
Penetration Testing as a Service (PTaaS) is an external service that regularly assesses and enhances an organization’s cybersecurity by simulating attacks. It enables organizations to understand how attackers view their security and how well their current security measures would perform in an actual attack.
Unlike traditional penetration testing, PTaaS allows for on-demand testing, which integrates testing into daily security tasks and supports immediate responses. This service provides expert testers who continuously examine systems.
These testers turn security assessments into a regular practice instead of just quarterly or annual events. With PTaaS, organizations gain better insight into their security preparedness by using dynamic reporting tools to track threats and improve defenses over time.
Penetration testing has become the best method to find hidden weaknesses, spot complex attacks, and verify security measures. Here’s why penetration testing will be essential in 2025 and in the future.
The growth of PTaaS reflects the increasing cyber threats and the demand for more advanced and ongoing security testing. The cybersecurity market had a value of $156.5 billion in 2020. It is estimated to grow to $352.25 billion by 2026, showing a yearly growth rate of 14.5%.
In this expanding market, PTaaS is establishing a strong presence due to its ability to provide real-time insights and flexible testing solutions.
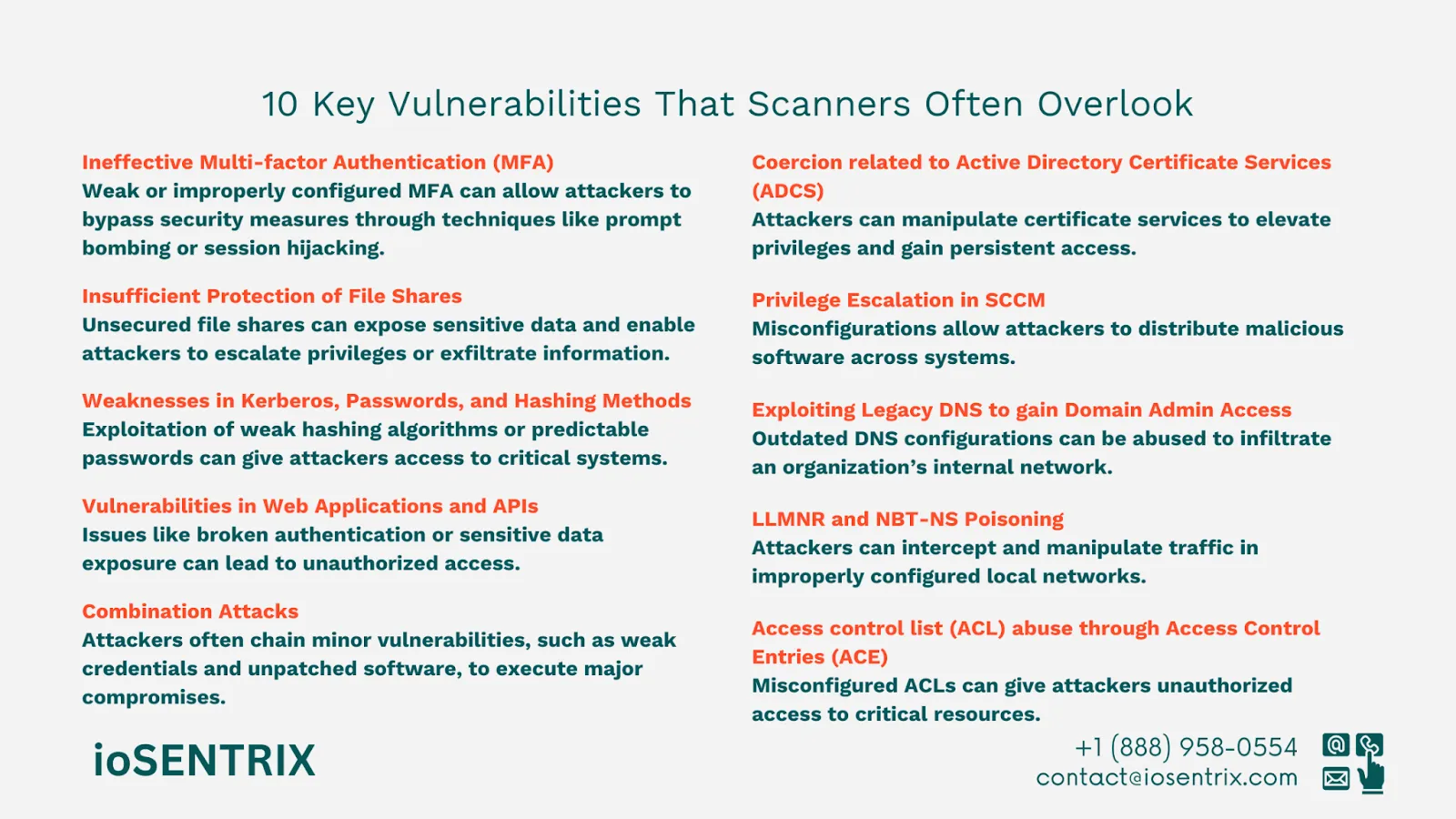
Vulnerability scanning is a crucial component, but it can sometimes create a misleading sense of security. While modern scanners are good at finding obvious issues like outdated software or missing updates, they often struggle to identify more complex attack methods.
For example, over ten privilege escalation attacks aimed at Active Directory Certificate Services usually go unnoticed by most scanners, yet they present serious threats to organizations.
Scanners often overlook how small vulnerabilities can be combined to create a serious attack. A skilled attacker can use these connections to break into even the most secure environments.
For instance, a weak password combined with inadequate authentication measures could serve as an entry point for a complex attack that compromises sensitive systems.
You may enjoy: Vulnerability Assessment vs Penetration Testing.
Even with many years of security training and awareness efforts, weak passwords and user habits remain a major weakness in cybersecurity. Both administrators and users often choose simple passwords that are easy to guess, which puts organizations at risk for attacks such as password stuffing and password spraying.
Penetration testing not only identifies poor password practices but also assesses how well multi-factor authentication (MFA) is working. Although many organizations have added MFA for systems such as Microsoft 365 and remote access, it’s common to find cases where MFA is missing or not properly set up.
For instance, a pentester might take advantage of a weak password to gain access to a VPN and then use a technique known as “prompt bombing” to bypass MFA. This method involves bombarding the user with approval requests until one is accepted. This scenario illustrates how weak passwords, flawed MFA setups, and user behavior can be combined to compromise systems.
Many companies invest heavily in security tools and systems to protect their data, but without regular testing, it’s difficult to know if these measures work as intended. Penetration testing not only spots vulnerabilities but also assesses how well your defenses hold up against real-world attack scenarios.
At ioSENTRIX, our services enhance traditional penetration testing by offering a cooperative approach to testing and improving security. During pentesting sessions, our team mimics real attacks to show how these attacks interact with your security systems.
These sessions provide valuable insights, reveal misconfigurations, and identify coverage gaps to help your team strengthen defenses in the moment.
Rather than depending on occasional tests that only reflect your security status at one moment, Pentesting as a Service (PTaaS) offers continuous testing to help you stay aware of vulnerabilities as they emerge.
Factors like shadow IT, software updates, tight deadlines for complex projects, and human mistakes can heighten your risk at any time. Our strategy ensures that potential threats to your business are identified and addressed before they can be taken advantage of.
PTaaS platforms provide real-time dashboards, alerts, and keep you updated on your organization's security status at all times. Risks are identified immediately when they arise.
PTaaS is flexible and suitable for businesses of any size. You can easily change the testing scope to cover a wide range or focus on a specific area during transitions without the high costs and limitations of traditional penetration testing.
Monthly PTaaS costs about 25% less than monthly one-off penetration tests, and you can save even more by identifying vulnerabilities faster, which lowers the chances of cybersecurity incidents.
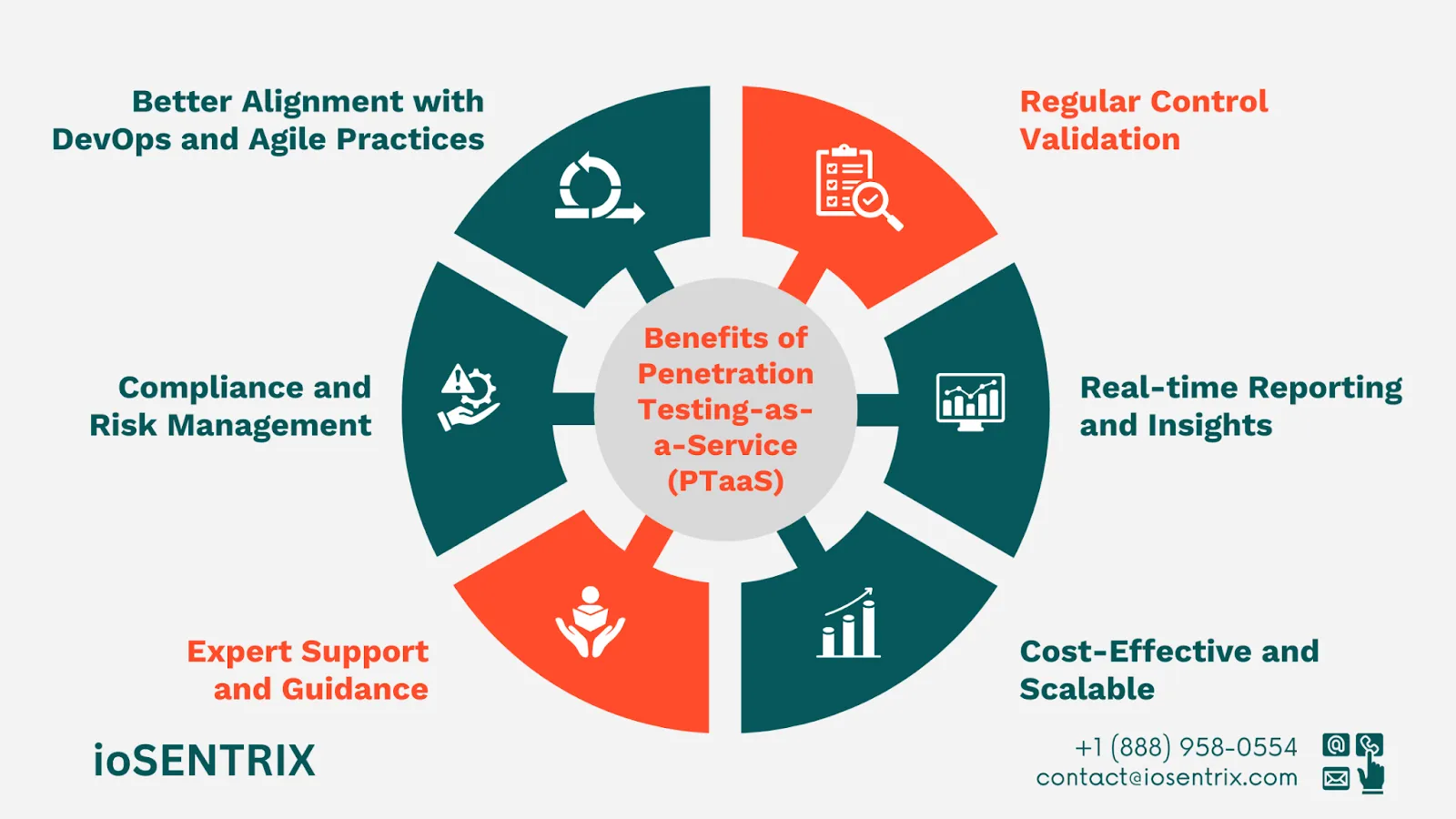
With ioSENTRIX’s PTaaS, you get access to professionals who frequently conduct penetration tests for large organizations. They review and confirm all findings and share them with you every quarter. These experts assist you in understanding the results and provide customized advice to enhance your security measures.
Many industries need regular security assessments to comply with standards like SOC 2, HIPAA, and PCI-DSS. PTaaS supports your organization in maintaining compliance by providing consistent testing and reports. It helps lower the risk of penalties for non-compliance.
If your team makes frequent updates and adds new features, conducting penetration tests just once a year will not be sufficient to find new vulnerabilities. You will need to regularly check new or modified services to keep up with a changing environment.
The use of AI and machine learning is a significant trend shaping the future of PTaaS. This integration enables automated vulnerability assessments that are quicker and more precise compared to conventional approaches.
AI-based testing is expected to keep advancing, with the ability to predict future vulnerabilities by past data analysis and patterns recognition.
Adding PTaaS to Continuous Integration (CI) and Continuous Deployment (CD) pipelines is becoming more common. This practice helps reduce the risk of vulnerabilities in production by allowing developers to find and fix security problems in real time.
Many governments are tightening cybersecurity laws, leading PTaaS providers to increase their compliance testing efforts. This trend helps organizations find and address vulnerabilities while ensuring they meet industry regulations.
In the future, PTaaS will feature detailed compliance modules specifically designed to align with the latest standards and requirements.
To address diverse cyber threats, PTaaS will focus more on customized and specialized testing. This approach recognizes that a “one-size-fits-all” is not effective in dealing with the unique and complex cybersecurity threats of today.
PTaaS services will meet the specific needs of industries such as healthcare, finance, and emerging technologies like IoT devices and blockchain.
As we approach 2025, the importance of cybersecurity is greater than ever. Relying only on vulnerability scanners or assuming existing controls are enough is no longer adequate. PTaaS offers a detailed assessment of your security status, highlights critical weaknesses, and ensures your defenses are effective against real-world threats.
This approach will not only help protect your organization from emerging threats but also show your commitment to proactive security measures. Contact ioSENTRIX today to schedule your next penetration test, and take the first step toward creating an advanced defense system.
Penetration Testing as a Service, or PTaaS, is a cloud-based service that provides ongoing penetration testing. This helps businesses to identify and address security issues in real time.
The length of a penetration test using PTaaS varies based on the scope of the assessment. Automated scans can typically be finished in a few hours, while more detailed manual testing may take several days or even weeks. With continuous testing, businesses can have ongoing evaluations and receive real-time results.
PTaaS improves operational efficiency by providing testing services as needed, automated vulnerability scanning, and real-time report generation. This allows for more frequent checks for threats and enables organizations to address identified risks promptly.
Organizations should plan to conduct security testing at least once a year. They should also carry out additional assessments after significant changes to infrastructure, before launching new products, or during mergers and acquisitions.
Larger organizations that handle a large amount of personal or financial information, or that have strict compliance requirements, may need to perform penetration tests more often.