
Often, it gets hard to understand the differences between some of the security assessments as most of the security activities complement each other at many points. With the growing and complex attack tactics, all businesses are adapting security practices and services to protect themselves against threats.
But on the contrary, it is getting tough to pick a distinct critical feature in all security assessments to pull off the right security services according to the risk and business’ necessities.
When it comes to defeating intruders and augmenting the defensive approaches, Vulnerability Assessment (VA) and Penetration Testing (PT) are the most fundamental and useful assessments to pick. But, both are one of those security assessments that confuses a majority.
To choose the appropriate security test, it is crucial to understand the diversity, qualities, and necessity of both. VA and PT can be infrastructure, or web-app focused, or can include both. They both help identify potential vulnerabilities and put the right security measures.
They also further amplify the defense by allowing the organizations to prioritize the critical assets according to the risk.
In this blog, we have shed light on the most essential and critical points that will make it easy to understand each of them.
So let’s get to basic to learn Vulnerability Assessment Vs Penetration Testing
Vulnerabilities assessment revolves around hunting maximum vulnerabilities. Vulnerabilities could be identified through reviewing codes, configuration, architecture, etc. The security bugs could be present in any level of network, application, or system, although in the cybersecurity industry, it is served with the limited scope of automated scan in infrastructure and web-application.
In VA, security professionals look for security flaws or weaknesses and classify them based on their risk (i.e., likelihood*impact or CVSS 2/3 score).
In penetration testing, the classified vulnerabilities are often alone or sometimes chained up to exploit in order to gain access to the applications, networks, devices, or infrastructure to simulate malicious activities.
The primary purpose of pentesting is to identify how an organization can be hacked or breached and how likely it can impact the business continuity and reputation. Whatever the goal of penetration testing an organization takes, it always enhances defensive controls by evaluating and remediating the exploited vulnerabilities.
There are a handful of objects that make each of them distinct, but we will take a look at the most prominent ones to help you learn the core of each assessment.
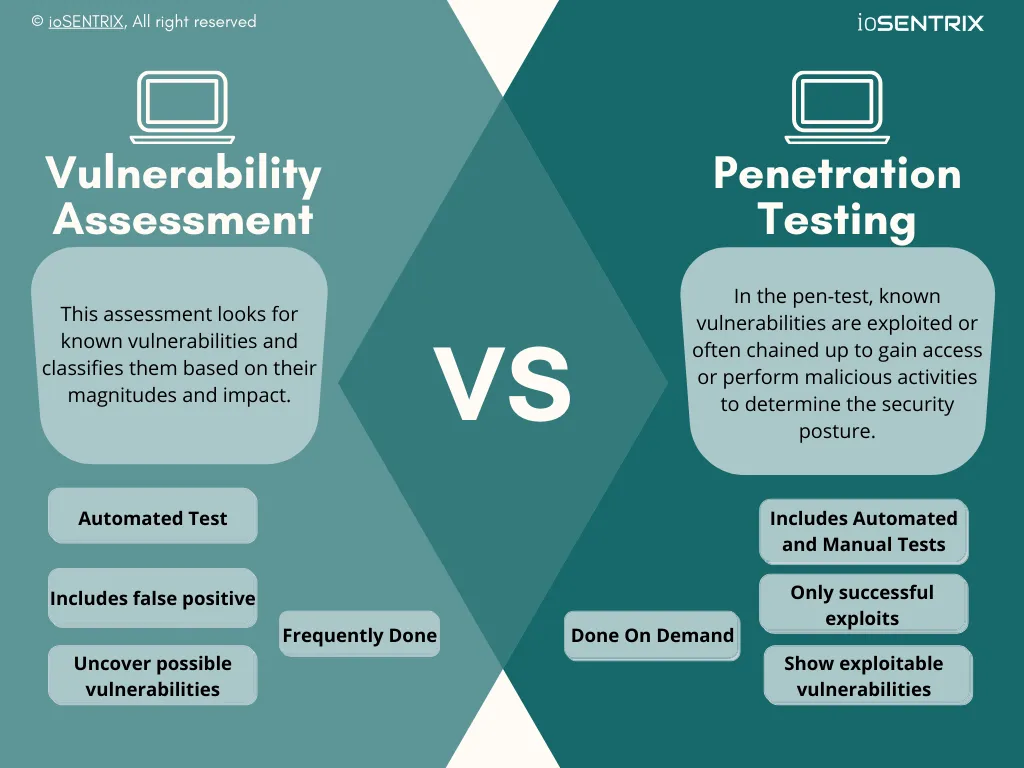
Use this link to download this Vulnerability Assessment vs Penetration Testing infographic in PDF format.
As vulnerabilities constitute risks that any ill-intentioned actor can exploit. Thus, an organization must be aware of every deficit to produce a remedy or find a solution. Also, no matter if you perform VA or PT, each identifies weaknesses and highlights the organization’s current security controls and defense capabilities. VA and PT are indispensable and valuable on their own when it comes to securing your critical assets.
Check out our detailed blog on Penetration Testing to learn more. As a trusted security service provider of Fortune 500 and SMB enterprises, we offer vulnerability assessment and penetration testing as a service to all kinds of businesses. Our VA and PT assessments deliver the best quality reporting of each bug and flaw. We ensure security at every possible end-points. For consultation and testing, email or call us.