIX offers a unified platform that streamlines the management of security tasks, providing role-based access control, anomaly detection, and advanced threat mitigation solutions.