
AppSec, short for Application Security, is the practice of securing applications by identifying and addressing potential threats throughout the software development life cycle. It aims to protect applications from attacks that compromise data confidentiality, integrity, or availability.
DevSecOps builds on this foundation by incorporating security best practices into the Software Development Lifecycle (SDLC). DevSecOps is a security-focused extension of the DevOps methodology that emphasizes collaboration between developers and security professionals throughout the software development life cycle.
In other words, while Application Security (AppSec) ensures the security of applications with a focus on high-level considerations like process, design, and requirements, DevSecOps is geared explicitly towards embedding security seamlessly into the DevOps cycle to prevent introducing vulnerabilities.
This collaborative approach helps create a security culture, reinforcing the importance of security in the development lifecycle. Together, AppSec and DevSecOps are essential for ensuring the safety and security of digital products and systems.
When it comes to securing software applications, there can be confusion surrounding two primary perspectives: Application Security (AppSec) and Development, Security, and Operations (DevSecOps). Think of AppSec as the overarching forest, covering a wide range of considerations such as process, design, and requirements.
On the other hand, DevSecOps is a specific area within this forest, focusing on seamlessly integrating security practices into the DevOps cycle to prevent vulnerabilities from taking root. AppSec takes a holistic view, ensuring the overall security of applications, while DevSecOps hones in on integrating security measures during development and operations. Despite their slightly distinct roles, both AppSec and DevSecOps ultimately share the goal of enhancing applications’ security.
AppSec is a broader umbrella covering all aspects of application security, from design review and threat modeling to logging and cryptography standards. The goal of AppSec is to ensure the overall security of the application. It involves identifying potential security risks and taking steps to mitigate those risks before attackers can exploit them.
For example, AppSec may include designing an application with security in mind, including encryption protocols or secure login procedures. It may also involve implementing logging standards to track user activity or monitoring for security events that could indicate a breach.
On the other hand, DevSecOps is an area within AppSec that focuses specifically on integrating security into the development and operations process. DevSecOps aims to build security into the development process, shifting it to the left and automating security testing to identify vulnerabilities earlier and more efficiently. This approach integrates security testing and other security measures into the software development process, ensuring that teams consider security at every stage of development.
By integrating security testing and other security measures into the software development process, teams can identify vulnerabilities earlier and take corrective action before releasing the application into production.
DevSecOps involves a variety of tools and practices, i.e., Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and more. These tools help developers identify vulnerabilities and other security risks earlier in the development process, allowing them to address these issues more efficiently.
Additionally, DevSecOps can use Continuous Integration/Continuous Deployment (CI/CD) pipelines, which automate the testing and deployment of code, allowing for more frequent updates and faster delivery times.
While AppSec and DevSecOps have different focuses, they share common goals and practices. Both approaches seek to improve application security by integrating security testing into the development process and automating security testing as much as possible. By adopting AppSec and DevSecOps approaches, organizations can build more secure applications faster and more efficiently, reducing the risk of security incidents like data breaches.
Overall, the application security landscape can be considered a forest, with AppSec as the more giant, overarching umbrella covering all aspects of application security and DevSecOps as a specific area within that forest that focuses on integrating security into the development and operations process. Together, these approaches help organizations build more secure applications and reduce the risk of security incidents.
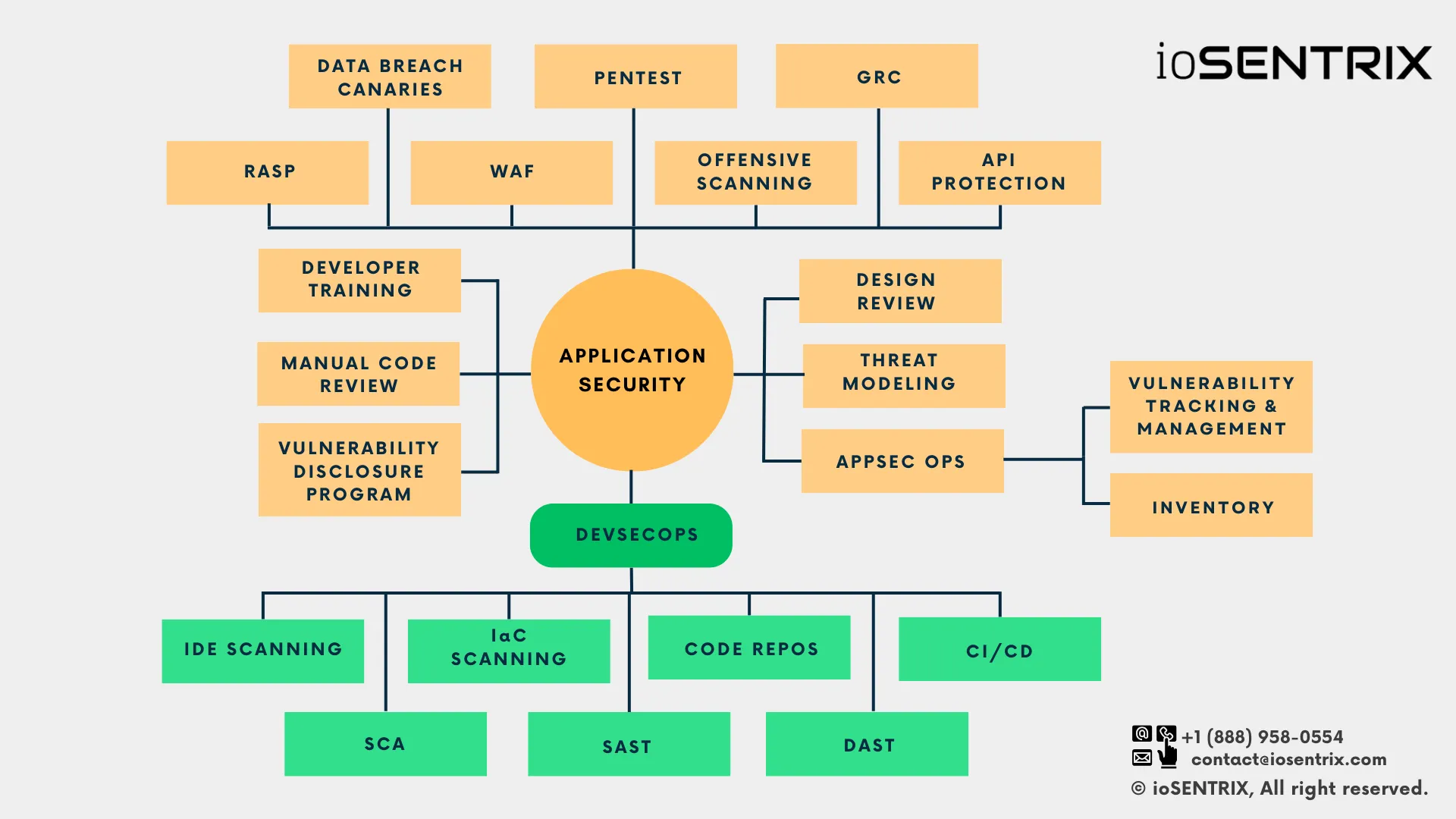
Use this link to download this AppSec and DevSecOps Mindmap.
AppSec is a forest, and DevSecOps is an area in that forest.
Application Security is a comprehensive approach to protecting the integrity and safety of an application. It contains various activities, tools, processes, and technologies that work together to identify, monitor, and mitigate threats before they become a problem. Within AppSec, DevSecOps is a specific component that seamlessly integrates security into the software development life cycle (SDLC). Notably, the following practices fall under the umbrella of both AppSec and DevSecOps:
Application security (AppSec) is critical in today’s digital landscape, where applications are often accessed over various networks and connected to the cloud, leaving them vulnerable to security threats and breaches. It provides organizations with a comprehensive framework to protect their applications and establish effective policies and procedures to ensure that applications are built securely.
AppSec helps organizations identify vulnerabilities in their applications and take steps to address them. It also enables organizations to set up effective authentication protocols, access controls, and encryption algorithms and define how data should be handled, stored and secured (by following security and privacy). This not only helps organizations protect their applications but also helps them comply with data protection and privacy regulations.
Furthermore, AppSec helps organizations classify their applications based on their risk levels, determining what security measures are needed for each application. This allows organizations to set up Service Level Agreements (SLAs) based on the risk level of each app and define acceptable performance thresholds. AppSec guides you on how to classify the applications, use crypto libraries and which solutions are approved when developing an application. It also outlines logging requirements for fraud detection and audit purposes.
AppSec sets standards and best practices around development, coding, deployment, testing, maintenance, and operations to ensure that application code is secure. It allows organizations to define access control policies that determine who can access sensitive data within an application and how they can access it.
Developers and security teams must collaborate effectively to reduce risk across the organization. AppSec enables a more effective collaboration between developers and security teams to mitigate risk across the organization. It provides a framework for continuously monitoring code changes throughout production environments to identify any vulnerabilities quickly before they become exploitable or cause harm.
Organizations of all sizes are increasingly targeted by cyberattacks, making ensuring that applications and infrastructure are secure from the start even more critical. To achieve this, organizations must adopt a complete software development life cycle (SDLC) that includes security in every phase(SSDLC). This includes implementing best practices such as understanding the OWASP Top 10 Threats and performing vulnerability scans throughout the life cycle. Additionally, organizations should instill a culture of secure development to ensure that security is always considered.
Understanding application security requirements from the very start of the SDLC is essential. The organization must consider relevant industry-specific standards or guidelines when developing security requirements. Once established, these requirements must be consistently maintained throughout the SDLC. This will help ensure that all applications deployed comply with regulatory standards and organizational policies.
To ensure security, an application’s secure design and architecture must also be considered during the SDLC. Specific considerations, such as authentication protocols, authorization rules, input validation processes, data encryption strategies, and logging mechanisms, must be made when designing an application. These factors will help reduce attack surfaces and mitigate potential risks associated with malicious actors or vulnerabilities in third-party components/libraries.
In the realm of application security, as software development grows in complexity, the implementation of secure coding practices becomes increasingly vital to safeguard against malicious actors and vulnerabilities in code. Developers should integrate strategies such as strict input validation, robust authentication controls like Two-Factor Authentication, and proper authorization rulesets, including access control lists. Employing appropriate cryptographic techniques for the storage and transmission of sensitive data, along with effective key management practices, is also crucial.
These measures significantly reduce an organization’s risk profile, as many cyberattacks exploit vulnerable code. To ensure the effectiveness of these practices, it’s essential to conduct thorough reviews of applications through Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and manual code reviews. This helps in identifying potential vulnerabilities. Additionally, carrying out penetration tests is a key step in prioritizing and managing any vulnerabilities that are identified, further fortifying the application’s security posture.
Finally, organizations need to instill a culture of secure development across all teams involved in creating software solutions throughout the SDLC process—from product owners to developers—to effectively protect against common threats like injection attacks or cross-site scripting attempts by malicious actors or weaknesses within third-party components/libraries employed within applications/infrastructure solutions deployed by the organization(s).
This means including security training programs for teams throughout each stage of development—from system design through deployment—and instituting periodic reviews on current threats. General awareness campaigns focused on information security topics pertinent to those involved with the application(s)/infrastructure solution(s).
Analyzing the severity of vulnerabilities requires considering both technical and business impacts. To reduce potential threats, threat modeling, [SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing)] (https://iosentrix.com/blog/SAST-vs-DAST-What-is-the-Difference/), and Software Composition Analysis (SCA) should be incorporated into the Software Development Life Cycle (SDLC) process to identify vulnerabilities quickly and automate security testing. Setting up Service Level Agreements (SLAs) is also recommended to promptly implement any applicable software patches.
Companies should adopt secure Application Security, SDLC, and DevSecOps practices to stay ahead of rapidly changing security requirements. Utilizing a secure design approach in combination with mandating threat modeling will further increase security across all applications. Additionally, performing SCA helps detect third-party components with known vulnerabilities. Regularly scanning applications with automated vulnerability assessment solutions can also help detect potential security flaws before they become an issue.
To ensure a comprehensive approach to security, organizations should document an incident response plan in advance and periodically assess their product with relevant security assessments. This allows them to identify potential security issues before they can be exploited and take measures to mitigate them.
Creating a vulnerability disclosure program can help organizations avoid potential security threats by allowing external researchers or “white hat” hackers to report any security flaws or vulnerabilities they find in the company’s software products. This helps organizations identify potential threats before they can be used maliciously against them.
Any organization looking to implement AppSec or DevSecOps will face particular challenges. One challenge is getting started. AppSec and DevSecOps can seem daunting, and knowing where to begin can be challenging. Another common challenge is resistance from Development teams. AppSec and DevSecOps can require changes in how development teams work; some may be reluctant to embrace those changes. Finally, there is the challenge of maintaining AppSec and DevSecOps over time. Implementing AppSec and DevSecOps is a continuous process, and it cannot be easy to maintain momentum once the initial implementation is complete.
Fortunately, there are ways to overcome these challenges. One way to get started is to find an AppSec or DevSecOps guru to help you get your organization on track. Employee resistance can be addressed by communicating the benefits of AppSec and DevSecOps and by providing training to help employees understand the implemented changes. Finally, the key to sustaining AppSec and DevSecOps over time is to make them part of your organization’s culture. The AppSec and DevsecOps processes should be integrated into SDLC.
Both teams need to partner(security and dev) to make this successful, and AppSec should be perceived as an ally rather than a show-stopper for Dev teams. Appoint an AppSec or DevSecOps champion, create incentives for employees who embrace AppSec and DevsecOps, and ensure that everyone in your organization understands the importance of AppSec and DevSecOps. By addressing these challenges head-on, you can ensure that your organization’s AppSec or Devsecops implementation is successful.
In today’s digital landscape, Application Security and DevSecOps play a vital role in protecting companies against cyber threats. ioSENTRIX offers comprehensive AppSec and DevSecOps services to businesses. Through our innovative visual mind maps, we comprehensively explain what these concepts mean and the best practices for implementation. Our comprehensive guide also includes relevant guidance for businesses to build secure applications. Furthermore, we understand that implementing AppSec and DevSecOps can be daunting.
Hence, we’ve made sure to provide detailed advice on how to overcome this obstacle. Whether you’re just starting or have advanced security requirements, our team is ready to help you reach your cyber protection goals safely and effectively. So don’t wait any longer; contact ioSENTRIX for the security consultancy you need today!