
The energy sector plays a crucial role in ensuring the reliability of all critical industries, but it is increasingly becoming a target for cyberattacks. While high-profile incidents like the 2021 Colonial Pipeline attack may appear infrequent, many go unreported for security reasons. Cyberattacks are now considered one of the top global risks, with the energy sector being the most frequently targeted.
Anything that can harm or cause problems for the power system is seen as a threat. These threats may come from nature, technology, or human actions. Power system planners and operators do not usually have control over these threats, which can range from wildfires and cyclones to cyberattacks and more. Other threats include droughts, long-term temperature changes, and so on.
Various government departments and agencies, such as those focusing on energy, environment, and natural resources, meteorology, utilities, and power systems operations, along with experts in risk assessment and emergency management, play crucial roles in identifying potential threats. Below are examples of resources that could be examined to help in identifying these threats:
Assessing the vulnerability of power systems involves considering the probability of potential threats. Natural threats like disasters can be evaluated using historical threat data and climate projections. On the other hand, technological and human threats, which are often more variable than natural threats, can be assessed through stakeholder interviews for a qualitative score.
Read more about Analytical Threat Modeling for Power Systems.
In October 2020, six individuals linked to Russian intelligence faced charges in Pennsylvania for their involvement in the ‘Sandworm’ cyber operation. They were accused of hacking into chemical labs in the UK and Netherlands, targeting individuals at the 2018 Winter Olympics in Korea, and conducting a cyberattack on Ukraine’s electricity grid in 2015.
This incident, occurring a year subsequent to Russia’s annexation of Crimea, marked the first documented case of a successful power grid cyberattack. The attack resulted in the shutdown of 30 electrical substations, leading to approximately 230,000 individuals losing power for a duration of up to six hours.
Another example is the 2017 “NotPetya” ransomware incident that was aimed at a Ukrainian energy firm. This incident quickly spread throughout the company’s network, causing extensive disruptions in Europe and the United States.
The recent incident is included in a limited number of reports on cyber threats in the energy industry by the EU’s Computer Emergency Response Team since July 2019. Although it may seem like cyberattacks on energy companies and power grids are uncommon, the International Energy Agency (IEA) emphasizes that the threat is significant and increasing.
Grid operators generally do not disclose specific threats due to security concerns. Some threats may not even be detected. According to research conducted by Hornet Security, a German cloud security provider, energy was the most targeted sector for cyberattacks in 2019, with 16% of global attacks aimed at it.
According to the US Department of Energy, cybersecurity in the energy sector is considered a significant national security challenge. In the 2019 Worldwide Threat Assessment, it was noted that China and Russia possess the ability to interfere with critical energy systems. Furthermore, there has been a surge in malicious activities during the pandemic, driven by financial or geopolitical motives.
According to Anjos Nijk, managing director of the European Network for Cybersecurity (ENCS), airports are typically the initial target in conventional military operations, followed by attacks on the energy system.
Cyberattacks targeting electric and gas power companies can cause serious harm. The energy sector faces vulnerability in three main ways:
The energy sector’s cyberattack risk extends beyond just power plants. All the power systems, including energy transmission, distribution networks, supply chain partners, and network data, present potential vulnerabilities.
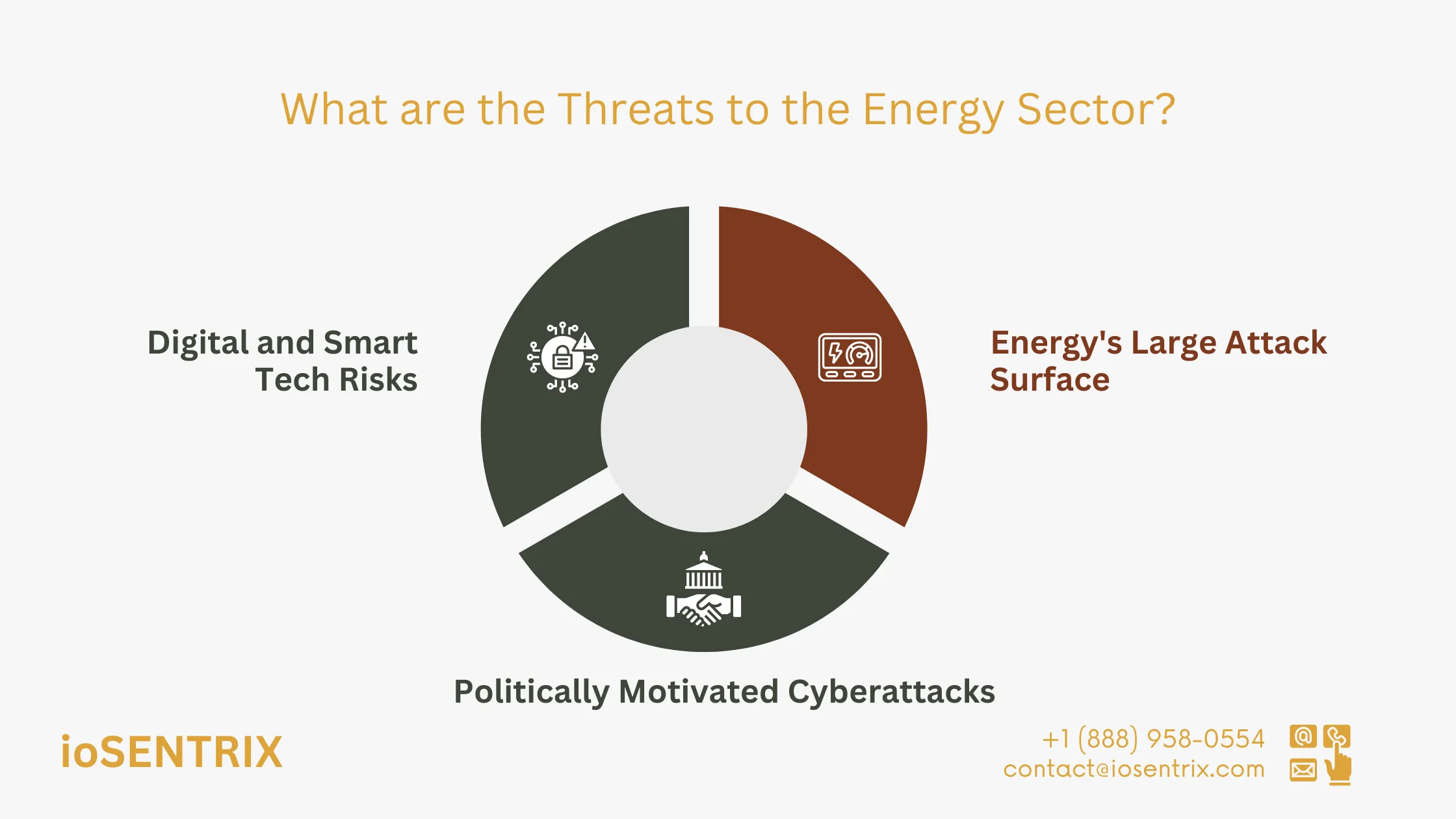
Political cyberattacks can be carried out by domestic hacktivists or nation-states as part of a broader strategy to respond to geopolitical events. In the first half of 2021, ransomware attacks doubled, with 54.9% of victims located in the US. The likelihood of facing consequences is low, as identifying the true source of these attacks is challenging.
The energy sector, traditionally a non-digital industry, is transforming digital advancements. While digitization offers many benefits, it also introduces risks. Operating systems now intersect with IT systems that follow different protocols. Additionally, the integration of customer-controlled ‘smart’ technology increases the number of weaknesses and flaws.
In most industries, cybersecurity is about balancing convenience, access, and protection. However, in the energy sector, cyberattacks can impact human health, safety, economies, and national security. Therefore, prioritizing the protection of public interests is crucial.
Damage from cyberattacks can quickly affect local, regional, and global partners within the energy supply chain. Every trusted vendor, piece of hardware, software, system, and individual in the supply chain is a potential target for cyber threats. Therefore, all parties must be trained in prevention techniques and prepared to fulfill their roles in a rapid recovery plan.
A key aspect of cybersecurity is having a plan for rapid recovery. Effective recovery planning was crucial in reducing losses during the 2015 Ukraine attack and the Colonial Pipeline breach in 2021. Both energy companies and government agencies play vital roles in maintaining energy reliability today.
Energy plant operators have traditionally stored sensitive data in offline devices, creating a physical disconnect between the data and potential cyber threats. However, hackers have found ways to breach this air gap and successfully attack offline hardware. Therefore, relying solely on air gaps ( a security method where a computer or network is isolated to stop any outside connections) is no longer sufficient for protecting data. Plant operators need to be more dynamic in their approach to cybersecurity.
The energy industry can be quite complicated. Operational Technology (OT) and Information Technology (IT) need to work together smoothly in a plant to prevent cyber threats. There is also a risk of cyber attacks in external energy supply chains. Energy companies need to consult with cybersecurity experts to evaluate and suggest effective security measures.