
When searching the internet for HIPAA compliance solutions, you will find numerous options. However, most of these solutions focus on only one or two areas of HIPAA compliance, rather than offering comprehensive solutions. It is crucial to understand this distinction. To achieve full HIPAA compliance, you need to ensure compliance across all aspects.
While having HIPAA-compliant data storage or communication channels is beneficial, it does not guarantee total compliance. A single gap in your compliance measures could lead to a PHI breach and potential fines if audited by the Department of Health & Human Services (HHS). Individual compliance solutions often address specific aspects of HIPAA but may fall short of offering the full spectrum of protection needed to ensure complete compliance.
This blog provides a detailed overview of HIPAA compliance, why it is essential, and how to choose a comprehensive software solution to meet regulatory requirements.
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. law that sets data privacy and security standards for protecting medical information. The law has gained increased importance in recent years due to the rise in health data breaches resulting from cyberattacks and ransomware targeting health insurers and providers.
President Bill Clinton signed HIPAA into law on August 21,1996. It generally takes precedence over state laws concerning medical information security, except when a state law offers stricter protections than HIPAA.
The regulations your business must follow depend on its nature and classification as a Covered Entity, Business Associate, or subcontractor. Medical facilities that handle and share PHI are usually subject to various laws, such as:
The Healthcare Insurance Portability and Accountability Act. The Security Rule and subsequent amendments. The Security Rule and subsequent amendments. The Privacy Rule and subsequent amendments. The Security Rule and subsequent amendments. The HIPAA Enforcement Rule. The American Recovery and Reinvestment Act. The Health Information Technology for Economic and Clinical Health Act. The Omnibus Final Rule.
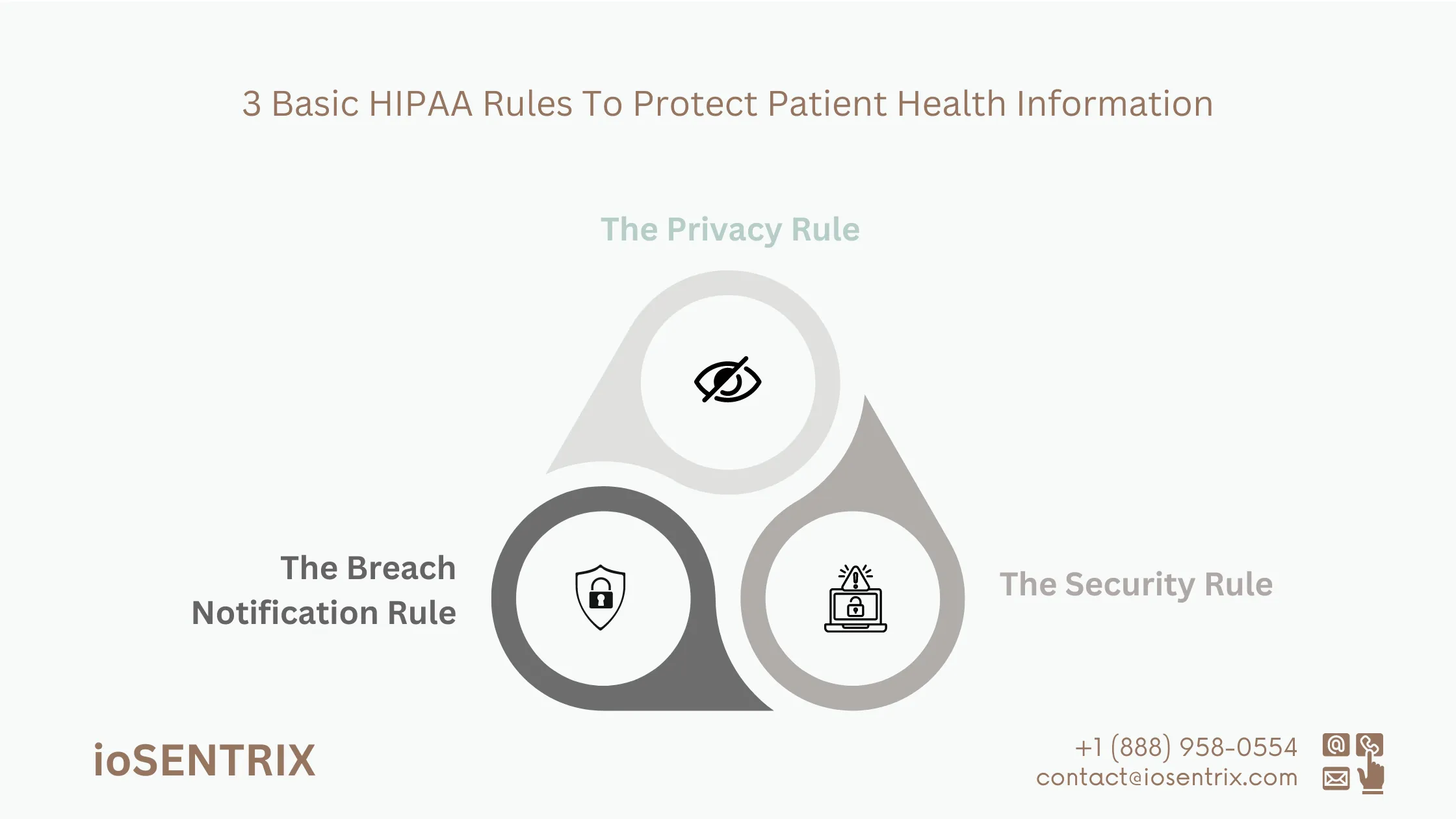
The HIPAA Privacy Rule explains a patient’s rights concerning their health information and controls who can view it. This rule applies not only to electronic data but also requires specific paperwork and consent forms to be completed by individuals managing PHI.
The HIPAA Security Rule sets guidelines on protecting electronic information when sharing or storing it. It focuses on using technical, administrative, and physical safeguards to prevent unauthorized access.
The Breach Notification Rule outlines what to do when there is a data breach. It emphasizes the importance of being prepared for potential hacks by having a plan in place. This rule specifies the process for informing affected individuals and the actions to mitigate harm.
Providing unique credentials to each user and having procedures in place for releasing or disclosing ePHI. Having policies and procedures to prevent unauthorized changes or destruction of ePHI. Using hardware, software, or procedural methods to track and review access and other ePHI-related activity. Implementing network security measures like encryption and firewalling.
Utilizing software for task management simplifies monitoring progress and setting deadlines for tasks. Having a HIPAA software solution makes it feasible for businesses of any size to comply with HIPAA regulations. This software acts as a project management tool to help meet all HIPAA requirements within a reasonable time frame. Despite numerous software options available for HIPAA compliance, not all of them cover everything necessary to adhere to the law. Therefore, what key features should you seek from your HIPAA compliance software provider?
A complete HIPAA compliance software package provides all the necessary tools to meet legal requirements. Trying to handle the various tasks needed for compliance without HIPAA software can be challenging and daunting.
Every year, healthcare businesses like covered entities, business associates, managed service providers (MSPs), and software providers need to do a security risk assessment (SRA). This helps find any gaps in your organization’s HIPAA safeguards. To follow HIPAA rules, you must fix any issues found during the assessment. Reliable HIPAA software can make this process smooth by showing you all compliance gaps in one place and guiding you on how to fix them.
Having HIPAA policies and procedures is crucial for a successful compliance program. Businesses must customize their policies and procedures according to their specific operations as mandated by HIPAA. Utilizing HIPAA software simplifies the process of implementing relevant policies and procedures for your business and also guarantees compliance with the HIPAA Privacy, Security, and Breach Notification Rules.

A HIPAA software solution allows you to manage and track all employee HIPAA and cybersecurity training in a centralized platform. The software also stores employee training confirmations and sends notifications for annual training sessions.
Managing your business associate vendors doesn’t need to be difficult or take up too much time. To ensure that any vendor who may access protected health information (PHI) follows the rules, they should sign a business associate agreement (BAA). Examples of such vendors include electronic health record platforms, email providers, appointment scheduling tools, teleconferencing services, and cloud storage providers. The HIPAA software ensures that all your business associate vendors sign a BAA and keeps track of them for you.
HIPAA mandates that any incidents involving the confidentiality, integrity, and availability of PHI must be reported. HIPAA software enables anonymous reporting of incidents and notifies administrators whenever an incident is reported.
ioSENTRIX offers a service for accessing your company’s internal resources from remote locations. Our solution adds a security layer to safeguard all endpoints containing sensitive information, ensuring secure access to your network, cloud tools, and databases.
Contact us today to see how our solutions can integrate with your existing processes to enhance compliance and secure sensitive information.