
Organizations heavily rely on data for operations but often lack effective measures to secure it during transmission, access, or storage. They often do not take strong enough measures to protect this data. Internal security measures frequently fall short and may not be effective against significant attacks.
Hackers and malicious individuals tend to take advantage of these weaknesses. While organizations enhance their security, they often spread their efforts too thin rather than focusing on critical data protection needs.
Compliance with ISO/IEC 27001:2022 is a valuable initial step toward improving security and compliance. This article explains ISO 27001 compliance, its importance, key components (controls), and how it contributes to overall security.
ISO 27001 Compliance is a global framework that helps organizations manage, monitor, implement, review, and maintain their information security. It helps organizations safeguard the confidentiality, availability, and integrity of their ISMS.
ISO 27001 is part of the more prominent 27000 family of standards that work together to provide the best cybersecurity practices for organizations of all sizes and types. These standards support comprehensive information security management across various types of data.
ISO 27001 is widely recognized as the top standard for information security. While compliance with the ISO 27001 framework is not mandatory, it is essential for several important reasons:
Security breaches can have a cascading effect; when one occurs, it can put many systems and processes at risk. For instance, Toyota had to stop production due to a cyberattack.
Achieving ISO 27001 compliance enables you to identify weaknesses, evaluate current risks, and apply necessary controls to support steady growth. This process requires ongoing risk assessment, which allows your team to tackle issues before they lead to more significant problems.

Control 17. A in Annex A ensures information security continuity. It mandates that organizations develop a plan for their needs, establish and maintain the necessary processes, and regularly check these processes to ensure ongoing security in case of a disaster.
No business owner would ever say, “Data security is unimportant to me, and anyone can access it.”
Data is an essential asset for every organization. More companies are seeking partners who prioritize information security, and you may be overlooked if you can’t demonstrate a commitment to it. ISO 27001 certification gives you a competitive edge over others in your field who cannot prove they have strong security measures in place.
Organizations use various security controls to identify, prevent, lessen, and address threats. However, these controls are often uncoordinated because they are implemented to react to specific problems. It usually leads to a focus on data stored in the cloud, leaving non-IT assets, such as paper documents, vulnerable.
Implementing an Information Security Management System (ISMS) allows you to gain control over all aspects of security, including physical security. An ISMS requires you to adopt a wide range of controls to safeguard data in all forms.
ISO 27001 consists of 114 controls organized into 14 categories. It aims to offer a framework for organizations to manage risks related to information security. You can select the controls that are most relevant to your business. Here is a list of the 14 categories and their objectives:
Information Security Policies (A.5)
Management guidelines and information security support should align with the requirements of ISO 27001 and applicable laws and regulations.
Organization of Information Security and Assignment of Responsibility (A.6)
It creates a management framework to oversee the implementation and operation of information security. It also ensures the protection of remote work and mobile devices.
Human Resource Security (A.7)
It ensures that employees and stakeholders know and meet their security responsibilities. It also requires employees to share their security roles when their job status changes.
Asset Management (A.8)
Focused on asset identification, protection, and prevention against unauthorized access.
Access Control (A.9)
Limit data access and processing facilities so that only authorized individuals can use them. Also, hold users accountable for safeguarding the data.
Encryption and Handling of Sensitive Information (A.10)
Makes sure that cryptography is used effectively to keep data confidential and maintain its integrity. (Annex A.10 cryptography controls are designed to secure information stored or transmitted electronically).
Physical and Environmental Security (A.11)
Stops unauthorized physical access to data and its processing facilities. It also helps prevent loss, theft, asset damage, and disruptions in business operations.
Operations Security (A.12)
Ensure the safe operation of data processing facilities against malware and data loss. Organizations must log events and evidence, protect against technical vulnerabilities, and minimize the impact of audits on systems.
Communication Security (A.13)
Safeguard data on the network and its supporting facilities while ensuring the security of shared information.
System Acquisition, Development, and Maintenance (A.14)
Ensure security is upheld during every stage of the information life cycle.
Supplier Relationships (A.15)
Adhere to service-level agreements for the delivery of information security services.
Information Security Incident Management (A.16)
Make sure to manage information security incidents effectively and consistently.
Information Security Considerations in Business Continuity Management (A.17)
Ensure security is part of the continuity management systems and is available in processing facilities to maintain consistent protection.
Compliance (A.18)
Avoid violations of legal and contractual security obligations. Ensure that security measures and operations are in accordance with the company's policies and procedures.
The ISO 27001 certification process involves a written document showing that your system meets the requirements. This certification comes from external bodies, not ISO itself.
If you want to become ISO 27001 compliant, ensure the certification body follows the appropriate CASCO standard. CASCO, which is the ISO Committee on Conformity Assessment, offers guidelines for the certification process.
Below is a brief overview of the implementation process:
The initial step in the ISO 27001 process is to develop a scoping document that outlines the data you want to protect. This will depend on your business structure, needs, methods, and products.
The ISO 27001 scoping document should clearly identify the types of sensitive information your organization manages, the products and services involved, the supporting processes, as well as the people and technology included in the ISMS.
It should also mention any exclusions, if applicable.
This comprehensive checklist of policies, procedures, and documents is designed to manage and reduce risks to your ISMS. Evaluate the risks that threaten your essential data, taking into account their severity level.
Must Read: 6 Steps to Conduct a HIPAA Risk Assessment.
The Statement of Applicability (SoA) is a document that outlines the controls you will implement as part of the ISO 27001 process. It should detail the chosen controls and provide reasons for including or excluding each one.
The SOA is essential for auditors to assess ISO compliance. It lists the controls your organization applies, explains why they're relevant and provides reasoning for any exclusions. Based on your risk management plan, select those that are relevant to your business from the 114 controls listed in Annex A.
Be sure to include valid explanations for any controls you decide not to implement in the SoA. If necessary, the SoA may incorporate non-ISO 27001 controls due to legal, business, or contractual requirements.
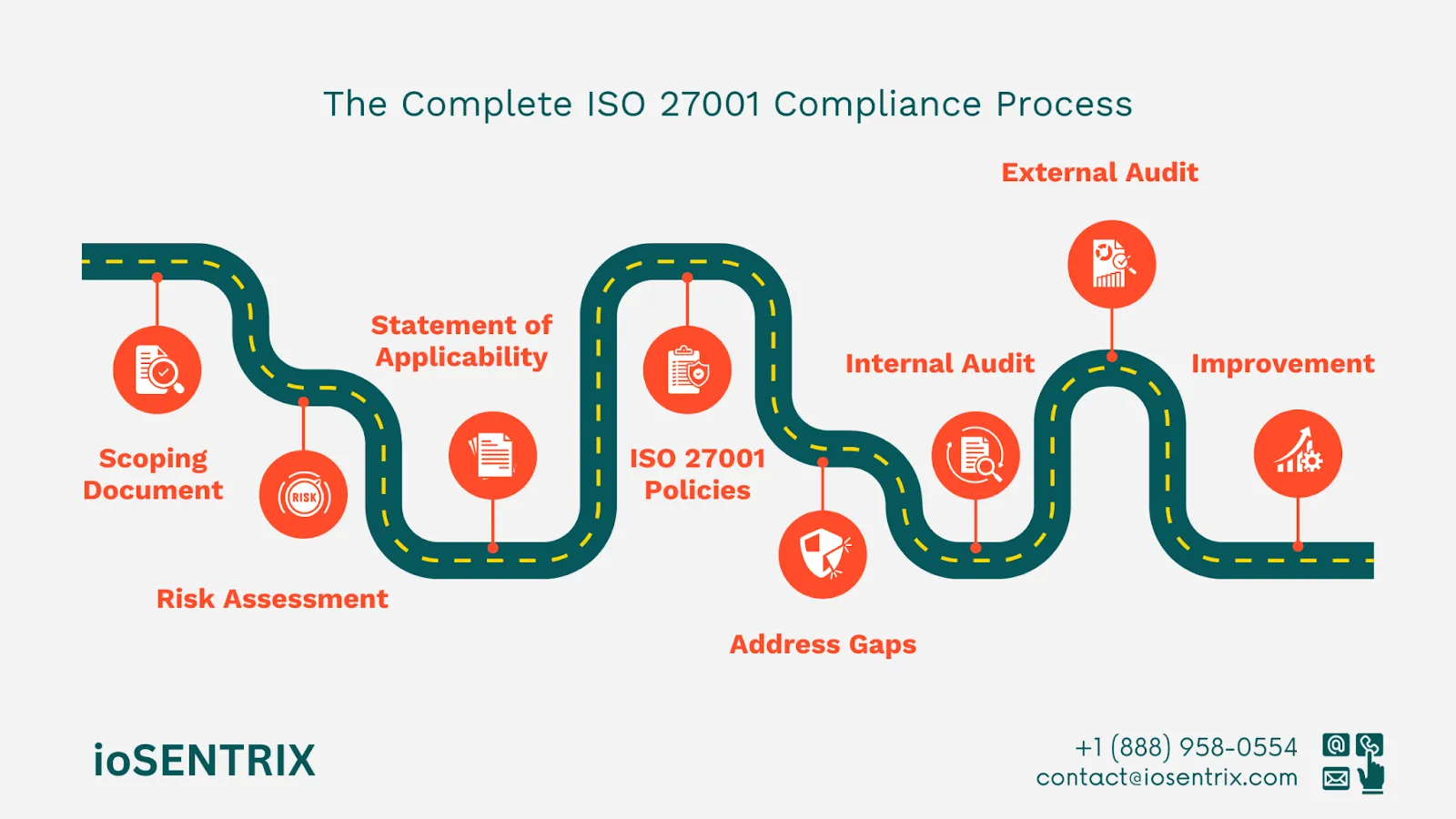
Your ISO 27001 policies should provide clear data protection guidelines, focusing on three key principles: confidentiality, integrity, and availability. These policies should also define the responsibilities and roles of individuals who oversee the ISMS and specify which groups are affected, such as employees, vendors, and contractors.
Begin by performing a gap analysis for ISO 27001. After identifying the gaps, set up a continuous monitoring process to keep track of these areas. Next, examine the root causes and risks linked to each gap, and finally, implement specific controls or improvements to meet the standard.
Manually addressing ISO compliance gaps is time-consuming, often taking up to a year and involving extensive coordination with assessors.
An ISO 27001 internal audit can be carried out by your team or by an outside auditor. The person assigned to this task will review documents, perform penetration tests, prepare the internal audit report, and examine any non-conformities while documenting their findings in detail.
The internal audit report will include an executive summary, an audit plan, methodology, discoveries, recommendations, and a timeline for addressing issues. These components will assist you in:
An external auditor examines your documents and issues an audit report and certification. A stage 2 audit follows this to confirm that your systems function according to the required standards. The auditor will then present a report detailing their findings.
Achieving ISO 27001 compliance is an ongoing process. To address constantly evolving threats, regular risk assessments and analyses and corrective actions as needed are important.
One effective way to maintain continuous compliance is to automate many parts of the process, ensuring you receive alerts whenever a control fails. ioSENTRIX can assist you through its real-time monitoring features and comprehensive control dashboard.
This checklist will guide your organization in effectively implementing an ISMS in accordance with the ISO 27001 standard and assist you in preparing for your audit.
A strong security posture can be challenging, but it's not impossible—especially with the right tools. A successful approach relies on a combination of people and processes to keep your organization safe.
ioSENTRIX Service is designed with ease of use, consistency, and compliance needs in mind. We automate the tasks on your compliance checklist, monitor for new and existing threats, and create an audit trail, making the certification process quicker and simpler.
With ioSENTRIX, you will have integrated risk assessments and continuous support from our experts whenever needed.
Interested in how we can help your business? Contact us today for a straightforward compliance experience.