We live in a time where technological advancements are transforming the world. Companies are constantly creating innovative solutions that improve efficiency and simplify daily tasks for individuals globally.
However, it is essential to acknowledge the darker side of technology, the unethical practices of some individuals who disrupt progress by hacking and corrupting data.
A company's security must defend against cybercriminals' attacks, safeguard sensitive information, and shield it from potential financial and reputational harm.
This is where business penetration testing stages play a vital role.
Enterprise penetration testing, also known as pen testing, involves systematically testing an enterprise's IT network systems to identify vulnerabilities.
This process is akin to ethical hacking and helps detect weaknesses in the system's defenses.
Regular and thorough pentests help enterprise businesses stay prepared for security threats. Companies can prevent potential financial, legal, and safety consequences from security breaches caused by unauthorized hackers.
Imagine you are a credit rating agency holding a large amount of customer data. If this information falls into the wrong hands, it could harm your customers and your organization's reputation.
Cybercriminals could use this data for scams or phishing schemes. A security breach could result in a lack of confidence in your ability to safeguard customer interests.
Regular penetration tests can help you prepare for cyber-attacks, comply with cybersecurity regulations, keep your IT systems secure, and ensure your security experts are always vigilant.
This makes understanding the stages of penetration testing for businesses essential for long-term protection.
Various penetration tests can be carried out depending on the business size, focus, and objectives.
Here are a few popular types of penetration tests that are commonly performed for enterprises:
Also read: How to Report Phishing Emails?
A well-executed penetration test follows a structured approach. The penetration testing process for enterprises typically involves seven critical steps for comprehensive evaluation.
To begin, it is essential to:
This alignment between you and the testing team is necessary for smooth business operations while your system's defenses are evaluated.
Having a non-disclosure agreement (NDA) in place with your testers is advisable to safeguard sensitive information that may be accessed during the testing process.
The second phase is reconnaissance, which involves gathering key information. During this stage, testers utilize different techniques and resources to acquire insights into the organization's cybersecurity defenses.
This information may be obtained from open-source intelligence, in-depth company research, or even employee-related data.
When testing web applications, experienced testers may use spiders and crawlers from search engines to gather valuable target information. This step plays a major role in the steps of pentesting for businesses.
This stage evaluates weaknesses in the enterprise’s security system. It involves a detailed examination of the target network to uncover potential vulnerabilities.
The process concludes when risks like remote code execution and cross-site scripting are measured and documented.
Must Read: Vulnerability Assessment vs Penetration Testing
This is the main stage of the business penetration testing stages. Vulnerabilities found earlier are actively exploited to determine how well the system can withstand a malicious attack.
While it may not be feasible to exploit every weakness, the primary goal is to gain access to the system and analyze its resilience.
Each successful exploitation provides critical insights into the target environment.
This stage, also called lateral movement, involves testers maintaining access to evaluate long-term risks. IT security teams may attempt to reset or reboot systems, and testers analyze how resilient the infrastructure is during this phase.
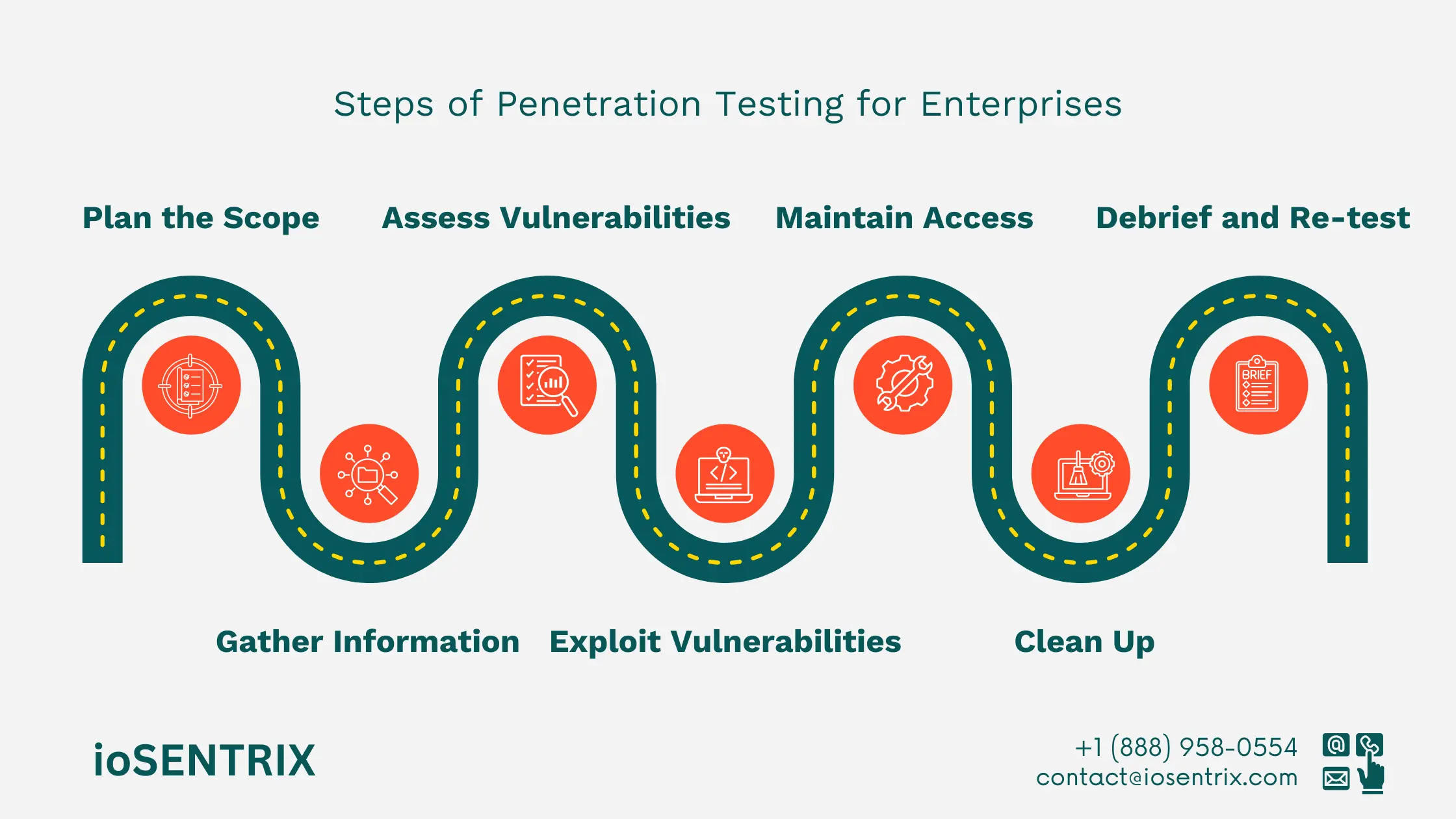
Cleanup, or artifact destruction, is essential. Testers remove all software, agents, and temporary files used during testing.
All configurations, including usernames and credentials, are restored to their original state, ensuring the system returns to its pre-test condition.
The final step of the penetration testing process for enterprises is sharing results and re-testing. Reports should clearly highlight vulnerabilities, exploitation methods, and recommendations for remediation.
After fixes are implemented, re-testing ensures vulnerabilities are properly resolved.
When conducting penetration tests, prioritizing information security management is essential. Since sensitive and critical data is involved, adhering to ethical and legal standards is non-negotiable.
Key guidelines include:
Ethical hackers must obtain proper authorization, respect data privacy, and avoid methods that may disrupt business operations.
Every business has unique characteristics, meaning its security requirements differ. Selecting the right penetration testing provider involves asking key questions:
Providers like ioSENTRIX specialize in the stages of penetration testing for businesses, aligning services with your organization’s needs.
We adhere to best practices to ensure enterprise-level protection. To learn more about our services, contact us today!