
For quite a good time, there has been a lot of buzz around third-party data breaches. 2020 has been a year full of cyber-attacks, and the pandemic has worked as a catalyst in all the data breaches.
According to reports, the cyber-attack has been increased by 400% since February 2020, in which third-party data breach was one caused in the augmentation of data breaches that increased the cost by $207,000
Sometimes the business needs to collaborate or outsource some of the services or products to the third-parties to make their business work efficiently. Nowadays, companies heavily rely on their third-party vendors, suppliers for their day-to-day operations and services to increase their production, sales, distribution.
Such collaboration with third-parties reduces the cost of the services, sometimes gives competitive advantages, and sometimes it is the demand or need of the business for its supply chain. Without any doubt, third-party vendors and suppliers provide a huge benefit to the first-party business.
If your organization relies on the third-parties, or you are going to build a third-party relationship. Then, read this article to know how you can assess your third-parties to maintain and validate the security threats.
But before we go further to assess the third-party ventures, it is essential to know the nature of risks associated with the third-party businesses.
In the security industry, third-party risk analysis is considered one of the essential things to be done while outsourcing any services or products to any third-party business. It is vital to manage third-party risk, which has direct, indirect, remote, or in-person access to your infrastructure, network, system, sensitive or confidential information that may expose your business to external or internal threats.
The following are the categorized risks that you can evaluate yourself with almost every type of third-party business.
Cybercriminals have been very sophisticated in their approaches. Let alone, in January 2021, there already have been several data leaks that happened due to third-party. The relation you build with your third-party vendors, suppliers, contractors, and service providers can impose multiple risks on your organization.
The risk may vary into their severity level but can still affect your organization’s security, reputation, finances, privacy, and, most importantly, your business continuity. Recently, one of the biggest tech firms and monitoring software system providers became the cause of supply chain attacks, and around 18,000 of its high-profile customers had been victimized.
Now the organizations heavily rely on their third parties to perform their daily operations, meet customers’ needs, and many more things to increase business productivity. During this, sometimes they do not consider the fact that the 3P might have access to their data or network.
Let’s consider an example of a SaaS-based CRM used by a company:
Think about it as you are utilizing the CRM (Customer Relationship Management) solution for your company to increase your business efficiency, team interaction, and productivity. One day the CRM company gets breached due to some reason. The hacker gets all of the CRM databases that possess your company’s internal useful information such as customers, employees, contract information, lead resources, purchase records, etc.
In such circumstances, you have to protect your company from threats; because an incident befalling on your 3P can heavily affect your data confidentiality. Depending on your necessities, requirements, and business goals, you can quickly assess your third-party risk with the help of your in-house security team or any independent cybersecurity service providers or individual professionals.
There are a variety of security industry frameworks such as NIST, SANS, ISO, etc., that you can incorporate in your business model to perform a third-party risk assessment.
The standard third-party risk assessment includes the consultation of your third-party business policies, a series of self-assessment questionnaires that you can ask before signing the contract.
Use this link to download this infographic in PDF format.
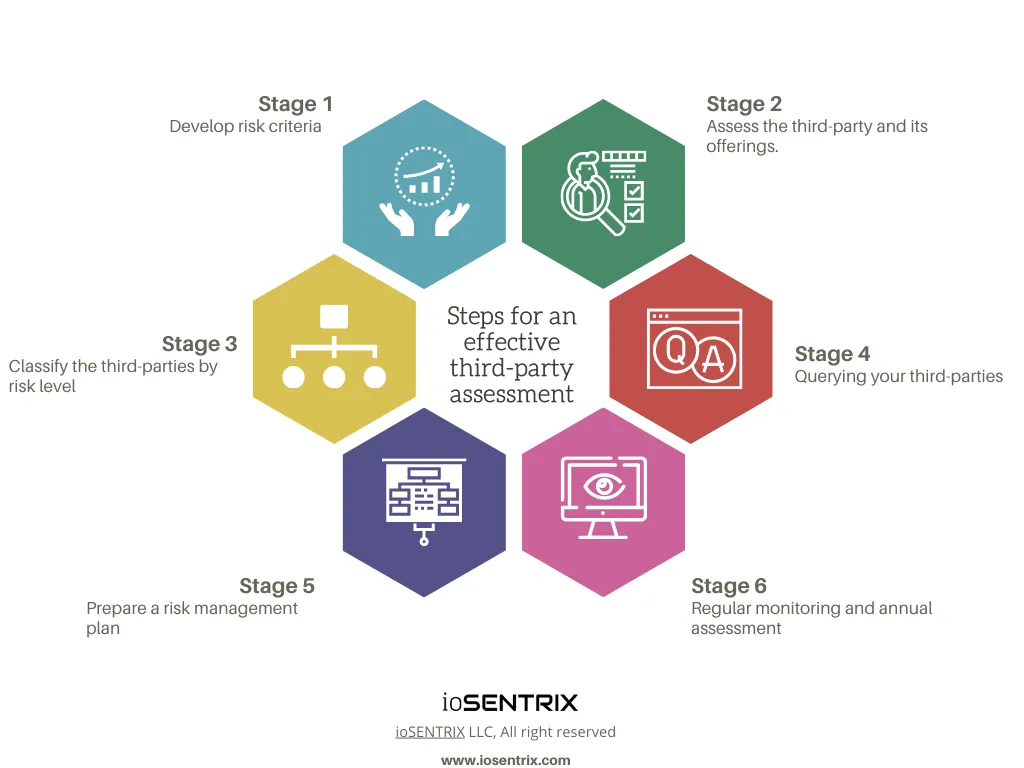
An effective risk assessment process throughout the third-party relationship life cycle includes:
Before you start the assessment, you must define the principle risk criteria you want to evaluate your third-party. It is necessary to develop risk patterns because once you recognize your business’s probable risk exposure to the third-party, you would correctly identify and prioritize your inherent risk. Let’s understand this on a big frame.
You have partnered with a travel agency named XYZ and received some benefits for your company and employees in terms of different packages and discounts. You generally go on business trips, industry seminars, conferences, etc., by utilizing their packages and services. They have sufficient data about your employees, such as their name, contact number, addresses, travel records, etc.
They also know how often your employee visits a specific city, as well as the period they spent on a specific site. Now let’s suppose one fine day the travel agency database gets breached, and the hackers get their hands down to the data of your company available in their database.
In this case, your company will be open to strategic and privacy risks. Because if the information is gathered and analyzed efficiently, it can provide an open path to the hacker to chain up all the travel records. This would expose your employees’ personal identification information and help the hacker track your company’s or employees’ trip activity to uncover your trade secrets and employees’ mission on the specific traveling history.
You can create risk evaluation criteria based on “high,” “medium,” and “low” impact areas on the organization. The impact can vary from reputational, customer trust, business productivity, regulatory affairs, penalties, finances, and much more according to business and third-party type.
In the third-party assessment, you must not assess your service/product provider as a whole. Instead, evaluate them separately on the basis of their company and each of the services/products you are interested in. This will help you get a better picture of the risk’s nature.
For example, if you evaluate your third-party as a company, you’ll likely end up with a clear picture of reputational, financial, compliance, and replacement risk. On the other hand, when you’ll evaluate them for the service and product you intend to buy, you’ll get a broad picture of their access to your physical and digital assets/systems/data as well as their technical competencies.
Right after you assess your third-parties, you must classify them according to their importance to your business, their risk level, the likelihood of threat and attack occurrence, their access to your internal/external network, and sensitive information.
Doing this will help you understand and decide whether you can work with that vendor or not and help you prepare and develop an efficient risk management plan with streamlined processes.
Third-parties risk assessment questionnaires can help you recognize potential security flaws of your partner that could result in a data breach and affect your business. You can use industry-standard best practices, frameworks for your questionnaires and even customized or extract multiple questions according to your business priorities, compliances, and concerns industry requirements from ISO, NIST, SANS, and shared assessments frameworks .
Questionnaires may vary with the type of vendor you reach because not every company has the same goals, nor the same practices apply to every business. But, evaluating them through the questionnaire can help you make a firm decision whether you can afford a relationship with them or not; in addition to assessing your 3Ps, you might ask:
With all the information and risks collected with the questionnaires, you can prepare and strategize a risk management plan. This method will help you respond quickly if you come across any disaster because of your third-party vendor.
This will also help you analyze the vendor security posture and risk level and perform due diligence by reviewing the submitted questionnaires.
For this, your risk management plan must include the possible risk scenario with the response strategy and the responsible teams and employees to reduce the disaster impact and minimize it to the acceptable level so that you can mitigate the risk of the third-party breach. While preparing for the risk management plan, make sure you include all the regulatory compliances and necessities of industry standards your company and the third-party vendor must meet.
Relying on preliminary assessment is not enough; it is crucial to monitor your third-party frequently. Since technology changes, and so does the security standards and practices. Therefore, it might be possible that previous standards and policies wouldn’t align with emerging threats and defense mechanisms.
Depending on the evaluated risk level, assess your third-party quarterly or annual basis because this is the more reliable way to stay ahead from third-party hazards and uncertainties.
Today, companies operate in a continually developing environment; now and then, new technologies and software are introduced to make many processes easier but also increase the level of risk originating from each of them.
No matter if you are a small or mid-size company, you need to maintain your business relationship and security with your vendors and service provider. Do not wait for a breach to occur; instead, take a proactive approach and perform a third-party risk assessment to streamline your business operations with industry best practices and framework.
You can also reach us for help; we provide 3rd party risk assessment as a service, among other necessary security testing to help organizations have a secure online exposure. As a trusted cybersecurity partner, we have helped a lot of startups in their third-party risk assessment.
We can also help you respond to the 3P assessment question by evaluating your company’s current posture and providing recommendations on improvement.
Visit our website to schedule a meeting or call or email us.