
After a vulnerability assessment, penetration testing is the next step. Penetration testing attempts to exploit a system in a controlled way to discover possible weaknesses. Authorized testers are allowed to try to exploit the system to find vulnerabilities. This process simulates an attack to evaluate the security of the information system.
It also evaluates how well security training works by using social engineering tactics. This is a valuable tool for organizations wanting to measure the security defenses against various levels of attack attempts by unauthorized individuals.
Penetration testing starts with careful planning. The test scope should be limited to what is important to the client to facilitate the identification of vulnerabilities.
At this stage, Iosentrix emphasizes a collaborative, intelligence-led approach—beginning with stakeholder interviews to define objectives, identify critical assets, and align testing boundaries with business priorities.
This is followed by establishing rules of engagement, including timeframes, authorization protocols, and acceptable testing methods. We use threat modeling to anticipate likely attack vectors to ensure the assessment simulates realistic adversarial behavior with minimized operational disruption.
Thorough documentation at this stage not only guides the execution but also ensures traceability and accountability throughout the engagement.
Penetration testing tools find and show security weaknesses, which help show how vulnerable the system is and allow for fixes. To detect security problems, Iosentrix combines automated scanning with targeted manual techniques to uncover common and complex vulnerabilities.
Each finding is validated to eliminate false positives, with detailed documentation to capture the technical root cause, potential impact, and real-world exploitability. This methodical, risk-based approach ensures that identified issues are accurate and aligned with the client’s operational and security context.
Read more on: Choosing the Right Penetration Testing Approach: Automated or Manual?
Ethical hackers use previously identified flaws to assess the extent of potential compromise, such as unauthorized access to sensitive data or privilege escalation. Every attempted breach is carefully documented, and strict adherence to client-approved boundaries and rules of engagement is maintained.
This process demonstrates the practical impact of vulnerabilities and provides actionable insights for remediation.
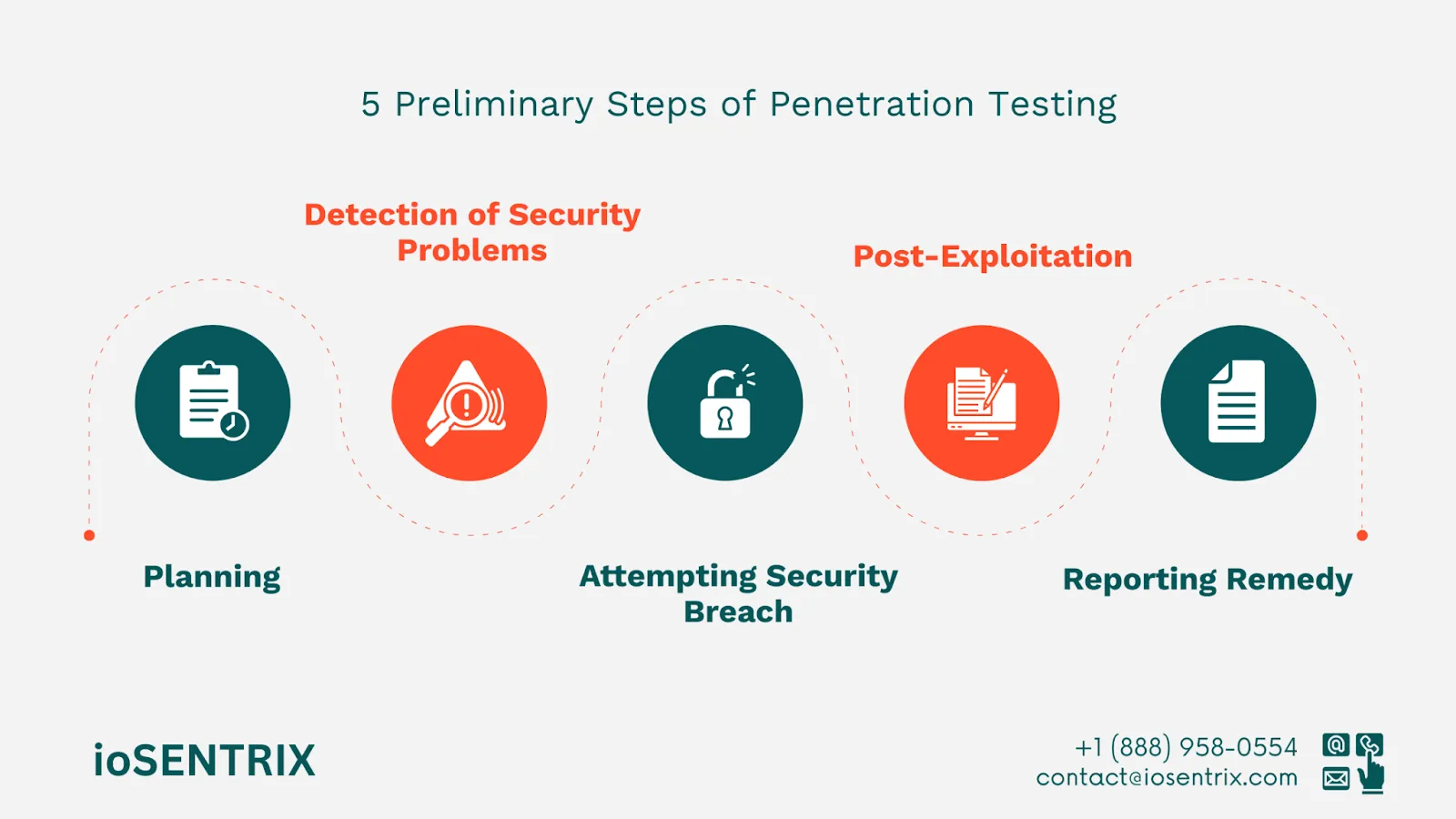
The report is given to the client to help fix the problem. This includes locating sensitive files, extracting credentials, or mapping internal network paths, all within ethical and predefined boundaries.
The goal is to demonstrate the potential business impact of a successful breach. Findings from this phase are contextualized in the final report, offering clear, evidence-based insights and remediation steps to help the client fix the vulnerabilities and understand the full scope of risk exposure.
The client receives a list of problems specific to the security breach that need fixing. The fix depends on the type of breach and its impact on the system. We deliver a comprehensive yet accessible report that outlines each vulnerability and prioritizes it based on risk severity and business relevance.
Clear remediation guidance is provided and customized to the client's environment and security maturity. Beyond technical fixes, the report includes strategic recommendations to prevent future incidents. The planning that began in the early phase ensures that each recommendation is practical, aligned with the original scope, and actionable within the client's operational constraints.
Don't just know about vulnerabilities; experience them. IoSENTRIX's penetration testing services go beyond basic assessments, actively probing your systems for exploitable weaknesses. Get the proactive security you need with our expert penetration testing.
Contact our experts to get started today!
While a vulnerability assessment identifies potential weaknesses, penetration testing actively exploits those vulnerabilities to determine their real-world impact and assess the effectiveness of your security controls.
Penetration testers use social engineering tactics as part of the process. These simulated attacks help evaluate how well your employees respond to phishing attempts and other social engineering techniques. This reveals vulnerabilities in security awareness training and highlights areas for improvement.
Penetration testing can identify vulnerabilities, including network security flaws, web application vulnerabilities, and system misconfigurations. It also uncovers weaknesses in your security infrastructure, like weak passwords, insecure protocols, and insecure system settings.
The price of penetration testing depends on the size and complexity of your system. A thorough assessment from a trusted company like IoSENTRIX offers valuable information about your vulnerabilities. This can prevent costly and damaging cyberattacks. We offer different pricing options to match various budgets.
IoSENTRIX provides a comprehensive report detailing the vulnerabilities discovered, their potential impact, and actionable recommendations for remediation. We collaborate with you to prioritize these findings, develop a security improvement plan, and implement effective solutions to enhance your organization's security posture.