For many years, encryption has been a valuable tool for keeping important information safe. Initially, encryption was mainly utilized by armed forces and governmental organizations. Nowadays, it is essential to protect data stored on devices or traveling over networks.
Data at rest pertains to information saved on computers and gadgets, while data in motion involves the transfer of data between devices and across networks.
Companies utilize encryption to shield confidential data from potential data breaches or unauthorized access, as these incidents could result in significant financial losses and harm the organization’s credibility.
“Data encryption is a way to change data from readable to non-readable form. This unreadable data can only be read by someone who has the decryption key. Only the sender and receiver must have access to this key.”
When implementing an encryption solution, it is important to understand that encryption can be targeted by various forms of attacks such as:
In a security system, there are three main parts: data, encryption mechanism, and key controller. These parts are typically kept separate to prevent the risk of one part being exposed, which could compromise the whole system. However, on a single device like a laptop, all three parts are operated together.
In a system with encryption, data is either unencrypted (plaintext) or encrypted (ciphertext). Encryption algorithms, also known as ciphers, are used to encode and decode data. These algorithms are mathematical methods that follow specific rules and logic to secure the data.
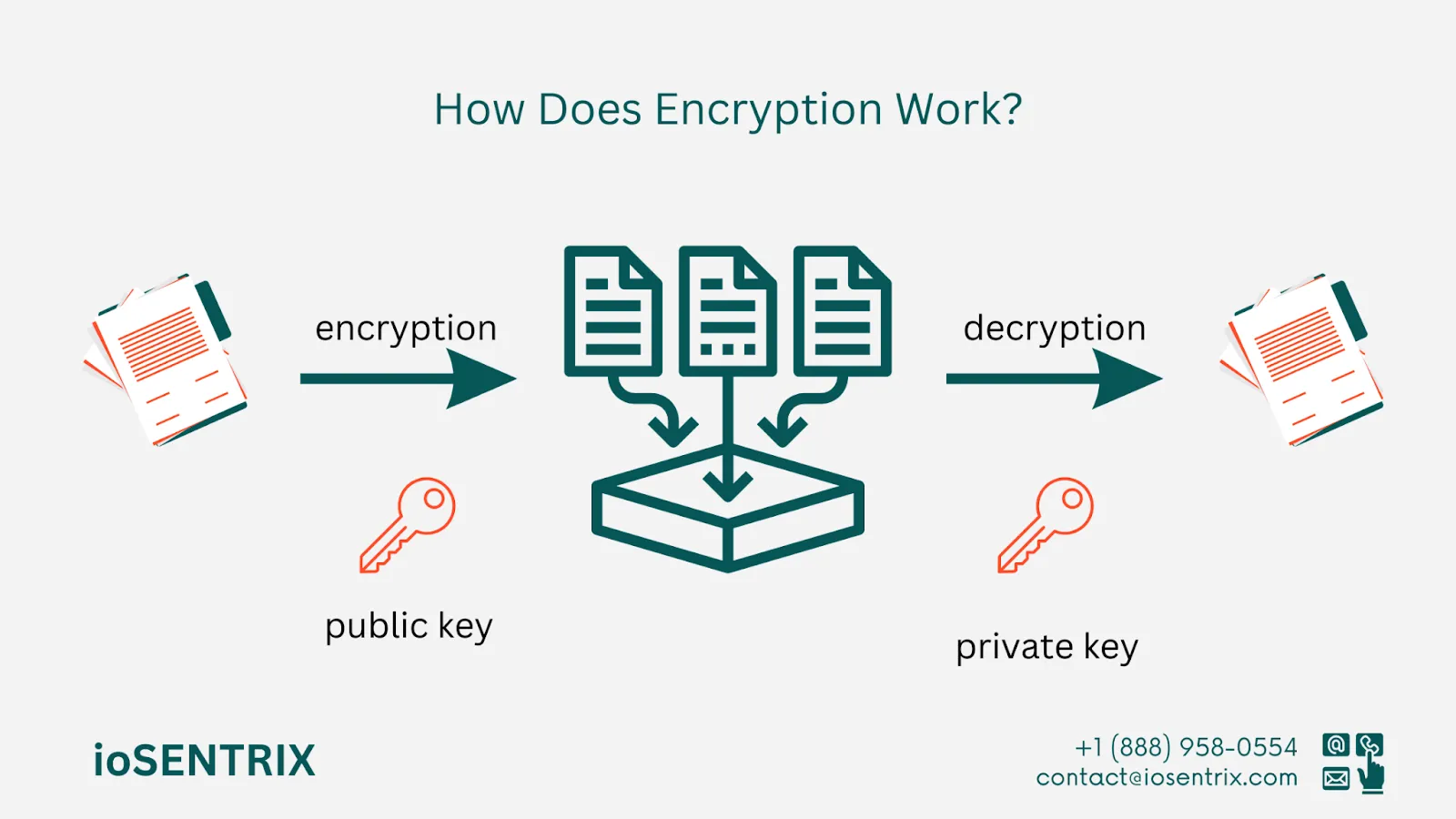
In the process of encryption, a tool called the encryption engine utilizes an encryption algorithm to convert data into a coded form. Various algorithms exist, each offering different levels of complexity and security. To create unique encoded data, the engine combines the encryption algorithm with an encryption key. This key, a randomly created sequence of bits, is unique to the algorithm.
Once the data is converted from plain text to encrypted text, it can only be decoded using the correct key. The key used for decoding could be the same for encoding the data or a different one, depending on the encryption algorithm - symmetric or asymmetric. In the case of a different key, it is commonly referred to as a decryption key.
When intercepted by an unauthorized party, encrypted data requires the intruder to guess the encryption method and key used to decrypt the information. Strong encryption algorithms and keys increase the difficulty of decrypting data.
The Data Encryption Standard (DES) is an old symmetric encryption method where you use one key for both encrypting and decrypting messages. DES uses a 56-bit key (8 bits are removed from the 64-bit key) and processes data in 64-bit blocks. As these key and block sizes are not sufficient for modern needs, newer encryption techniques have replaced DES.
In the past, Triple DES was commonly used as a symmetric algorithm. This method involves using three separate keys, each with 56 bits. Although the total key length reaches 168 bits, many experts believe that its actual key strength is closer to 112 bits.
The RSA asymmetric cipher was introduced to the public by Adi Shamir, Ron Rivest, and Leonard Adleman from the Massachusetts Institute of Technology. Prior to this, British mathematician Clifford Cocks had developed a public key algorithm in 1973, which remained classified by the U.K.’s Government Communications Headquarters until 1997.
Various protocols like Secure Shell (SSH), OpenPGP, Secure/Multipurpose Internet Mail Extensions, and Secure Sockets Layer/Transport Layer Security (TLS) use RSA for encryption and digital signatures.
The U.S. government selected a symmetric block cipher to secure classified information. This cipher is widely used in software and hardware globally to safeguard sensitive data. AES development began in 1997 by the National Institute of Standards and Technology (NIST) to replace the Data Encryption Standard (DES) as it was becoming susceptible to brute-force attacks.
An asymmetrical cipher relies on algebraic functions to create secure connections between key pairs. This method can lead to more efficient and faster cryptographic algorithms that offer similar levels of security but with shorter key lengths. These qualities make ECC algorithms a suitable option for IoT devices and other products that have restricted computing capabilities.
The QKD algorithm utilizes entangled photons to generate encryption keys, ensuring secure communication. Quantum entanglement allows users to detect any interference or alterations to the encryption key before data transmission. This real-time monitoring is possible due to the inherent properties of quantum information, where observation alters the data. Once the encryption is secure, the encrypted message can be safely transmitted over public internet channels.
A symmetric cipher that splits messages and encrypts them one at a time. Blowfish is a legacy algorithm, which is still effective, but has been succeeded by Twofish.
It was developed as a modern alternative to outdated encryption methods like DES and IDEA. Despite its initial popularity for being fast and easy to use, Blowfish is now being phased out in favor of more secure options like AES.
The algorithm is designed to work optimally on 32-bit central processing units. What makes Twofish unique compared to other encryption methods is its use of the S-box, a substitution box that is predetermined and dependent on the encryption key. The S-box helps to obscure the connection between the key and the encrypted data, although the decryption process still relies on the cipher key. Additionally, Twofish is an open-source algorithm that can be freely accessed and used.
Information that stays in one place without moving between devices or networks is referred to as data at rest. This can include data stored on a laptop, hard drive, flash drive, or in a database. Cyber attackers find data at rest appealing because it often contains important file names and organized data, revealing personal information, credit card numbers, intellectual property, and healthcare records.
It’s important to always be aware that hackers may be able to access stored data. To prevent data breaches, it is crucial to reduce the amount of stored data, maintain a list of all remaining data, and ensure that it is properly secured.
In many modern applications, users provide data which is then processed and stored in a database. The database is made up of files managed by an operating system and stored on physical storage like a flash hard drive.
Attackers may target data at rest, including cloud-stored data, because it often contains structured information that is easier to mine. Insider threats also pose a significant risk if data is improperly secured or accessible.
In a database, each column of data is encrypted individually. Using a different encryption key for each column helps improve flexibility and security.
This encryption process does not affect how applications interact with the database. Additionally, backups of the database are encrypted as well to prevent data loss in cases of stolen or compromised backup media.
Creators have the option to encrypt data in particular data fields by marking sensitive fields. This means that any information entered by users in these fields, such as credit card numbers, and bank account numbers, will be encrypted for added security.
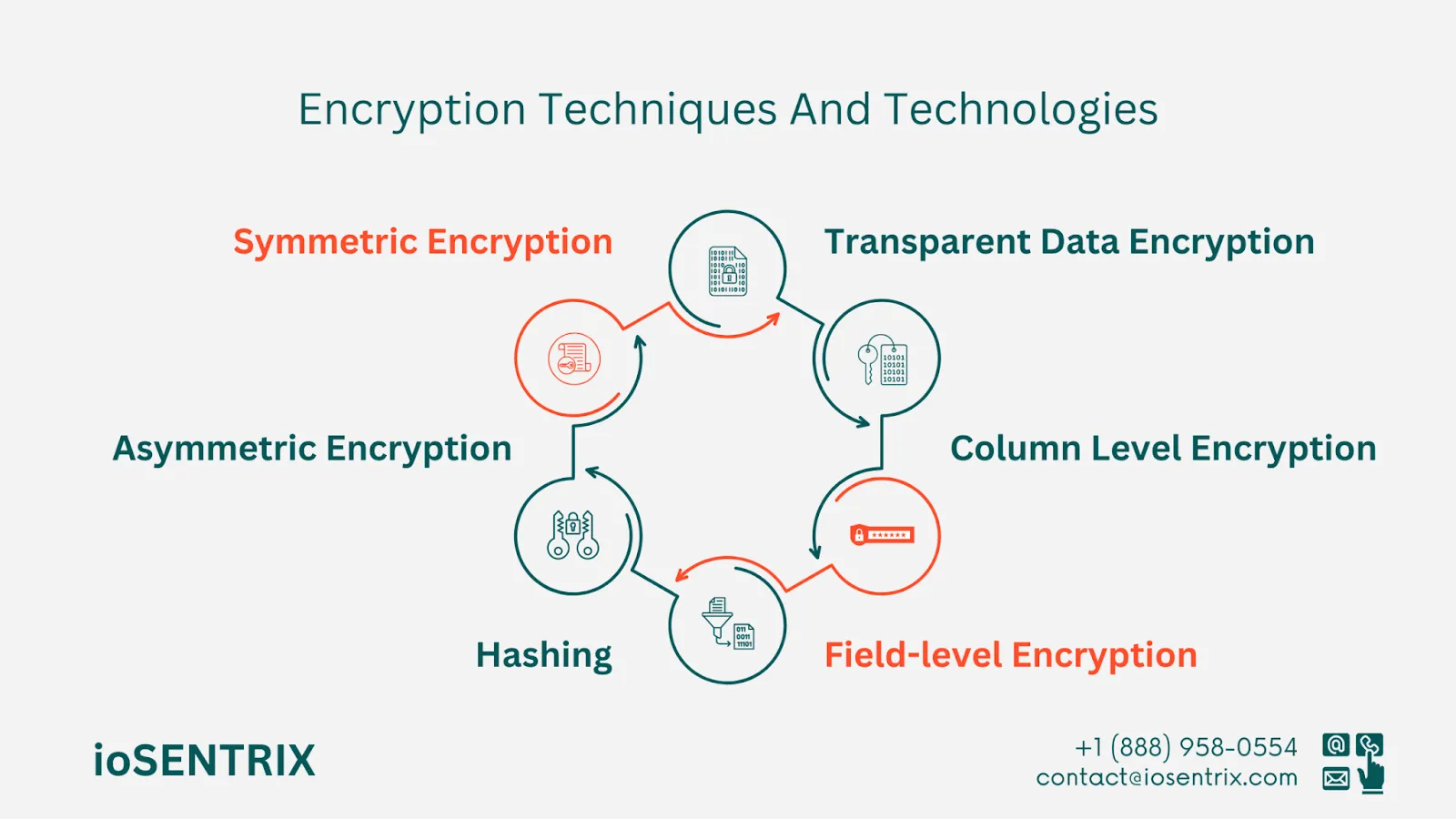
Hashing is a process that converts a long string of characters into a shorter fixed-length key or value that looks like the original string. It is often used in password systems for security reasons. When a user creates a password, it is saved as a hash. Later, when the user tries to log in, the password they enter is checked against the stored hash to verify its correctness.
Asymmetric encryption makes use of both public and private encryption keys. The public key is openly available and unique to each user, whereas the private key is a confidential key that only the user knows. Generally, the public key is utilized for encryption purposes, while the private key is used for decryption.
In data security, a private key is used to encrypt data, which makes it unreadable without decryption. Data is encrypted before saving and decrypted when accessed, as long as the key is available.
Symmetric encryption is faster and often more efficient for large data volumes, while asymmetric encryption offers secure key exchange but is computationally heavier.
Implementing database encryption, especially at the column level, can lead to a decrease in performance. This may make organizations hesitant to encrypt or secure all their data at rest.
Several RDBMS systems offer encryption and key-management features. It is simpler to implement database encryption when a data center uses databases from a single vendor. When overseeing databases from various suppliers, handling keys may present a challenge. Failure to properly manage keys can result in security risks.
Another potential danger is accidental data loss. If data is encrypted with powerful codes and the key is misplaced, the information becomes inaccessible. Losing or mishandling keys can lead to severe outcomes.
Data protection solutions that offer encryption services can safeguard devices, emails, and data files. These encryption features usually come with control options for managing devices, emails, and data. Businesses and institutions encounter the task of securing data and averting data breaches, given the frequent use of external devices, USB drives, and online tools by employees as part of their routine operations.
It is important to address the risk of sensitive data being mishandled by employees, who may save it on removable devices or transfer it to the cloud. Effective data loss prevention solutions can help prevent unauthorized data access, malware attacks, and data breaches. These solutions should monitor and control the use of devices and applications to ensure data security and incorporate automatic encryption to safeguard data even when it is outside the company's network.
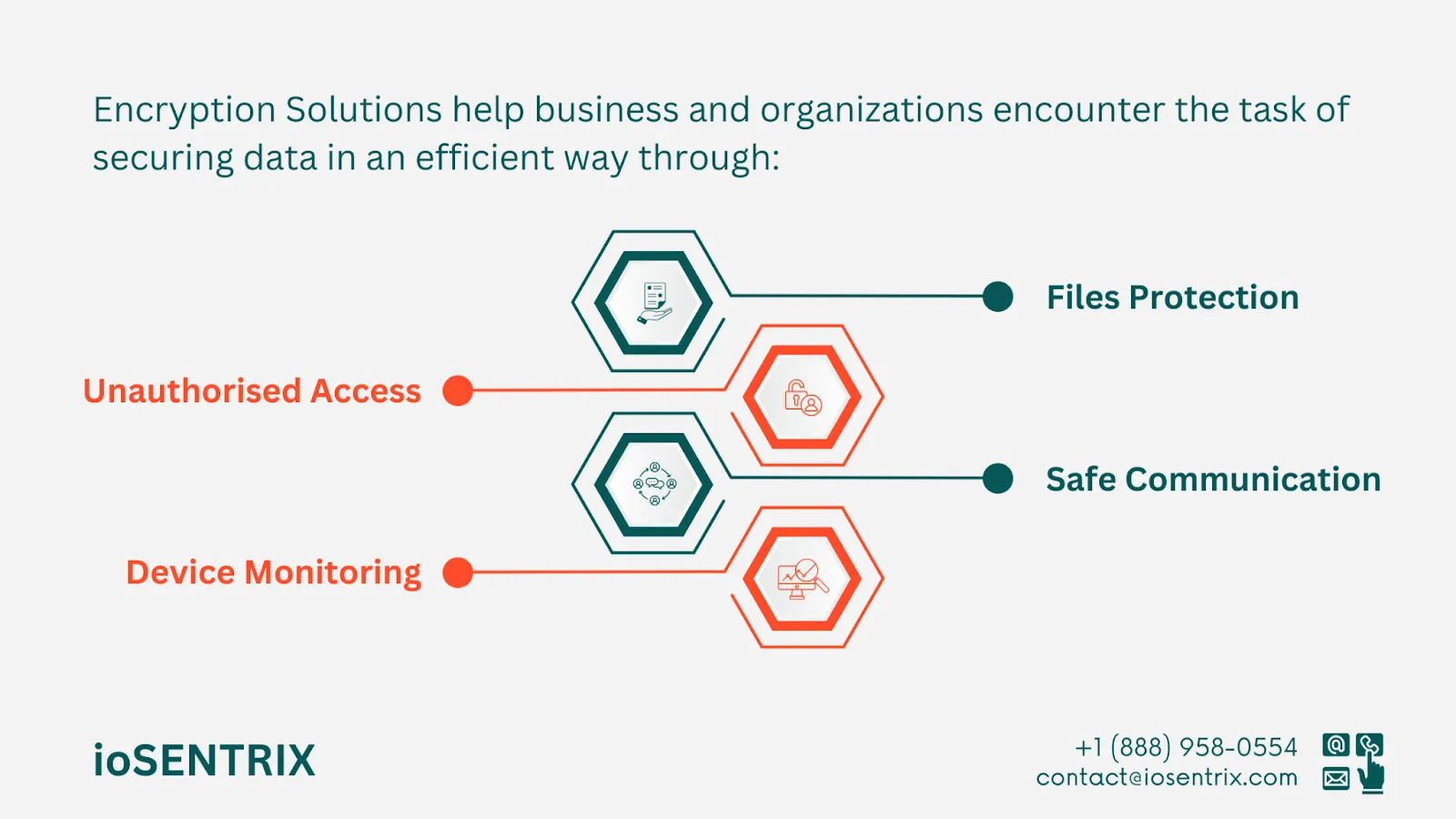
Email control and encryption are essential to meet regulatory requirements, support remote workers, accommodate BYOD policies, and outsource projects. Effective data loss prevention solutions enable employees to safely communicate via email by tagging, categorizing, and encrypting sensitive information in messages and attachments. Leading data loss prevention tools can also detect, block, and encrypt confidential data based on various factors like user, data type, and recipient.
Although data encryption may appear overwhelming and complex, data loss prevention software effectively manages it on a daily basis. Your organization does not need to tackle data encryption independently. Select a reputable data loss prevention software that includes data encryption along with device, email, and application control to ensure the safety of your data.
ioSENTRIX’s data security solution enhances the security of your data by adding extra layers of protection, in addition to your existing data encryption measures.
To Learn More about our encryption solutions, please contact us here.