
Application security is critical in today’s software landscape. Following a comprehensive application security guide ensures your software is protected from vulnerabilities and cyber threats.
By combining secure coding practices, threat modeling, modern AppSec solutions, and best practices, organizations can strengthen their security posture.
With the increasing adoption of cloud-native environments, hybrid systems, and DevOps pipelines, integrating security into every stage of development is no longer optional.
Companies that implement these measures effectively reduce risks, prevent data breaches, and maintain user trust.
Application security concepts focus on protecting software applications from unauthorized access, data breaches, and potential exploits. It encompasses both preventive and reactive measures to reduce vulnerabilities and strengthen overall protection.
Organizations use a combination of secure coding practices, security testing, and automated tools to ensure that applications remain resilient against evolving cyber threats.
Adopting a proactive security strategy helps minimize risks before they escalate into costly incidents.
A fundamental aspect of application security is implementing secure coding practices. Developers play a critical role in ensuring the software they create is resilient to attacks.
This includes input validation, proper error handling, secure authentication, and safe configuration management.
Common practices include:
By following these practices consistently, organizations reduce the likelihood of vulnerabilities that attackers can exploit.
Threat modeling involves identifying, categorizing, and prioritizing potential threats to applications. Using this process, development teams can implement necessary controls and improve their application security posture.
Benefits of threat modeling include:
By integrating threat modeling into the software development lifecycle, organizations create a proactive approach to application security concepts.
Regular security testing ensures that applications remain protected. Tools like penetration testing, code reviews, and automated vulnerability scans help detect existing weaknesses.
Continuous evaluation enables organizations to stay ahead of emerging threats and address vulnerabilities before malicious actors exploit them. This is a cornerstone of any robust AppSec guide.
AppSec ensures software applications are protected from potential threats using security techniques, procedures, and best practices.
DevSecOps, on the other hand, integrates development, security, and operations for enhanced collaboration, transparency, and automation.
It’s important to note that simply combining AppSec practices with DevOps does not automatically create DevSecOps.
True DevSecOps involves embedding security deeply into development and operations pipelines, leveraging automation and collaborative processes to maintain security throughout the lifecycle.
SAST analyzes an application’s source code or binaries to identify vulnerabilities. By examining code logic, structure, and potential weaknesses, developers can address security flaws before deployment. SAST is essential for early-stage security assurance.
DAST scans live applications to identify runtime vulnerabilities and misconfigurations. It provides insights into an application’s security posture during operation, allowing organizations to remediate issues that arise in real-time.
MAST focuses on securing mobile apps against platform-specific threats. Mobile apps handle sensitive data and face unique risks, such as insecure data storage, weak authentication, and poor encryption.
MAST ensures mobile applications remain secure across different devices and OS versions.
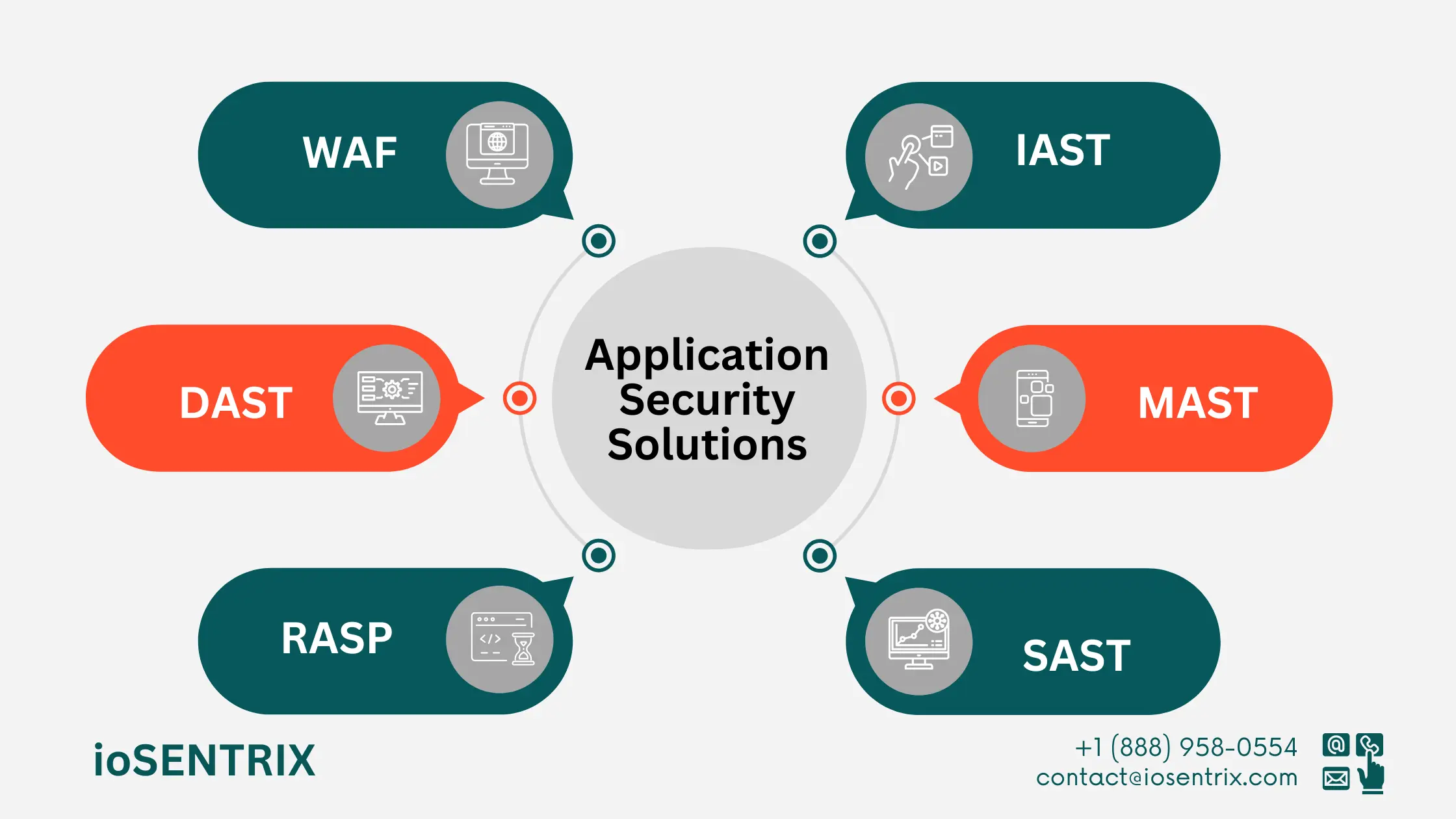
IAST combines SAST and DAST to provide real-time insights into application vulnerabilities. By monitoring application behavior, IAST identifies and mitigates risks efficiently, offering a comprehensive view of application security.
RASP proactively protects applications during runtime by monitoring and responding to threats instantaneously. It embeds security measures directly into applications, preventing attacks before they cause harm.
WAF acts as a shield between applications and potential attacks. By filtering malicious traffic and using behavior analysis, signature-based detection, and anomaly detection, WAF provides an additional layer of defense for web applications.
CNAPP (Comprehensive Network Application Security Process and Practices) offers a holistic approach to application security. It standardizes processes, practices, and controls, covering risk management, vulnerability assessment, secure coding, and incident response.
Cataloging all assets within an organization’s application ecosystem, hardware, software, and data, enhances visibility and strengthens overall security.
Incorporating security early in development ensures vulnerabilities are detected sooner. Automated security testing within CI/CD pipelines enables developers to fix issues without relying solely on security teams.

Evaluating attack vectors and existing security controls helps organizations understand potential weaknesses and implement improvements proactively.
Restricting access based on necessity minimizes risks. Least-privilege access prevents unauthorized access and reduces insider threats.
Security as Code automates security policy implementation, ensuring consistency, repeatability, and scalability. Organizations adopting DevOps and cloud-native approaches benefit from automated, codified security practices.
Zero Trust frameworks validate every access request continuously, providing stronger protection against advanced cyber threats than traditional perimeter-based models.
Following a structured application security guide ensures robust protection across software lifecycles.
ioSENTRIX provides tailored solutions that secure applications in hybrid and multi-cloud environments, enabling efficient, reliable, and secure operations.
Get in touch now to secure your applications with experienced professionals.
A guide provides a structured approach to protect applications from vulnerabilities, covering coding, testing, and monitoring best practices.
DevSecOps integrates security into development and operations pipelines, enabling continuous monitoring, automation, and collaboration.
SAST, DAST, MAST, IAST, RASP, and WAF are commonly used tools to identify and mitigate vulnerabilities at different stages.
It ensures security is considered early in the development lifecycle, allowing developers to detect and fix vulnerabilities before deployment.
CNAPP provides a comprehensive approach covering risk management, secure coding, and incident response, offering a holistic view of application security.