
Is it necessary to conduct penetration testing for SOC 2 compliance? What are the requirements for a pen test in SOC 2? This article examines all the requirements for SOC 2 compliance. SOC 2 (Service Organization Control 2) is a common compliance standard created by the American Institute of Certified Public Accountants (AICPA).
It protects confidential information and upholds customer confidence, essential in the modern interconnected environment.
Many businesses frequently ask whether SOC 2 is mandatory for penetration testing or not. This article addresses this inquiry by examining the components of SOC 2, and the significance of penetration testing within this regulatory framework.
Developed by the American Institute of CPAs (AICPA), SOC 2 sets standards for handling customer data, with a focus on these five key principles: security, availability, processing integrity, confidentiality, and privacy.
Contrary to PCI DSS, which has strict rules, SOC 2 reports are customized for each company. Based on their individual business needs, companies create their controls to meet one or more trust principles.
The internal reports offer valuable information about how your service provider handles data. This information is useful for you, as well as regulators, business partners, and suppliers.
Penetration testing is not explicitly required by SOC 2. Instead, SOC 2 allows organizations to choose the controls that best fit their security needs. The framework is flexible and enables organizations to select the security measures that best suit their requirements amongst various ongoing and specialized evaluations.
While SOC 2 offers flexibility, it may cause confusion regarding which security measures, like penetration testing, are essential versus optional. While such a test can help find vulnerabilities and improve security, it's not mandatory for SOC 2 compliance. ioSENTRIX suggests considering it as a valuable practice, even if not officially required.
As mentioned earlier, adherence to SOC 2's Trust Services Criteria (TSC) is essential to ensure data security and management. It is important to understand the specific requirements to meet compliance. Let's examine the five main principles in detail.
The fundamental principle of safeguarding information and systems from unauthorized access is crucial for security. This involves using measures like firewalls, access controls, and encryption to protect data from internal and external threats.
This standard focuses on making sure that systems, products, or information are easily accessible as guaranteed. It includes actions such as monitoring network performance, planning for disasters, and managing incidents to ensure that services are ready for use.
Common areas of focus include monitoring network performance, conducting data backup and recovery processes, and establishing disaster recovery procedures.
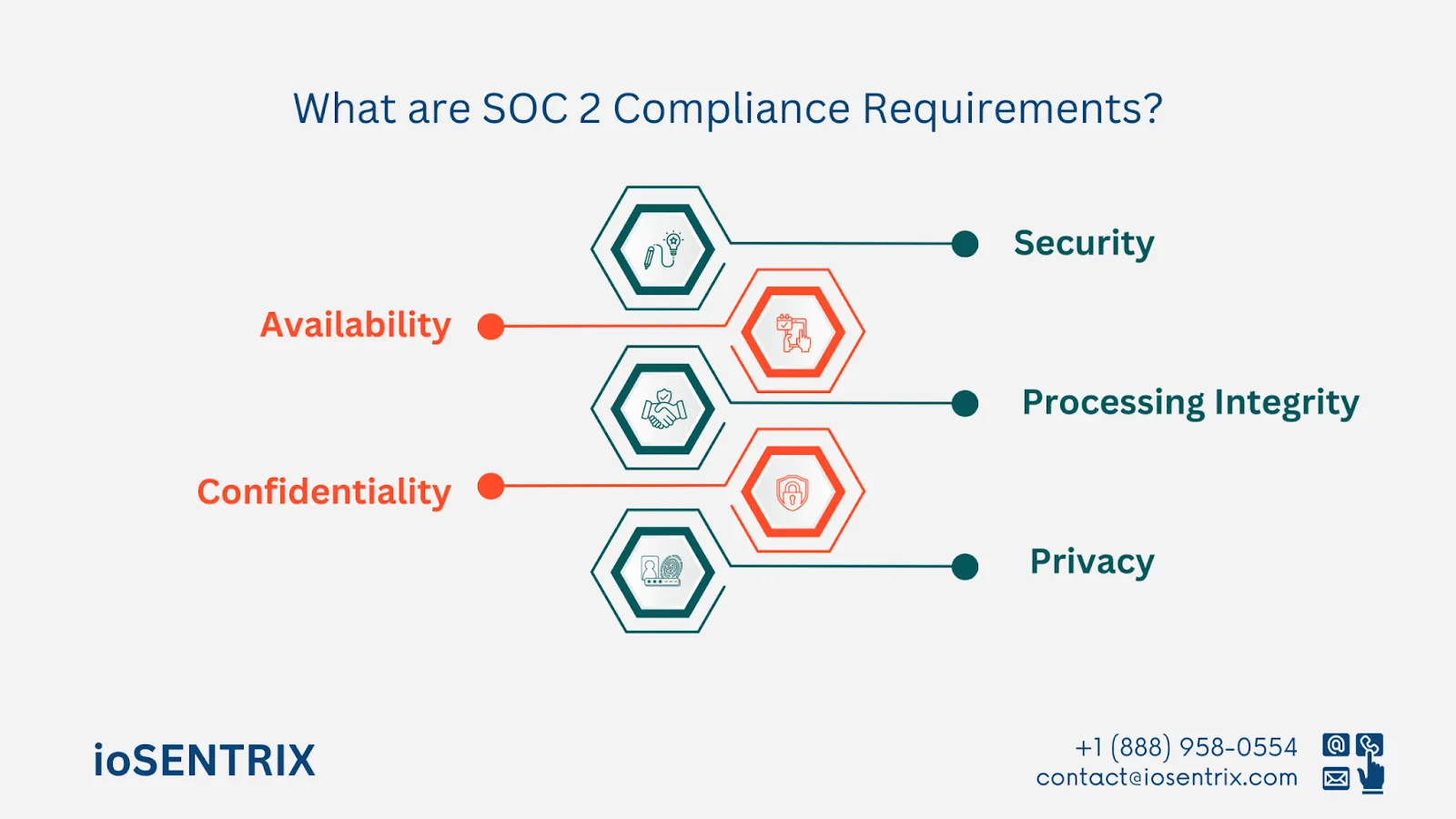
The main focus is on making sure that system processing is accurate and reliable. This ensures that information is processed in an approved, complete, accurate, and timely manner. Controls like data validation checks and quality assurance processes are put in place to maintain accuracy.
Restricted access to the information is essential to protect sensitive data such as customer information. This is achieved by using encryption, access controls, and network segmentation to limit access and disclosure to specific parties or functions.
This aspect focuses on how personal information is gathered, used, stored, and removed according to an organization's privacy policy and relevant laws. It includes measures such as consent procedures, data protection, and privacy evaluations.
There are two main options to choose from: SOC 2 Type 1 and SOC 2 Type 2. Each report serves a specific purpose and offers unique value. It is important to determine which attestation report best suits your needs before initiating the audit process.
SOC 2 Type 1 compliance assesses an organization's cybersecurity measures at a specific moment. Its purpose is to check if the internal controls set up to protect customer data are appropriate and operational. This evaluation aims to see if the required Trust Services Criteria are being met. Typically, Type 1 audits and reports can be finished within a few weeks.
A SOC 2 Type II evaluation assesses how effectively a service organization's system and controls operate over a specific timeframe, usually ranging from 3 to 12 months. It aims to determine whether these systems and controls are functioning as planned. While Type 2 audits may require up to a year for completion, they are generally more costly compared to Type 1 audits.
In many cases, the decision comes down to timelines. Consider a scenario where you must demonstrate compliance to secure a crucial business opportunity. However, your company may lack established systems or have recently applied significant changes to your data security protocols.
Instead of waiting for a comprehensive Type 2 report, opting for a Type 1 assessment of your current information security controls can serve as a temporary fix. It is advisable to aim for a SOC 2 Type II report from the start, as many clients are turning down Type 1 SOC reports.
Eventually, you will likely require a Type 2 report, and obtaining it directly can save time and costs by consolidating the audit process. If immediate action is needed, a Type 2 audit report covering a shorter 3-month period can be a practical solution.
It's important to understand the concept of penetration testing in cybersecurity. Penetration testing, while not required, is valuable and aligns with the TSC principles. It addresses vulnerabilities in an organization's security setup, and mimics cyberattacks to assess the strength of security measures in place.
During this process, the tester is given some level of special access to the company's internal network. The main goal is to imitate what someone on the inside, like an employee or outside vendor, could potentially take advantage of. This method is especially helpful in finding weaknesses that could be exploited after an initial breach, like gaining more privileges or stealing data.
External network penetration testing is conducted to assess an organization's ability to defend against outside threats. This examination is done by a third party with no prior access to the internal systems, evaluating the effectiveness of the perimeter security controls.
The main focus is on testing firewalls, publicly accessible applications, and services to ensure the organization's readiness against external attacks.

Hybrid penetration testing combines features from internal and external penetration tests to give a full view of an organization's security status. This method helps to understand how different security measures function in both insider and outsider attacks and identifies possible vulnerabilities within the organization.
As noted earlier, although not explicitly mandated by SOC 2, penetration testing can be a useful method for confirming the strength of a company's security measures, specifically regarding confidentiality in the TSC.
For example, hackers may attempt to crack encrypted data, enter restricted network areas, or get hold of confidential information. Successful defense against these attacks proves the reliability of an organization's confidentiality protections.
Penetration testing also shows how various security measures work together. For instance, if a hacker can't decrypt data but can bypass access controls, the data remains at risk.
One more benefit of pen testing is that it can be customized to imitate the threats that are most important to a company's specific operational situation. This is especially helpful for industries like finance or healthcare, which are often targeted for their valuable confidential information.
Through realistic attack simulations, businesses can improve their understanding of risks and make better decisions when aiming for SOC 2 compliance.
Read more on: Compromise Assessment or Penetration Testing?
When considering SOC 2 compliance, it is important to hire a penetration tester with the right qualifications. The person or team performing the test should possess the necessary credentials to guarantee an accurate and compliant assessment with the established standards.
An important qualification to have is a Certified Ethical Hacker (CEH) certification or a similar qualification. This certification shows that the individual has received in-depth training in ethical hacking methods and is knowledgeable about current cybersecurity risks and defenses.
The tester needs both technical skills and knowledge of regulatory rules. Familiarity with SOC 2 and its TSC is important for ensuring that checks meet compliance goals.
This helps in vulnerability detection and control evaluation based on the necessary criteria.
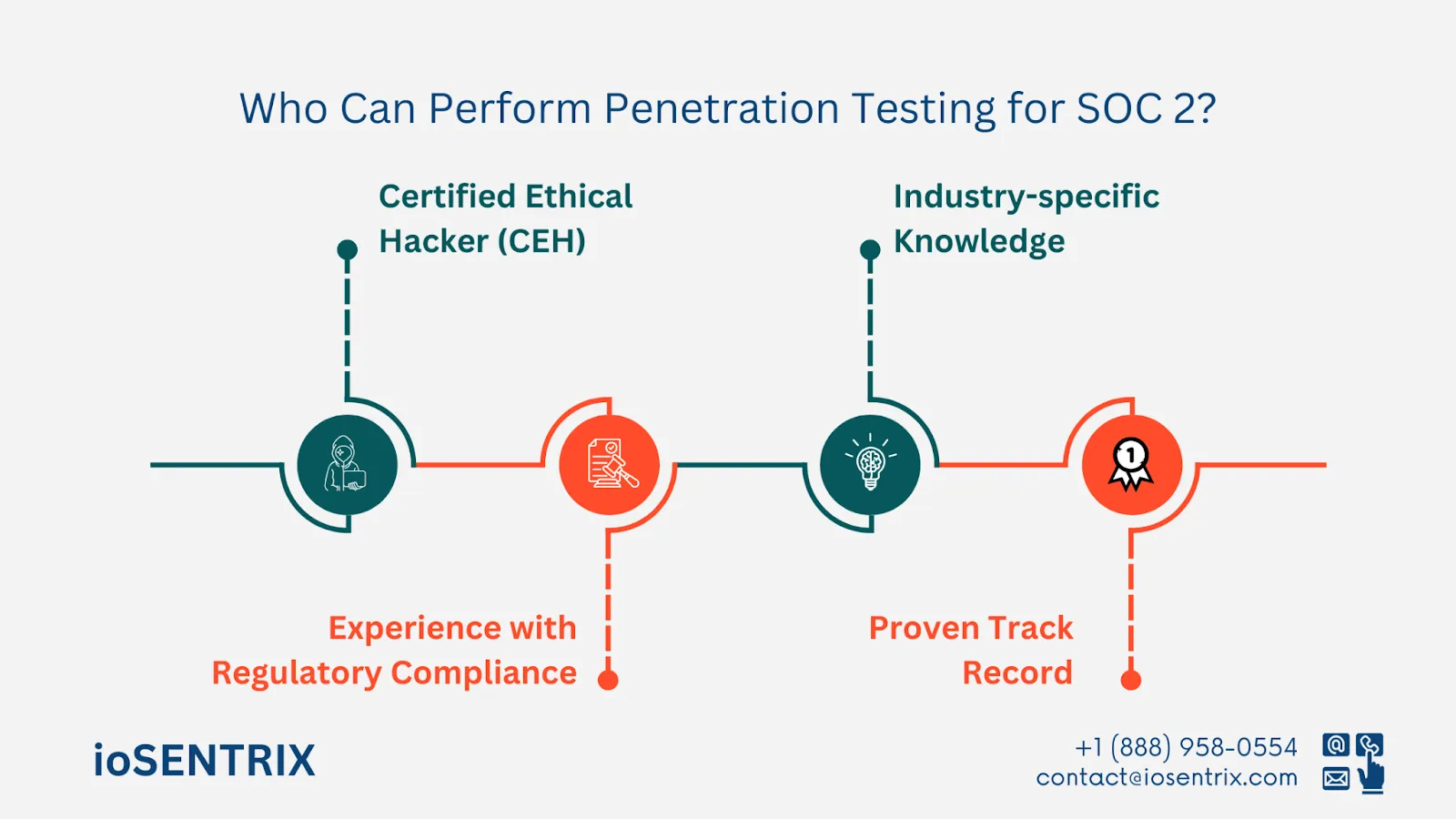
Various industries have specific security needs and risks. An expert familiar with your industry can conduct more focused and meaningful assessments. For instance, healthcare companies need to follow regulations such as HIPAA, and financial institutions may have particular data security demands.
Having an assessor who understands the industry can customize the evaluation to address these distinct requirements, resulting in more practical outcomes.
It is important to choose someone who has a strong record of successful tests, especially within SOC 2 or similar compliance frameworks. Past accomplishments can indicate the examiner's ability to conduct a thorough evaluation effectively. Client feedback, case studies, or references can offer helpful information about the examiner's credibility and skills.
Every category has its pros and cons that can significantly impact the quality of your SOC 2 evaluation.
Software tools are used to conduct scans that detect known vulnerabilities and address various security concerns quickly. These scans are effective in identifying common weaknesses such as outdated software, missing patches, and configuration errors.
However, they have limitations as they can only detect known vulnerabilities and may not identify more intricate security issues that necessitate a deeper understanding of the system's logic and functionality.
Manual security tests are conducted by skilled human testers who imitate real-world cyber attack situations. These testers can think innovatively and adjust their tactics to uncover intricate vulnerabilities that automated tools may overlook.
Manual tests are valuable for evaluating the security controls' efficiency, as they can be customized to match the Technical Security Controls (TSC). Nevertheless, conducting manual tests tends to require more time and financial resources compared to automated methods.
Experts often suggest a balanced approach that incorporates both automated and manual tests. Automated tests efficiently pinpoint and address obvious vulnerabilities-enable manual reviewers to concentrate on more intricate and potentially significant gaps.
Have detailed insights on our Blog: Choosing the Right Pentesting Approach: Automated or Manual?
While not required for SOC 2 compliance, we believe that penetration testing is highly valuable for validating security measures and improving data protection. This practice also aligns with TSC principles and can strengthen your company's cybersecurity strategy. Therefore, it is strongly advised. Many organizations seek assistance from experts like ioSENTRIX to incorporate penetration testing into their SOC 2 compliance process.
Our skilled team will support you in understanding the key aspects that assessors consider in SOC 2 compliance. We will assist you in validating the efficiency of your security measures and ensuring they comply with the TSC to facilitate a seamless audit process.
We not only assess your current compliance status but also assist in creating a plan for the future. Our customized plans will detail the necessary steps to take, such as the importance of penetration testing in confirming your security protocols.
Get in touch today to have a secure digital environment.