
Businesses handling payment card data must comply with the PCI DSS. This compliance keeps sensitive information protected. SDLC can help organizations meet PCI DSS standards effectively. How?
This blog explains how you can implement SDLC practices in your computer systems to meet PCI DSS compliance.
The PCI DSS applies to any business that stores, processes or sends credit card information. These standards help ensure that consistent and adequate security measures are in place. Web companies need to meet PCI DSS requirements, which include using a hosting service that complies with PCI standards.
PCI compliance minimizes the risks of attacks through a secure Card Data Environment (CDE). This requirement is essential for in-house payment processing systems and third-party secure payment providers.
It is particularly crucial for e-commerce websites that transmit payment card information over the Internet.
Specific risks associated with e-commerce websites include:
The Software Development Lifecycle (SDLC) is a structured process to create top-notch software quickly and affordably. Secure SDLC (SSDLC) adds security at every step and continues through design, development, testing, deployment, and maintenance. Security becomes an integral part of every phase, not just an afterthought.
PCI DSS are security standards for protecting payment card data. Organizations that process, store, or transmit cardholder information must comply with these standards. The standard comprises 12 requirements: encryption, secure authentication, vulnerability management, and regular monitoring.
Secure SDLC helps organizations meet these requirements by building security into their systems from the ground up.
PCI DSS 4.0 states that security is key throughout the software development lifecycle. The Secure SDLC method involves thinking about security in every development stage, which helps find and fix weaknesses early on.
To learn in detail about PCI DSS Requirements, click here.
Identification and documentation of security needs are essential in the initial phase of SDLC. Requirement 1 of PCI DSS mandates the use of secure configurations. Secure configurations involve security measures taken during the building and installation of computers and network devices to minimize cyber vulnerabilities, such as turning off unused ports or enforcing secure password policies.
Criminal hackers commonly target security misconfigurations for exploitation.
During requirements gathering, teams should identify how sensitive data will be stored, transmitted, and accessed. Define encryption methods (Requirement 3) and specify authentication controls (Requirement 8).
Implementation Tip: Involve security experts early. Threat modeling identifies potential risks and includes mitigation strategies in the documentation.
Requirement 6 of PCI DSS calls for developing and maintaining secure systems and applications through secure coding practices and regular patching. Architects should prioritize segregating duties, least privilege access, and data flow security during this phase.
Implementation Tip: Incorporate security frameworks like OWASP ASVS and design systems that encrypt data at rest and in transit and meet PCI DSS encryption standards.
Developers must write secure code to prevent vulnerabilities like SQL injection and cross-site scripting (XSS). Requirement 6.5 specifies coding guidelines to mitigate common vulnerabilities. Use secure libraries, avoid hardcoded credentials, and validate all inputs.
Implementation Tip: Train developers in secure coding practices and use static application security testing (SAST) tools to identify issues during coding.
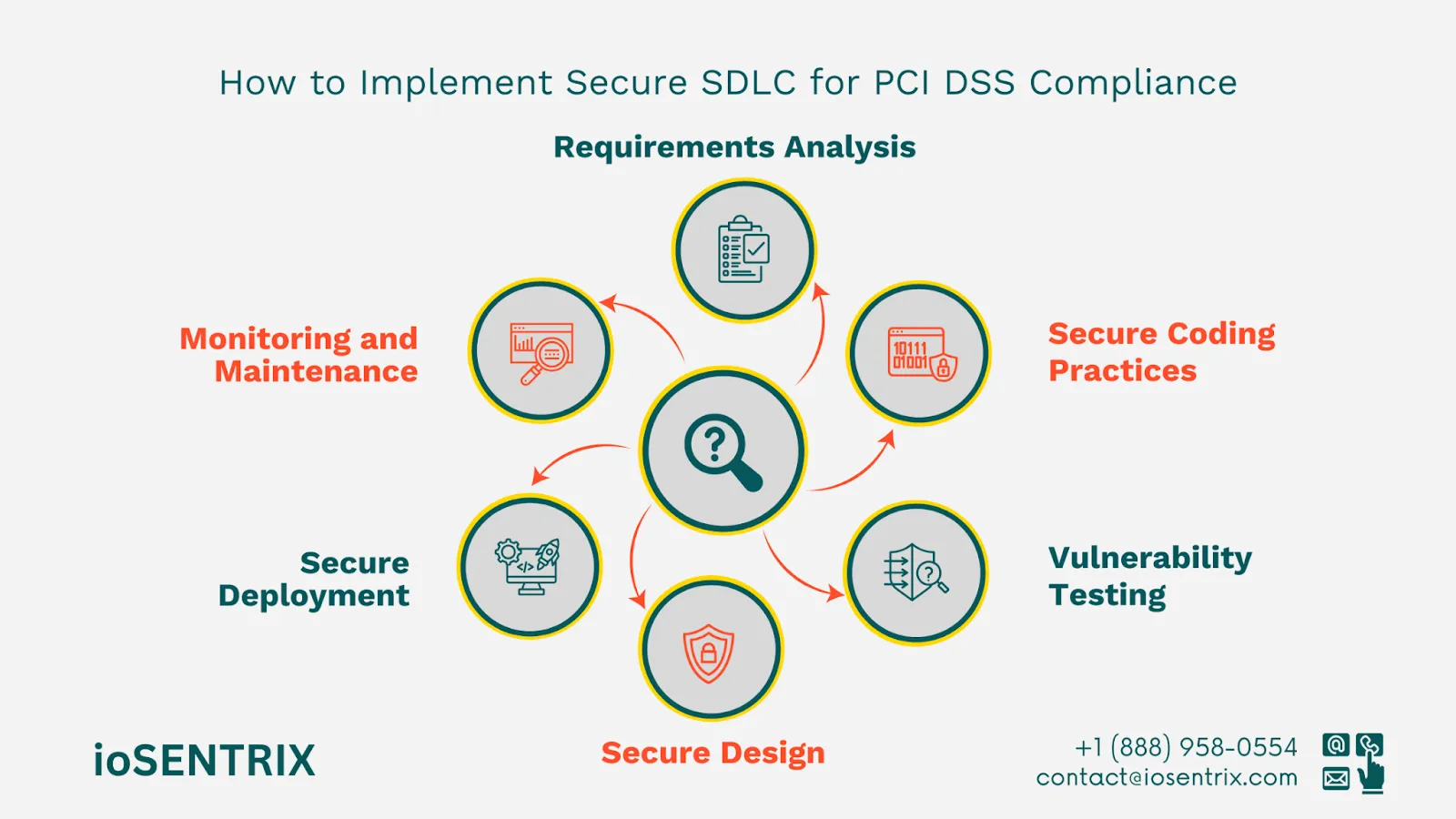
DAST meets the 6th PCI DSS requirement, which involves creating and keeping secure applications. In PCI language, this refers to having a Vulnerability Management Program. PCI describes vulnerability management as the ongoing process of identifying weaknesses in a company's payment card system.
Regarding DAST, PCI DSS Requirements 6.1 and 6.3 require integrating information security into the Software Development Life Cycle (SDLC).
Implementation Tip: Use tools like DAST (Dynamic Application Security Testing) to identify runtime vulnerabilities. Conduct manual code reviews for critical sections of the application.
Must Read: SAST vs DAST: What's the Difference?
Requirement 2 emphasizes the secure configuration of all components. Ensure operating systems, web servers, and databases are patched and configured securely.
Implementation Tip: Automate deployment with Infrastructure as Code (IaC). Validate configurations using tools like CIS Benchmarks.
Requirements 10 and 11 demand logging and monitoring of all cardholder data access. Security measures should be regularly tested, and systems should be updated to address emerging threats.
Implementation Tip: Implement a centralized logging solution to analyze logs for anomalies. Schedule routine security reviews and patch management.
To follow PCI DSS rules, use strong security to protect payment card information. This prevents hacks and keeps all data safe. It also improves security against new threats and saves money. Customers feel secure sharing card details.
PCI DSS guidelines help find and fix payment card system issues quickly. It lowers the risk of security problems, money loss, and harm to the company's reputation.
Do you trust a business after a data breach? A survey found that most US adults wouldn't return to the same company. Customers value PCI compliance and certification for trust. It's vital for customer loyalty and impacts profits.
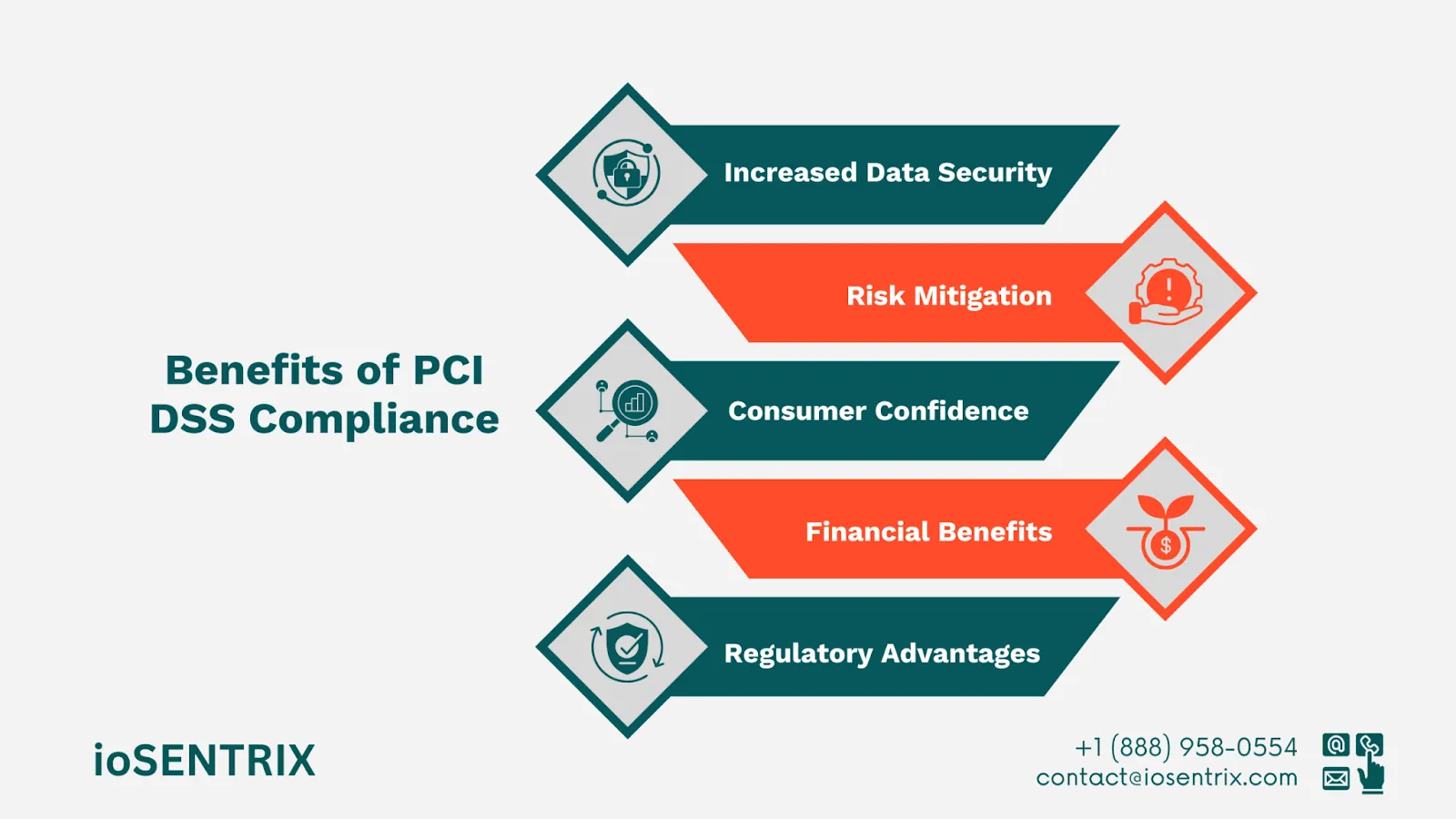
PCI DSS requirements may cost upfront, but the benefits are worth it. Organizations save money by avoiding data breaches, fines, and backlash. They can also lower insurance premiums, which leads to more savings overall.
Data protection laws are strict worldwide. Following these laws and being PCI DSS compliant helps companies stay ahead of regulations, which builds credibility with regulators and consumers.
Failure to adhere to PCI standards may lead to significant penalties and adverse outcomes, such as business loss. Research by the Ponemon Institute revealed that over half of customers lose confidence in a company following a data breach, with 31% deciding to end their association with the company post-breach.