
The process of cybersecurity due diligence involves investigating a company’s online systems before entering into any business transaction. This includes reviewing all important aspects to ensure a clear understanding of the situation and make informed decisions.
Although it is often mandatory by law, due diligence is commonly associated with voluntary investigations. In many industries, due diligence is the process through which a potential buyer evaluates a target company or its assets before an acquisition.
Every day, businesses face risks not only from cyberattacks but also from within their operations. Using third-party and fourth-party vendors has become essential for successful organizations, yet it brings hidden risks.
To prevent these risks, companies conduct thorough due diligence reviews of all their associations, partners, and prospects. This is done to safeguard against cyber threats and reduce liability in case of compromised sensitive information.
Due diligence may appear burdensome initially, but it is a necessary step to prevent possible problems. Therefore, when evaluating a potential business partnership, it is important to remember to conduct your due diligence.
Cyber due diligence is an essential process that evaluates a company’s online systems and potential third-party risks to determine its overall risk level. This helps in informed decisions when considering investments, purchases, or mergers with the company. In simpler terms, it is like inspecting a house thoroughly before buying it to identify potential issues.
Cyber due diligence is so important because:
Yes, both due diligence and due care are important for managing risks and complying with regulations, but they have distinct differences.
Due diligence involves a structured investigation to ensure tasks are performed correctly and all risks are identified, typically during transactions like mergers or acquisitions. Due care, on the other hand, refers to the day-to-day actions taken to protect an organization’s assets, such as implementing regular security updates and employee training.
While due care is more informal, due diligence is a more rigorous process that involves thorough investigation and verification of all relevant information. This complete process can be seen as an investigation or audit to gather and confirm all necessary facts and figures.
Mergers and acquisitions, also known as M&A, involve transferring or combining ownership of companies. Cyber due diligence plays a significant role in this process by assessing a company’s cybersecurity status before such transactions take place. This evaluation is an important component of any merger and acquisition security checklist.
During cybersecurity in mergers and acquisitions, the focus is on examining the organization’s existing cybersecurity policies, data privacy regulations, incident response strategies, regulatory adherence, and prior security breaches. Additionally, assessments may include a review of supply chain and third-party vendors’ security practices.
The process of security due diligence means:
Any business deal must understand the cybersecurity risks related to a company’s M&A operations to secure investments for the long term.
Cybersecurity due diligence is highly advantageous for companies globally. It helps organizations evaluate risks before agreeing to mergers or acquisitions and addresses any concerns that could affect deal structures.
Additionally, it aids in understanding the cybersecurity threats and enables the assessment of an entity’s overall cybersecurity position.
Let’s examine the significance of cybersecurity due diligence and understand why it is important.
Third-party risk management (TPRM) is recognizing, evaluating, and managing risks from dealing with third parties, like suppliers and partners. TPRM uses guidelines and structures to guarantee that third parties:
When individuals without permission gain entry to confidential information or exploit the digital environment as a means to carry out cyber attacks, it is known as an infiltrated server.
Servers are at risk of being compromised because of:
Influencing servers can harm a company's reputation and lead to data breaches or cyber-attacks. Cyber due diligence is essential for identifying and addressing security vulnerabilities.

A ransomware attack occurs when cybercriminals block someone’s data or online systems until a ransom is paid. These attackers may use methods like phishing emails, supply chain attacks, or scams to gain access to an organization’s systems and then lock them out.
Industries like IT, construction, and healthcare are particularly vulnerable, but no sector is safe. Preventing ransomware attacks requires regular system backups, robust phishing awareness training for employees, and using endpoint protection to detect suspicious activity early
The Enterprise Security Posture Score (EPSS) is one metric used to assess a company’s overall cybersecurity effectiveness. While not the only available metric, it provides insight into how well security controls and risk management strategies are implemented
An EPSS is calculated based on:
The security policies, procedures, and guidelines of the organization are analyzed to determine how well they align with industry standards and regulatory demands.
Assessing the company’s risk management structure involves examining how risks are identified, assessed, mitigated, and monitored, as well as how they are reported within the organization.
How well the organization's technical and administrative safeguards, like firewalls, access controls, encryption methods, intrusion detection tools, and incident response plans, are working to safeguard sensitive data and systems.
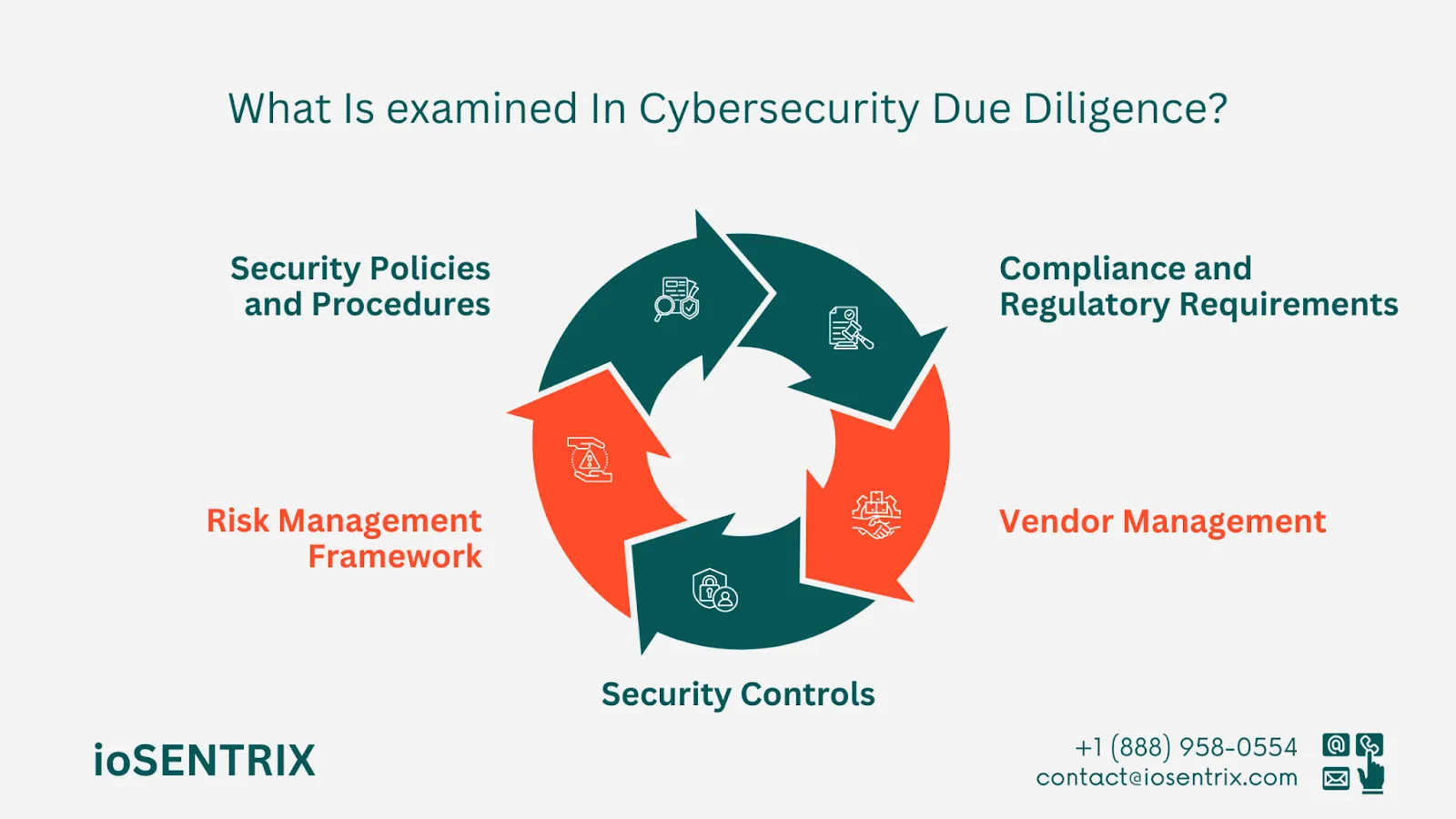
The organization follows laws, regulations, and industry standards related to data protection and information security, like GDPR, HIPAA, PCI DSS, or ISO 27001.
When conducting due diligence on a third-party vendor, it is crucial to review the vendor’s cybersecurity measures. This involves examining their security protocols, how they manage data, and their vendor management procedures.
If you are unfamiliar with cyber due diligence, there is a simple questionnaire available to provide you with a general understanding of a company’s cybersecurity status.
No matter the circumstances, using this questionnaire and investing in trustworthy services like ioSENRTIX help you meet all cybersecurity standards and have the necessary knowledge to protect your business in the long term.
For more information, reach out to our professionals.