
In December 2022, OU Health, a hospital in Oklahoma, informed approximately 3000 patients regarding a security breach of their health information resulting from the theft of an employee's laptop. This breach exposed sensitive data such as treatments received, social security numbers, and insurance information.
This event emphasizes the significance of having various security measures such as encryption, asset tracking, and multi-factor authentication in place.
This blog explains the various types of security controls, along with examples, you should implement to strengthen your security architecture.
Security controls are safeguards that help to protect information systems, networks, and data assets from security risks. They come in different types like preventive, detective, deterrent, and corrective measures.
Cybersecurity controls are implemented to ensure that sensitive data remains secure, available, and confidential. They involve using various tools, strategies, policies, and processes along with the efforts of individuals within the organization.
Just as we keep our money in a bank for security and easy access, businesses store their important assets in the cloud. Like how robbers target banks for valuable items, cybercriminals go after cloud services to compromise important business data.
Security breaches in cloud computing can have significant consequences for various business goals. In this regard, it is crucial to maintain an advanced security posture to protect against potential attacks.
Many small businesses do not focus on security until they experience a security incident. Research by IBM security revealed that 83% of organizations suffered more than one breach, and 60% transferred the recovery costs to their customers.
Recovering from an attack can be costly, time-consuming, and disruptive for a business. Security controls can enhance your security level and make your business more resilient to risks.
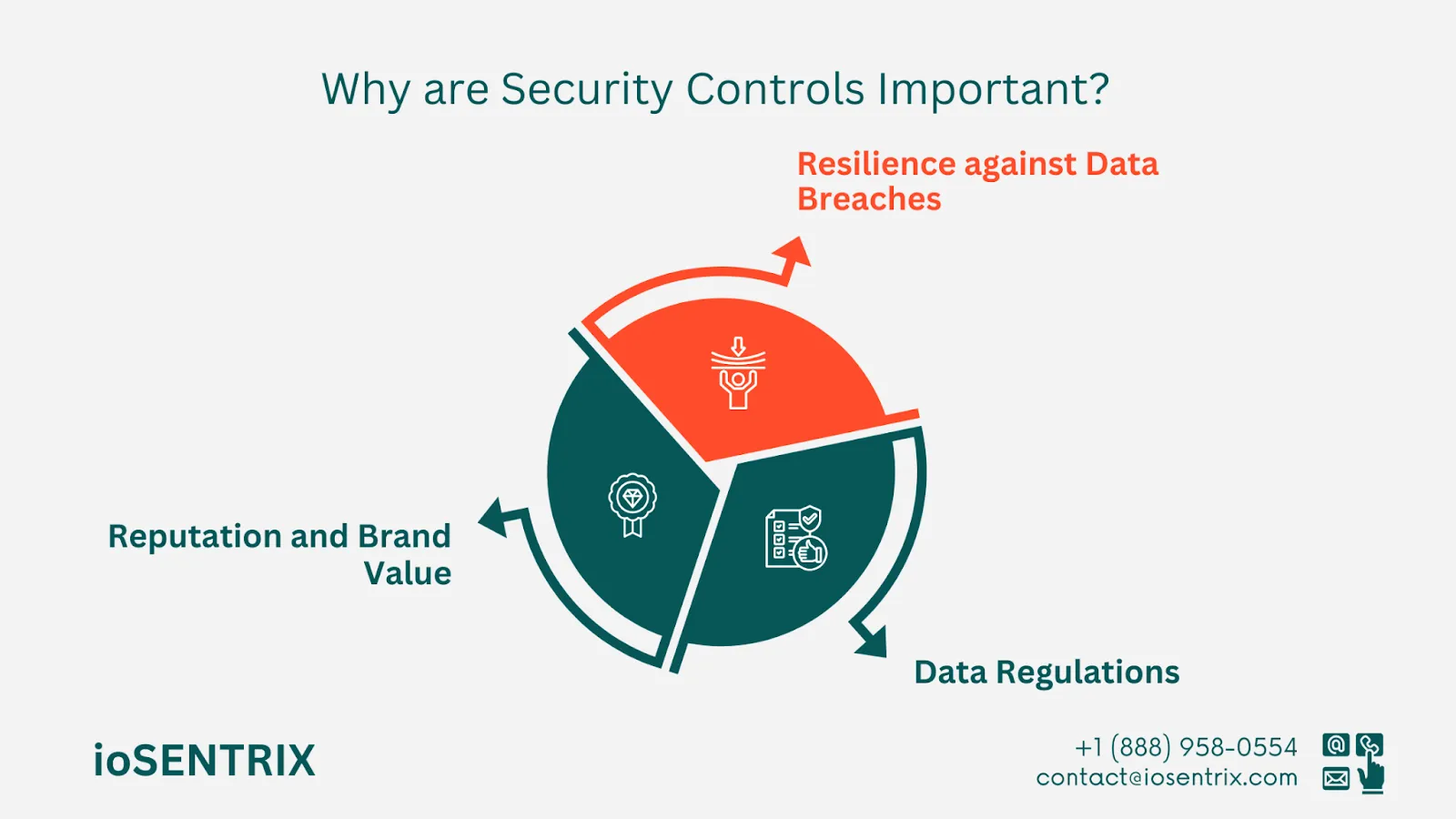
Privacy laws and individual rights regulations are becoming stricter. Companies must follow these rules to prevent legal issues and fines. For instance, if you own a healthcare business in the U.S. dealing with protected health information (PHI), you must comply with the Health Insurance Portability and Accountability Act (HIPAA).
Businesses that handle cardholder data, such as Debit or Credit card transactions, must follow the rules of the Payment Card Industry Data Security Standard (PCI DSS) for security.
It's essential to keep your product safe so customers feel good about using it. Nowadays, People want to know that their info is being kept safe online. If you don't have good security measures, it can cause big problems, just like what happened to Facebook when they didn't handle people's info right.
An increasing number of online users are switching from Google to other search engines because of concerns over Google's data collection practices. In addition, SaaS companies are facing challenges in closing sales deals as they are required to show their security practices through audit reports for frameworks like SOC 2 or ISO 27001.
Security controls are categorised into three main types: administrative, technical, and physical. These different security measures work in harmony to create strong cybersecurity programs.
Let's explore the unique characteristics and purposes of each type of security control.
Physical controls are measures, policies, and procedures to safeguard an organization's physical assets in specific locations. Security threats may include unauthorized access, theft, or natural disasters that can potentially harm these assets.
Examples of physical security controls are:
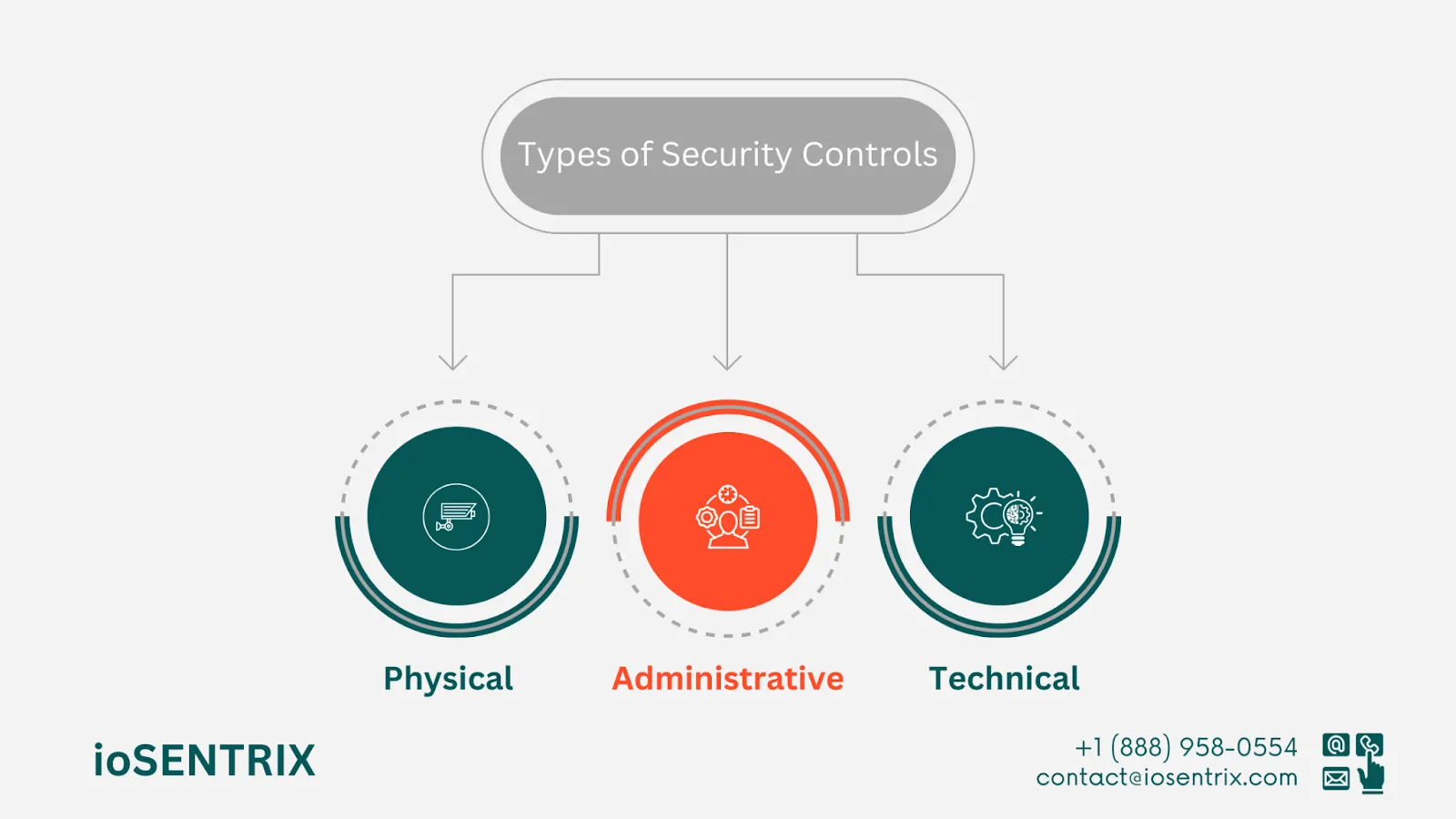
Technical controls are software tools that safeguard your IT infrastructure and information assets against unauthorized access by users. The elements in place help identify, track, stop, reduce, and address different risks or weaknesses from both inside and outside sources.
A few commonly used technical controls are:
Administrative security controls, also referred to as organizational or management controls involve a series of security measures that include policies, strategies, processes, practices, or guidelines aligned with business goals to uphold security standards according to the risk level.
Common examples include:
For advanced understanding of security controls and their implementation, read our blog: What are Security Controls? And How to Implement it?
Now that you have a basic understanding of the different types of control, let's explore the importance of each in securing business environments. Controls can have roles such as prevention, detection, or correction, and there can be some overlap in how they function in practice.
In alignment with its name, preventive controls are in place to find and stop any vulnerabilities, unauthorized access, or threats to important information before they can cause harm. It is crucial to prioritize prevention over dealing with consequences after an incident, which makes these controls the first layer of defense in security.
Some examples of preventive controls include:
Detective controls, similar to whistleblowers, send alerts to alert system administrators or control owners of breach attempts or intrusions. With this information, your IT team can take action to prevent and stop the intruder before any harm is done. Both security service providers and organizations use detective controls for this purpose.
Some examples are provided below.
While a strong security system is important, it cannot provide complete protection against breaches and vulnerabilities. Corrective controls are implemented to handle unforeseen situations, reduce any potential harm to the business, and help maintain operations without disruption.
Common examples are:
Are you feeling overwhelmed by managing and tracking numerous controls? ioSENTRIX offers a solution by consolidating tools, systems, people, and processes into one platform. This simplifies security compliance through automation, ensuring authorized access only through role-based control. It also alerts users of unusual or non-compliant behavior and uses advanced techniques to suggest corrective measures.
Contact us now and let our professionals strengthen your digital defense line.