
Among the many digital systems used in healthcare, one of the most critical is the DICOM (Digital Imaging and Communications in Medicine) system. Developed to facilitate the exchange and storage of medical images, it is essential to safeguard DICOM against cyber attacks.
This article explains different strategies and best practices to ensure the security of your DICOM system.
Digital Imaging and Communications in Medicine (DICOM) serves as a global standard for storing and transmitting medical images. This standard outlines both a file format and a networking protocol. Additionally, it includes specific guidelines for storing files on various media types like compact discs.
The development of DICOM involved contributions from members of the DICOM standards committee, representing manufacturers and users such as the American College of Radiology (ACR), Radiological Society of North America (RSNA), European Society of Radiology (ESR), and other user groups like cardiologists.
A formal protocol, like DICOM, establishes how devices communicate with each other and store their program data. By adhering to the DICOM standard, different companies' devices can effectively communicate and operate within the same hospital environment.
In DICOM files, besides core imaging data (pixel information encoded differently), there is additional study and patient-related data. While the standard includes some security features, it also presents vulnerabilities in terms of cybersecurity.
Patient identification details are typically found in the header tags of DICOM files and sometimes within other file sections, like ultrasounds that may embed patient names or numbers in the images.
A DICOM file comprises several components: preamble, prefix, header, and image pixel intensity data. The header holds patient information, study acquisition parameters, image dimensions, matrix sizes, and color spaces.
The pixel intensity data, separated from the header by an attribute "7FE0," consists of a series of "1"s and "0"s that can be decoded into an image using information from the header.
DICOM works alongside the Health Level 7 (HL7) standard to exchange textual data among Hospital Information Systems (HIS), Radiology Information Systems (RIS), and Picture Archiving and Communication Systems (PACS).
DICOM systems, like any other digital system, are prone to unique cyber threats. It is vital to understand these attack vectors to implement effective security measures.
Effective preventive steps are necessary to restrict unauthorized entry to data stored in DICOM. This involves effective authentication methods like:
It's crucial to routinely check and adjust access permissions, apply session management methods, and monitor system logs to identify and stop unauthorized entry attempts.
Data interception occurs when information is illegally captured or redirected while moving through digital channels. Hackers often use this tactic to access confidential data without permission, usually for malicious purposes. During data interception, data meant for one recipient is mistakenly sent to an unauthorized party.
Those responsible for these actions typically aim to misuse the stolen data for criminal activities like identity theft, financial fraud, corporate espionage, and state-sponsored spying.
To safeguard data while it's being moved, it's important to use encryption methods like Transport Layer Security (TLS) or Secure Sockets Layer (SSL). It's also crucial to apply encryption for data stored in databases or on physical storage devices.
Keeping encryption methods up to date and using strong encryption algorithms improve the security of data protection measures.
A man-in-the-middle (MITM) attack occurs when a wrongdoer places themselves in a conversation between a user and an application, aiming to listen in or pretend to be one of the parties to create the illusion of a normal information exchange.
The objective of such an attack is to steal personal details like login information, account specifics, and credit card numbers.
Data acquired during an attack could be misused for various reasons, such as identity theft, unauthorized money transfers, or changing passwords without permission.
Such attacks pose a significant threat to DICOM systems.Following techniques are helpful to mitigate risks associated with man-in-the-middle attacks:
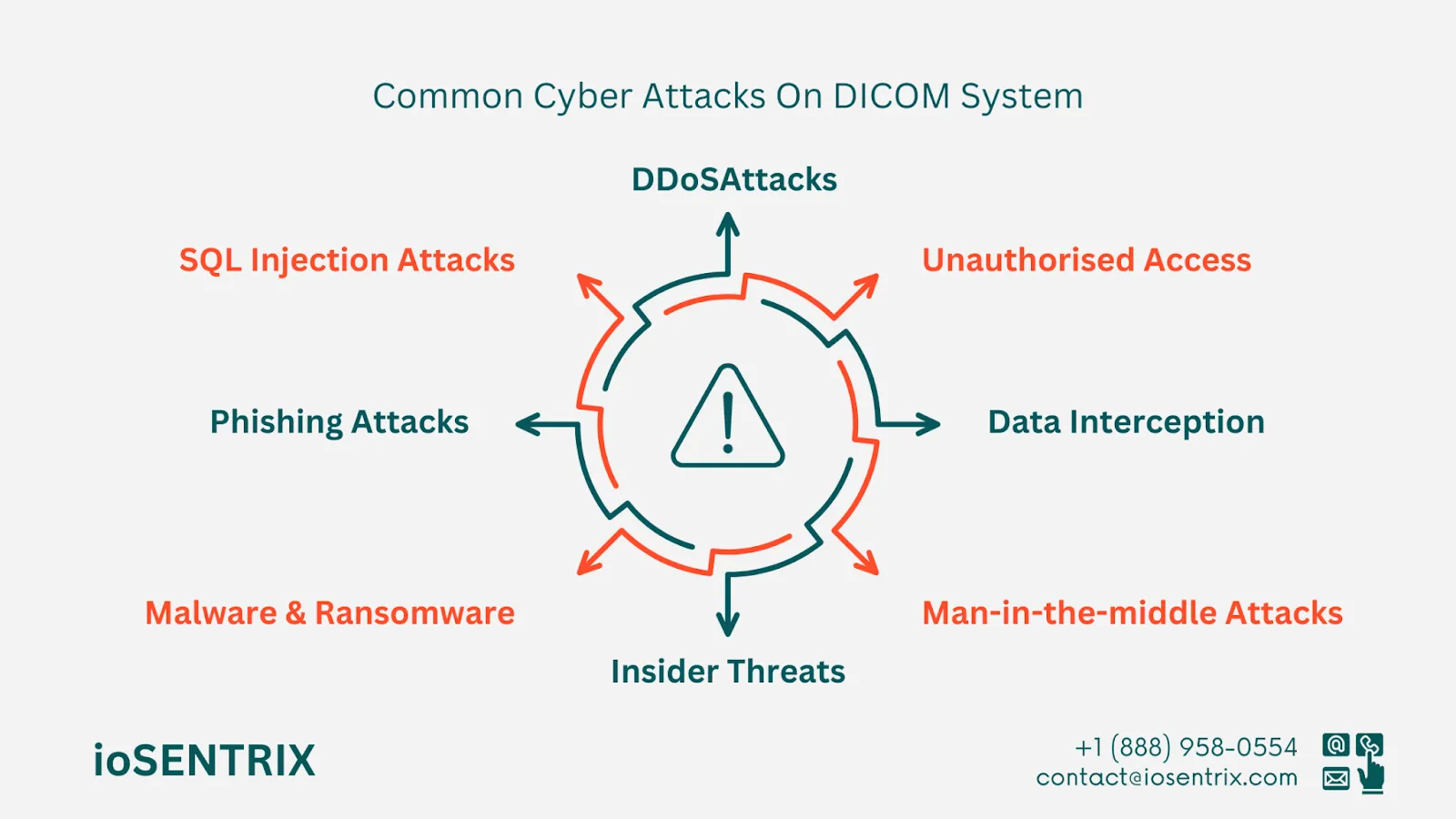
Ransomware is a malicious software that cybercriminals employ to infect computers, devices, and networks, limiting access to data until a payment is made. These attacks have affected businesses, hospitals, and public services globally.
Malware and ransomware pose severe threats to DICOM systems, potentially resulting in data loss and system downtime. To protect against these threats, organizations must:
Social engineering includes various harmful activities conducted through human interactions. It entails using psychological strategies to trick users into making security mistakes or disclosing sensitive information.
Common methods to cope with such vulnerabilities include:
Organizations should also implement strict access control policies, limiting the information shared in public domains, and using secure communication channels to protect against social engineering and phishing attacks.
SQL injection (SQLi) is a web security issue where an attacker can change the queries sent by an application to its database. This can enable the attacker to access unauthorized data, such as information from other users or any data accessible through the application.
SQL injection attacks exploit vulnerabilities in web-based applications that interact with DICOM databases. To prevent these attacks, organizations should:
The reasons behind launching a DDoS attack differ greatly, just like the kinds of people and groups interested in carrying out this type of cyber assault. Some attacks are done by unhappy individuals and activists who want to disrupt a company's servers to send a message, enjoy exploiting cyber vulnerabilities, or show their disapproval.
DDoS attacks can disrupt the availability and performance of DICOM systems, causing significant harm to the healthcare organization. Mitigation solutions include:
An insider is someone who has been given permission to access or knows about an organization's resources, such as staff, buildings, information, tools, networks, and systems.
For Example: A trusted individual within the organization, like employees, members of the organization, and those who have been provided with confidential information and access.
Insider threats can have severe consequences on the security of a DICOM system. Organizations should:
To prevent data breaches in DICOM, consider the following steps:
Maintain Secure Access Control: Restrict DICOM system access to approved staff, use role-based access controls, and enforce advanced password rules to stop unauthorized entry.
Use Encryption: Encrypt DICOM data both in transit and at rest to ensure intercepted data cannot be read without the correct decryption key.

How to Prevent a Cyber Attack on DICOM System
Ensure Secure Configuration: Configure all DICOM systems securely, including servers, and replace default passwords with strong ones.
Create an Incident Response Plan: Develop a response plan for data breaches or security incidents, outlining steps for containment, investigation, and reporting.
Limit Data Retention: Retain DICOM data only as long as necessary, reducing the risk and impact of a potential breach.
Ensure Regular Monitoring: Regularly monitor DICOM system activity and audit logs to detect and promptly investigate any unusual activity.
Conduct Regular Security Audits: Perform regular security audits to ensure compliance with industry standards and regulations, and to identify and address vulnerabilities.
Continuous Monitoring of Security Controls: Continuously monitor security controls to identify vulnerabilities and potential threats, staying ahead of security risks and zero-day attacks.
Limit Access on Personal Devices: Create a policy that limits or disallows access to DICOM images on personal devices to prevent loss or theft of sensitive data.
Vet Third-Party DICOM Software: Ensure that third-party DICOM software used for viewing and analyzing medical images is properly vetted to avoid vulnerabilities that could be exploited by attackers.
With more than ten years of experience in the industry and a team known for their technical expertise, ioSENTRIX is dedicated to shielding your organization from threats and adjusting to your specific needs. We guide you through a comprehensive security risk assessment and ensure that your systems meet industry security standards.
Our certified specialists have created specialized Do-It-Yourself Assessments for organizations equipped with a strong in-house IT team. Get in touch with an Expert today to discover how our services can benefit your organization.