
In the year 2022, more than 52 million people experienced the compromise of their private health information across over 700 data breaches. This represents a notable increase from around 6 million affected individuals in 2010, the period during which the systematic documentation of such data started (Report by Healthcare Dive).
There are actions you can take to prevent adding to data breach numbers. Doing a HIPAA risk assessment is an important step to become HIPAA compliant and enhance the security of your sensitive data.
In this blog post, we have explained the contents of a risk assessment and learned how to carry one out.
“HIPAA risk assessments help organizations identify vulnerabilities in how they handle and protect PHI, allowing them to implement necessary controls to prevent security breaches.”
This assessment serves as an internal audit to evaluate how PHI is stored and protected, helps businesses spot vulnerabilities, and enhances information security practices.
The HIPAA Security Rule mandates that both covered entities and business associates must perform risk assessments to safeguard [protected health information (PHI)](.
Numerous patients store their health information digitally. This contributes to a greater risk of potential breaches in their electronic protected health data, commonly known as ePHI.
Therefore, regular evaluation is necessary to identify vulnerabilities and an effective strategy must be defined for the safety of patient information. One effective method to achieve this is through a risk assessment, that must be compliant with HIPAA regulations.
Failing to comply with HIPAA rules can lead to expensive fines, harm to your reputation, and sometimes even criminal charges.
The objective is defined in the General Rules (CFR 45 § 164.306) before the Administrative, Physical, and Technical Safeguards of the Security Rule. The objectives are:
In terms of the Administrative, Physical, and Technical Safeguards of the Security Rule, the General Rules permit a flexible approach in implementing the standards. While flexibility is allowed, it is important to comply with all standards, unless a specific specification is considered unreasonable or inappropriate, in which case an equivalent alternative measure should be put in place instead.
This assessment must consider certain factors to determine the likelihood of compromise such as:
The reason the HIPAA breach risk assessment is considered optional is that covered entities and business associates have the choice to forgo this assessment and report any unauthorized access or disclosure of PHI instead.
However, this may lead to disruptions in business operations if the HHS Office for Civil Rights deems that your organization is facing a high number of data breaches and decides to carry out a compliance review.
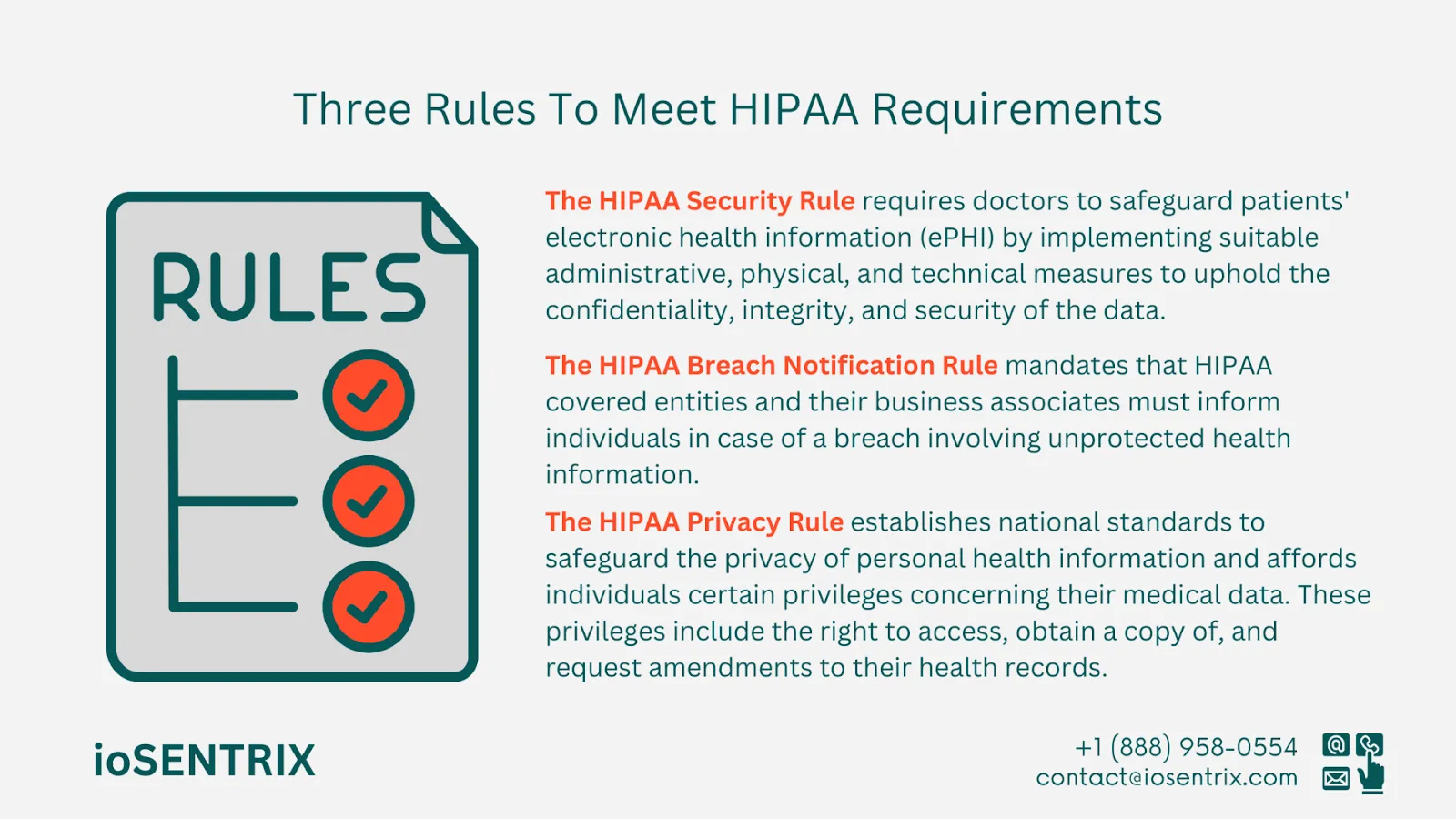
Rules to Meet HIPAA Requirements
Frequent breach notifications can erode trust among patients, clients, and business partners. This is especially true when individuals are told to protect themselves from fraud, theft, and other risks due to breaches that may not have occurred.
The HIPAA Security Rule requires covered entities and business associates to perform risk assessments. However, many tend to neglect the importance of HIPAA privacy risk assessment. This type of assessment is just as crucial as a security risk assessment but can be more challenging, especially for larger organizations with different types of operations.
To conduct a HIPAA privacy risk assessment, an organization should designate a Privacy Officer. The Privacy Officer’s initial responsibility is to understand the organization’s workflows and how the HIPAA Privacy Rule affects its operations. Next, the Privacy Officer must track the flow of Protected Health Information (PHI) within and outside the organization to pinpoint areas where breaches could happen through a gap analysis.
Finally, organizations and businesses need to develop and implement a HIPAA Privacy compliance program. This program needs rules to deal with any privacy risks to PHI found in the assessment. It should also be checked regularly whenever new work methods or technology is introduced.
According to 45 CFR § 164.530, employees need to receive training on policies and procedures resulting from a HIPAA privacy risk assessment. This training should also be provided when changes to policies and procedures affect employees’ roles. While some organizations may view this training as a checkbox task, properly trained staff are less likely to make mistakes related to HIPAA compliance. Therefore, training on HIPAA policies and procedures should be seen as a strategy to reduce risks.
According to the guidelines set forth by the Department of Health and Human Services (HHS), a security risk assessment includes evaluating risks and vulnerabilities related to the confidentiality, availability, and integrity of electronic Protected Health Information (ePHI) that an organization generates, receives, stores, and transmits.
This involves securing ePHI on various electronic devices such as hard drives, CDs, DVDs, smart cards, personal digital assistants, and portable storage devices.
The term “electronic media” covers a wide range of devices such as a single computer or complex networks spanning multiple sites. An assessment of security risks should consider all electronic Protected Health Information (ePHI), regardless of how it was generated, received, stored, or sent, and irrespective of its origin or where it is located.
It is worth mentioning that conducting a HIPAA risk analysis does not have a single correct method. HIPAA does not offer precise guidelines for performing a risk assessment due to the unique nature of each organization. Nevertheless, there are key factors that should be taken into account during every risk assessment process.
Your risk assessment should consider all possible risks to protected health information (PHI), including where PHI is stored (electronically or physically) and the devices used to store electronic PHI (ePHI).
The Department of Health and Human Services (HHS) offers a set of questions to consider when scoping a project:
Organizations need to recognize and record any weaknesses that might lead to a PHI breach. They can be achieved by regular evaluation of previous or ongoing projects, discussion with the personnel who deal with PHI, and relevant document reviews.
It is important to evaluate the existing security measures against the security requirements set in the HIPAA Security Rule. If any shortcomings or ineffective measures are identified, they should be reviewed again.
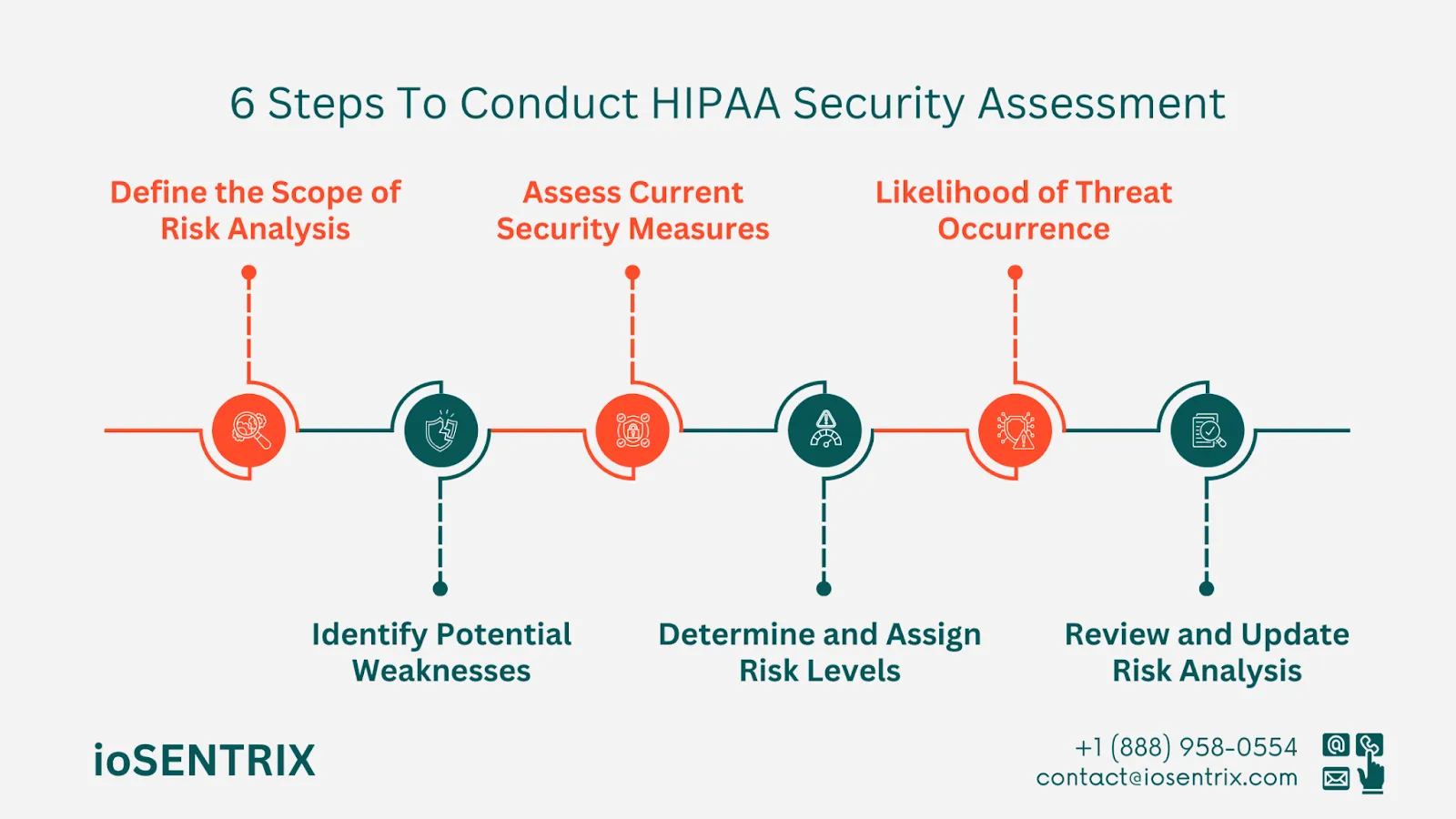
To evaluate both likelihood and impact, organizations often employ a rating scale ranging from 1 to 5. A rating of 1 signifies low likelihood and minimal impact, while a rating of 5 denotes high likelihood and severe impact.
Once the likelihood of a threat is analyzed, companies must analyze the potential impact that these threats could have on the confidentiality, integrity, and availability of electronic Protected Health Information (ePHI). This involves analyzing how serious the impact would be if a threat were to exploit a vulnerability. It is important to document this assessment process.
HIPAA does not specify how often a risk assessment should be conducted, but it is recommended by experts to perform assessments either once a year or once every two years.
Working with cybersecurity experts like ioSENTRIX simplifies the process of understanding the PHI you manage and its flow within your organization. We assist you in assessment of your security measures and pinpoint any vulnerabilities to give you a comprehensive view of your security status.
To learn more about how ioSENTRIX can help you achieve HIPAA compliance, contact us here.