
Advanced Red Teaming, created by De Nederlandsche Bank, is a framework that focuses on threat intelligence. It provides a strategic analysis of how well you can withstand threats from actual malicious attackers and thoroughly assesses your defensive strengths.
Red teaming is more than just threat prevention; it also involves alerts, response, and evaluation detection. While blue teams in regular penetration tests know when the test will take place, red teaming tests challenge and measure how well blue teams can defend themselves and respond to real-world threats.
Unlike basic exercises, ART involves multi-phase operations (preparation, testing, and closure), with modules for organizational needs. It emphasizes collaboration between Red and Blue Teams through Purple Teaming for post-attack analysis and improvement.
Additionally, ART includes optional components like Gold Teaming for crisis readiness. It offers a more comprehensive and customizable approach to cybersecurity assessments.
Red Team: A "red team" is cybersecurity experts who mimic cyber attacks on a company's IT defenses. These professionals act like malicious hackers and use tools and methods cybercriminals often use to break into the organization's IT system.
Blue Team: The Blue Team within your organization is in charge of defending networks, systems, and applications. They are not informed about the Red Team simulation to enhance realism and evaluate their response capabilities.
Control Team: The Control Team serves as the bridge between the Red and Blue Teams. This group includes members from both our organization and yours. Additionally, the Managing Authority's representative (e.g., DNB or Z-CERT) attends all Control Team Meetings, though they are not considered a formal part of the team in technical or legal terms.
Purple Team: In Advanced Red Teaming, a key component is Purple Teaming, where the Red and Blue Teams gather post-simulation to analyze and gain insights from the attack.
Read more on: Red Team v/s Blue Team Security: The Essential Guide
Advanced Red Teaming uses up-to-date threat intelligence and is overseen by the appropriate governing body for each sector, like De Nederlandsche Bank or Z-CERT. In the healthcare sector, it is referred to as ZORRO.
Every Advanced Red Teaming project has these key elements:
Secrecy: The project within your organization is being kept confidential, with limited people being informed about it.
Live Systems: Red Teaming involves testing active systems to make the attack simulation more authentic.

Ethical Hacking: In one of the scenarios, ethical hacking is included as a part of the project.
Threat Intelligence: The situation should be informed by threat intelligence for analysis. Different sources such as threat intelligence feeds, dark web forums, publicly accessible reports, and tools help companies understand possible risks.
An Advanced Red Teaming project has three phases: preparation, testing, and closure. These phases include required modules but can also include additional optional modules. The Managing Authority acts as a neutral referee to oversee the processes and provide feedback on their feasibility.
In the initial stage of Advanced Red Teaming, your organization's Managing Authority (such as DNB or Z-CERT) and security provider are involved, but at separate times. Initially, you will work with the Managing Authority to define the scope and modules of your project. Following this, you will review and discuss this plan with our experts.
Threat Intelligence: Each ART project begins by gathering up-to-date threat intelligence (TI). The way this information is collected varies depending on the sector and requirements. Z-CERT supplies TI for the healthcare sector.
The TI report can be either basic or comprehensive, depending on the selected modules.
Threat-Led Attack: Next, we will proceed to the Red Teaming phase. Our team of Red Team experts will work closely with you to create scenarios that align with the identified threat intelligence and attempt to access sensitive information undetected by your cybersecurity team (Blue Team).
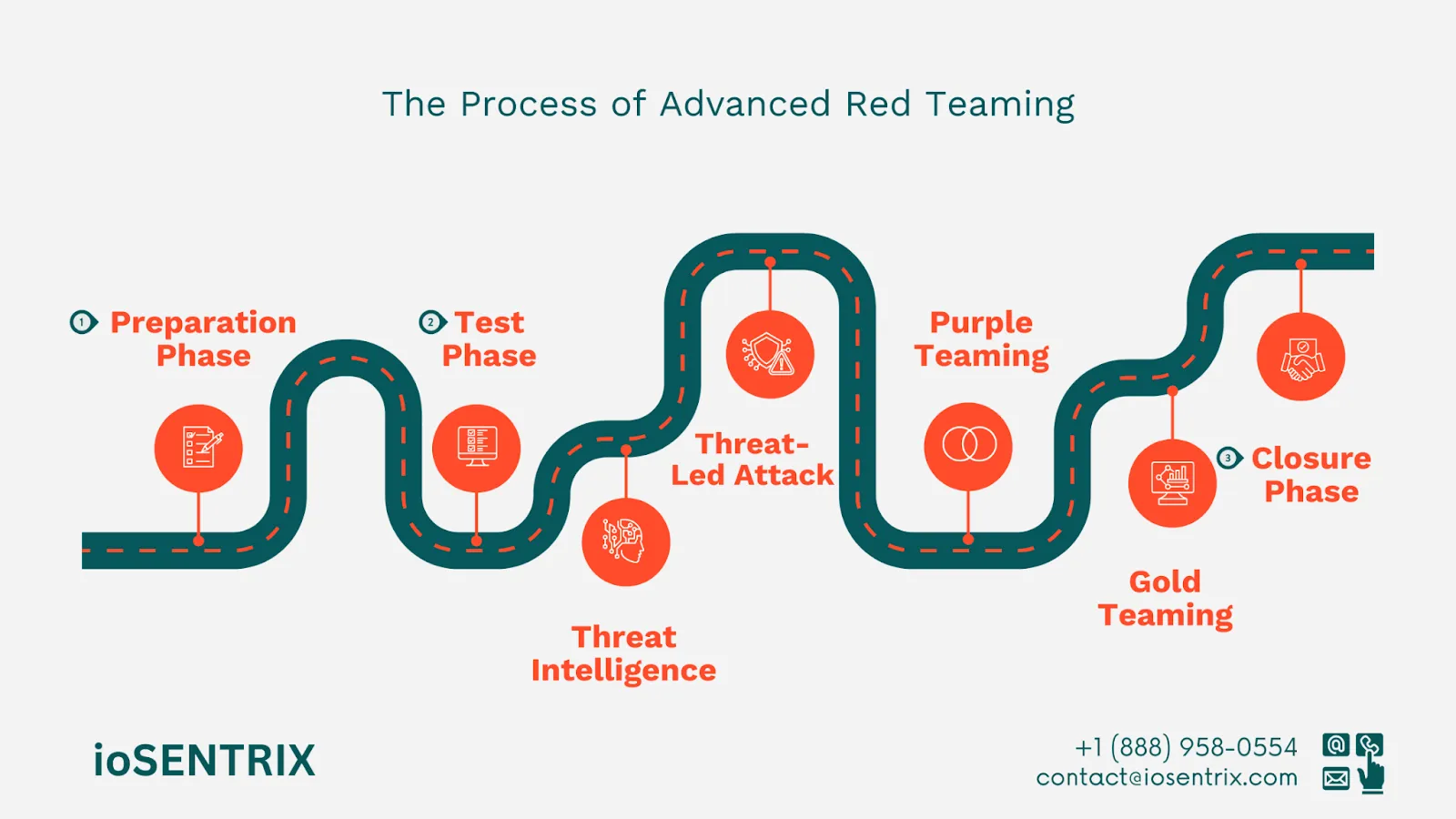
Purple Teaming: Following an attack, it's important to have a conversation with your defenders to review what worked well and identify areas for improvement. This joint effort between the Red and Blue Teams is referred to as Purple Teaming. Every ART project includes a basic Purple Teaming component. As the assessment nears completion, the Managing Authority will evaluate if the basics are sufficient or if additional Purple Teaming is necessary.
Gold Teaming (Optional): You can utilize the results of the Red Teaming exercise to prepare your crisis teams through a process known as Gold Teaming. It involves using the findings to develop training tools such as Walkthroughs, Tabletop exercises, or full Simulations for your crisis teams.
This stage involves handling the remaining digital evidence of the attacks along with planning for remediation. What steps should be taken for follow-up after an attack?
Advanced Red Teaming, also known as ART, is an extension of the Threat-Intelligence Based Ethical Red Teaming (TIBER) framework introduced in 2016. TIBER assesses the cybersecurity of financial systems such as banks and payment institutions.
ART and TIBER have several key distinctions between them:
A red team exercise is a highly advanced security assessment an organization can conduct to replicate the latest targeted attacks by real adversaries. These exercises help assess your business's current risk level, identify areas for improvement, increase resilience, and offer a greater level of assurance.
Advanced Intrusion Exercise (AIE): The AIE conducts thorough analyses of potential threats from targeted attackers, using a mix of social engineering, physical intrusion, and typical cyber-attack methods.
This approach in breach simulation is carried out by experienced security experts. The AIE can simulate various threats to deal with a wide range of client requirements based on their business type.
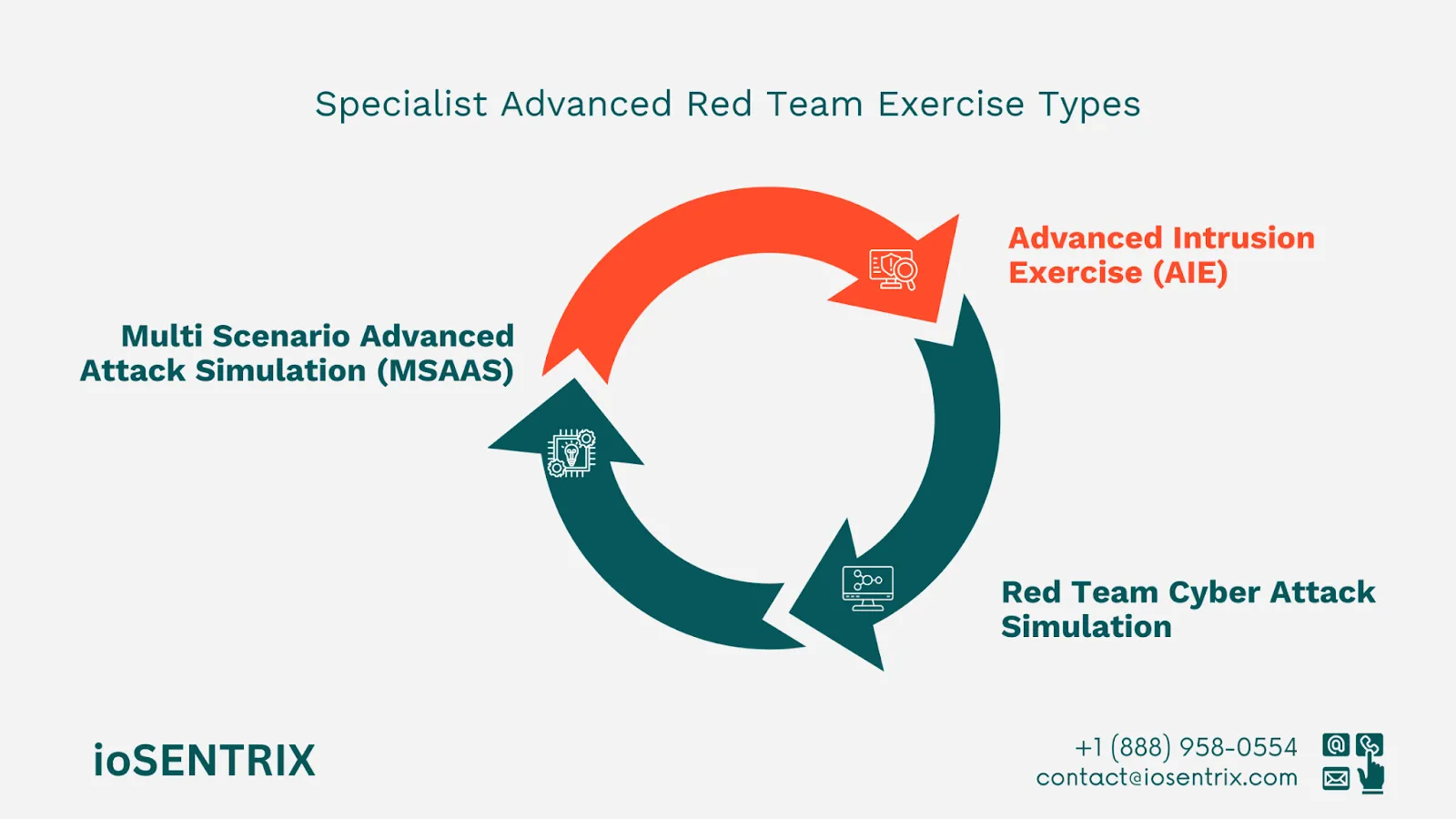
Multi Scenario Advanced Attack Simulation (MSAAS): Highly favored by FTSE250 companies, this program takes place over an extended period (such as 6-9 months) for a stealthier, APT-like method resembling actual cyber threats, rather than the usual time-limited exercises.
The MSAAS service offers organizations a chance to assess how well they can protect themselves from real-world dangers realistically.
Red Team Cyber Attack Simulation: This includes tactics like network implants, spear-phishing, and other internet-based attacks. The objective is to move laterally through the network to access important assets and potentially steal data.
Evaluating the strength of security measures, the accuracy of notifications, and the efficiency of response strategies are crucial in this process.
The key strength of a Red Team engagement lies in its team collaboration. The most effective engagements involve a combination of technology, tools, and skilled human operators. This approach helps to assess the potential risks of security measures within an organization.
When considering automation, it is common to think about eliminating simple tasks carried out by people. However, automation can offer significant benefits. Instead of thinking of it solely as automation, it may be more helpful to see it as augmentation.
This can be likened to enhancing a team with advanced technology, like enabling a Red Team with capabilities such as speed, strength, and improved efficiency in running multiple tasks simultaneously.
Certain Red Team operations that are commonly used and offer great benefits from automation are:
Asset Discovery: Analyzing all the systems, networks, and applications that make up the organization's potential vulnerabilities, along with the connections that could be exploited to achieve specific objectives.
OSINT Gathering: Searches for external information about systems, business processes, partners, and even personal details about executives and employees. This information can be used to deceive or exploit others.
Ransomware Attack Simulation: At the most advanced level of Red Team tasks, experts safely simulate the impact of a genuine cyber attack to improve preparedness and response strategies.
Artificial Intelligence has the potential to introduce Jarvis into the process. AI is not just for conversation; it also helps to reduce the time for the Red Team to simulate attacks effectively.
Although AI use in Red Team activities is not widespread yet, criminals are already tapping into its capabilities to enhance their deceptive tactics. Their ultimate aim is to maximize opportunities and returns on investment in their illicit attacks.
Where is AI located in the Red Team playbook right now? The main ways AI is used in Red Team operations are:
In the coming years, people will continue to play an important role in analyzing, prioritizing, and executing cyber attacks. However, it is possible to imagine a future where AI technology becomes more involved in these processes, including:
A hacker utilizes a wide range of tools to exploit various areas of your digital, technological, physical, and human security to reach your most valuable assets. Replicating such an attack requires a skilled group of hackers and social engineers with in-depth understanding, diverse expertise, and many talents.
Our team has developed these capabilities and skills over the years. We have completed Red Teaming projects with a focus on conducting complex simulations. Our team has expertise in three key security areas: technology, physical security, and human behavior.
To learn more about our team expertise, contact us today!