
The previous few months have been a roller coaster ride for the entire security industry because of the emerging cyber-attacks targeting security organizations, researchers, and service providers.
The rise of cyber risk shows no clue of diminishing down, whereas the experts estimate the increase in cyber risks and threats in 2021 as hackers continue to follow the least path and take more advantage of pandemic and remote work. Covid-19 has left a considerable mark on the global cybersecurity market that is expected to grow from $183.2 billion in 2019 to $230.0 billion by 2021.
When it comes to securing your organization and putting strict limitations over your valuable assets and information, there are only two questions you must ask yourselves on behalf of your organization.
The questions might sound light to you, or you must be thinking my business is not the type that can be hacked, or why would anyone be interested in hacking my organization.
You might not know, but it is always valuable for cybercriminals and intruders, whatever your business niche is. You might get hacked, and you might not even know about that.
It usually takes over six months for most organizations to detect data breaches. You must not take it lightly because the consequences of already being hacked or on the edge of being hacked can be a nightmare for you and your organization.
Obviously, you would not want authorities knocking at your door with huge penalties, nor would you like your organization’s reputation to go in vain.
Among others, the two security assessments that can prevent you from being a cyber-attack victim, and those are Compromise Assessment and Penetration Testing.
In this blog post, we have put together all the required information you would need to understand these two in order to avail of any assessment according to your business requirements, current or future necessities.
Moving towards a proactive approach to revamp and implement necessary security checks is more important than ever. We have penned down all the required directions that you may need to establish security work to safeguard your business from being breached.
So, Let’s start with the basics.
Compromise assessment is a security assessment and answers the fundamental business security operational question, “Are we breached?” through analyzing various security measures.
CA delivers a high-level review and audit of the organization’s networks, applications, infrastructures, and end-points based on suspicious user behaviors, logs, compliances policies, Indicators of Compromise (IOCs), or any evidence of malicious activities to identify attackers residing in the current environment or active in the past.
On the other round, penetration testing is another security assessment that answers the simple question, “Can we be breached or hacked?” with practical and appropriate techniques. Pentesting is conducted to find exploitable vulnerabilities.
In it, vulnerabilities are often chained up to gain access in order to perform malicious activities, as well as to understand the severity of identified threats.
Interested in learning more about penetration testing? Check our detailed blog post on penetration testing, and why do you need it?
Compromise assessment and penetration testing are different from each other in several ways. Since both assessments cover wholly different aspects of cybersecurity, there is no way you can compare them or prioritize any of them when it comes to performing them.
Here are a few notable differences between compromise assessment and penetration testing that you must understand:
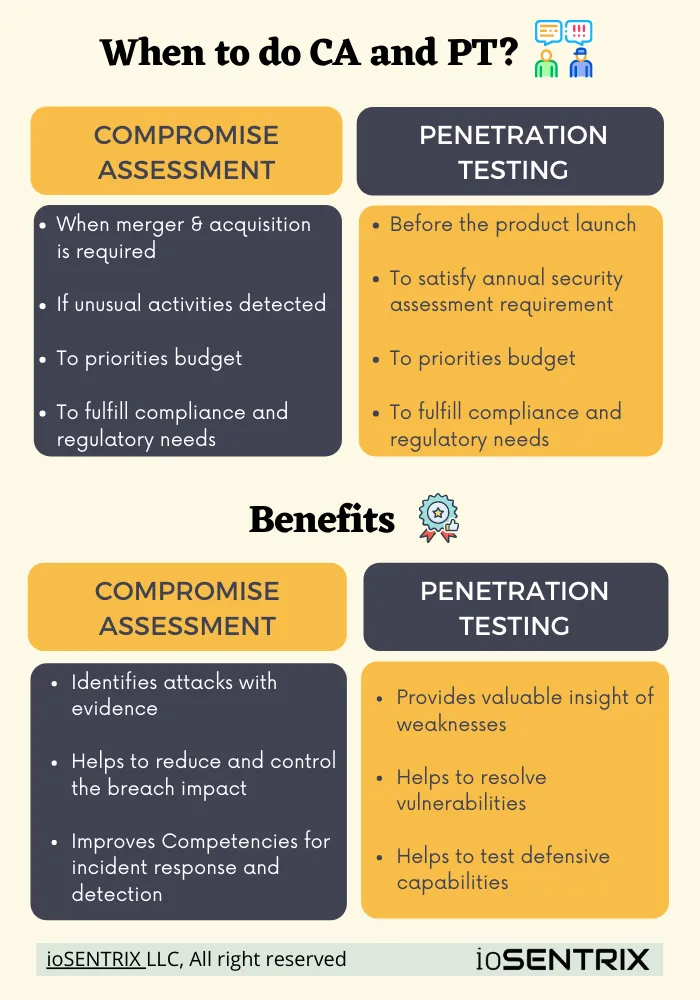
Whether it is compromise assessment or penetration testing, they both serve the same goal of identifying adversarial movement opportunities. They are essential in the fast-growing world of APTs and develop on distinct needs and circumstances. Here are the most critical two cases when both become essential to perform.
Merger & Acquisition
Performing CA during the merger and acquisition process helps examine the organization’s exposure to cyber risks, identifies threats in the early stage, and evaluates the acquisition’s environment, current security posture. This also plays a massive role in determining the risk profile of the acquisition of an organization as well as facilitates the decision to initiate the M&A process.
On behalf of the assessment results, you can decide whether the acquisition target is beneficial for your business and the network connectivity or app integration should continue or stop. In addition to that, it also assists in evaluating the security measures and controls that would be required before and after the alliance is completed.
Unusual activities
Noticing your network’s abnormal behavior while doing the compromise assessment can not only help you hunt down the reason behind the activities but also prepare you to design a sustainable remediation plan as well. In many cases, suspicious behavior on databases, application servers, unusual data transmission, or network applications utilizing bandwidth than the normal could be a reason for an advanced threat actor residing and controlling the data transmission to obscure servers. Such abnormal activities are IoC of breaches that one must look for through proper compromise assessment.
Before Product launch
It is beneficial to do a penetration test of the product before its launch. Because that way, you would be able to find vulnerabilities in your product before a hacker can exploit them. Through this, pentester would be able to interpret the weaknesses that the dev team might not have considered or found out.
Annual security assessment requirements
In order to remain secure and prepare in-defense, businesses need to evaluate their critical assets at least annually. Organizations have many reasons to take proactive measures to classify and quantify the cyber risks targeting the external or internal network environment. Through penetration testing; businesses can examine their security requirements and reconsider the priorities with the evolving cyber threat TTPs and identify the loopholes that might affect the overall IT and security policies of the organization.
Here are a few more cases to which both assessments mutually contribute to.
Compliances and Regulatory needs
This matter remains constant in both (i.e., compromise assessment and pentest) scenarios. They help distinguish the security gaps that refrain your business from reaching and adopting security compliances and certifications. Whether your business requires PCI DSS, GLBA, ISACA, HIPAA, COBIT, or other regulatory requirements, these two can further map out all those specific demands that your business lags.
Budget Priorities
Once you have analyzed your business assets with a suitable security assessment, either with pentest or CA, you can better prepare security programs with the focused area to spend the most or minimal budget. It also supports you to classify whether your business requires more frequent testing, security training, other assessments or resources.
Use this link to download this Compromise Assessment vs Penetration Testing infographic in PDF format.
There are countless benefits of both assessments that help the organization level up its security posture. We are going to touch a few that make them a must to do. Let’s take a quick glimpse at their benefits.
Cyber adversaries are taking over the world like a storm, and advanced threat actors are becoming more and more sophisticated and persistent. It is important to determine the weaknesses to develop adequate controllers. Breaches can go undetected for months and sometimes even years.
Today, cyber-attack has become a norm, and there is no more “security” without efforts. Advanced threat actors love to lurk into your infrastructure to mine their desirable data; sometimes, they do it in exchange for money, and sometimes they are state-sponsored. The havoc 2020 has caused to businesses in terms of security is quite devastating.
It is often the internal weaknesses that let the attacker come inside; sometimes, it happens due to newly deployed applications, infrastructure, and the other time it occurs due to a third-party vendor or product.
With penetration testing, you can test your application, internal or external environment, your organization’s intrusion, detection abilities and look for newly discovered vulnerabilities as well as 0-day exploits to protect against external threats.
Whereas compromise assessment can help you find out the lurking attacker that has been gone undetected due to previously failed security checks.
Cyber-attack tactics are evolving as per reports, and cybercrime is expected to reach $10.5 trillion annually by 2025. In contrast, vulnerabilities ramification is going to be a struggle for many organizations into 2021 and beyond.
To stay ahead of attackers, it is now necessary to not leave any open security hole that can provide any succeeding path to the attacker(s).
Do your part and be well-versed in the changing world of cybersecurity and always put security controls first and continuously monitor your assets so that if any attacker aims at your network, you have your necessary security measures in place.
Identify and eliminate vulnerabilities through regular penetration testing to reduce the risk of breaches. It is also required to keep tabs on emerging cyber threats and attack trends. However, you can do one more thing from your end to stay ahead of attackers by performing a compromise assessment at-least annually to identify if you have been breached recently or any past intrusions.
As a trusted cybersecurity partner, we have provided our compromise assessment and penetration testing service to fortune 500 companies and helped them protect their critical assets and reputation. Schedule a meeting today with us and see how ioSENTRIX can make your organization secure from upcoming cyberattacks